Colangelo's Sock Puppets? Open Source Sleuthing Methods in Recent NBA Scandal
On May 29, The Ringer published an investigation into five Twitter accounts that had apparent links to Bryan Colangelo, the President of Basketball Operations of the NBA’s Philadelphia 76ers. Colangelo has since confirmed that he does operate one of these accounts — @phila1234567 — but is apparently only used for monitoring news, and does not tweet. The other four accounts — @AlVic40117560 (“Eric jr”), @Honesta34197118 (“HonestAbe”), @Enoughunkownso1 (“Enoughunkownsources”), and @s_bonhams (“Still Balling”) — tweeted about the Philadelphia 76ers and a range of other subjects of interest to Colangelo, such as the Toronto Raptors (where he previously worked), the University of Chicago men’s basketball (where his son is a member of the team), and, of course, ardently defended the decisions made by Bryan Colangelo.
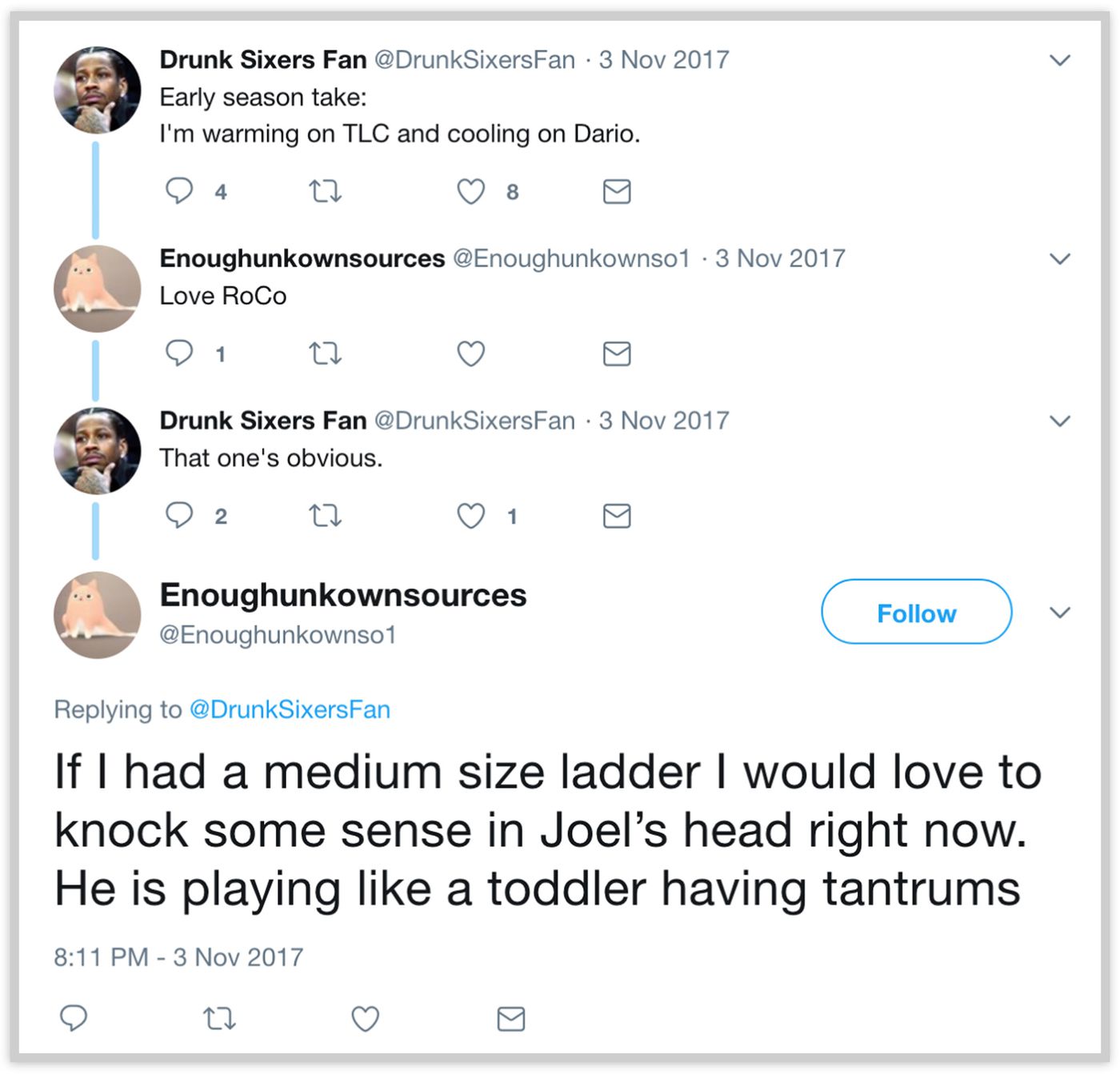
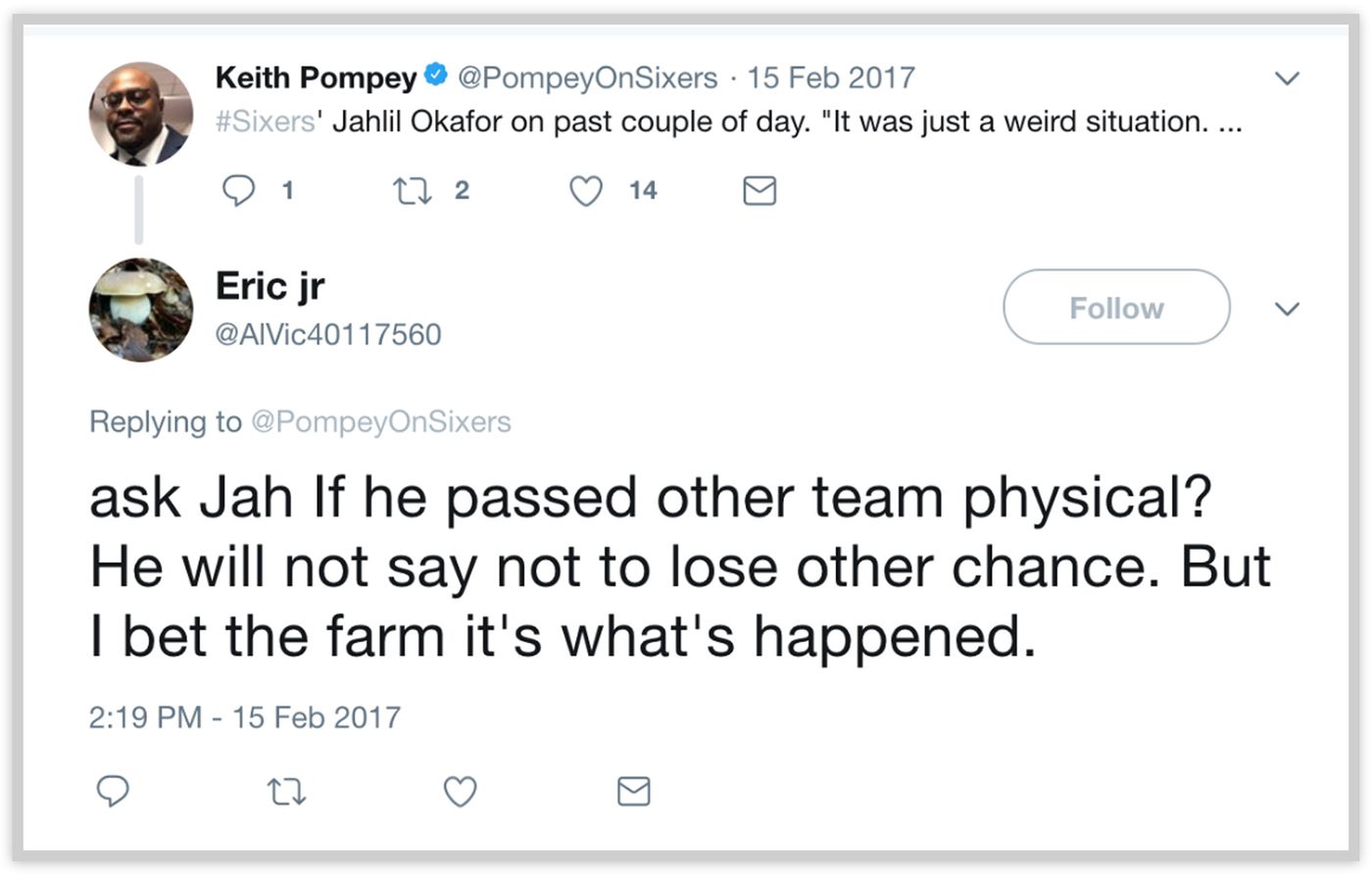
The fact that a well-known NBA player or front office official runs secret “burner accounts” on Twitter is not entirely surprising, as seen in last year’s revelation of how Kevin Durant operates alternate Twitter accounts to defend himself against online detractors. This case, however, has become a legitimate scandal because the tweets written by the accounts linked to Colangelo (and more likely, as has become apparent since The Ringer published its investigation, Colangelo’s wife) publicly and crudely criticized former and current players on the 76ers roster, most notably star center Joel Embiid and last year’s #1 draft pick Markelle Fultz. Additionally, the account possibly revealed non-public medical information in the form of a failed physical from former 76ers center Jahlil (“Jah”) Okafor.
While digging through the tweets of a basketball executive’s secret accounts is not quite as serious of a task as identifying the perpetrators of downing a passenger plane or analyzing chemical weapons remnants, many of the basic investigative methodologies are the same. In this case study, we will examine some of the sleuthing methodologies done by Ben Detrick and The Ringer and others who have followed up on their original research.
Nexus Accounts
One of the simplest methods of establishing the owner of an account — or, for the more conspiracy-minded, the person that is meant to appear to be the owner of an account — is by closely examining the account’s follows and followers. While this method cannot be universally applied, we can often identify obscure Twitter users that an account interacts with through its likes or follows. Perhaps most famously, Ashley Feinberg (formerly of Gawker/Gizmodo, now with the Huffington Post) identified the secret Twitter account of former FBI Director James Comey by following a few clues publicly given by Comey along with tracking the relatively small Twitter and Instagram accounts of Comey’s family. After following deactivated Twitter accounts and random mentions on Twitter, Feinberg found the Instagram account of Comey’s son, which was connected to Comey’s Instagram, which eventually led to his Twitter account.
The same practice was applied for the five accounts linked to Colangelo. Four of the five accounts were set to private soon after The Ringer sent an inquiry to the Philadelphia 76ers (crucially, The Ringer only asked about two accounts, with the other three being set to private immediately after the inquiry), but the “Eric jr” (@AlVic40117560) account remains open for the public to see. Thankfully, The Ringer has meticulously taken screenshots of the activity of these now-private accounts.
Much like how James Comey’s son followed his father’s relatively obscure account, the accounts followed by the Colangelo-linked accounts shed light on their operator(s). The “Still Balling” account (@s_bonhams), for example, followed accounts that include “several of his son’s college basketball teammates, a former coach from his son’s high school, and an account that shares the same name as the agent Warren LeGarie, who has represented Colangelo in the past.“Colangelo’s son’s college basketball team, it should be noted, is the University of Chicago, a tiny program that has had little to no success in the past decade and with an arena that seats fewer than 2,000 attendees. The “Eric jr” account was also a vocal supporter of the University of Chicago’s men’s basketball team, even live tweeting their games (thus excluding Colangelo’s son as a “suspect” in operating these accounts):
Play defense guys! Please – some effort
— Eric jr (@AlVic40117560) February 5, 2017
The FollowerWonk tool can be used to compare the follows and followed users of two or three different accounts.
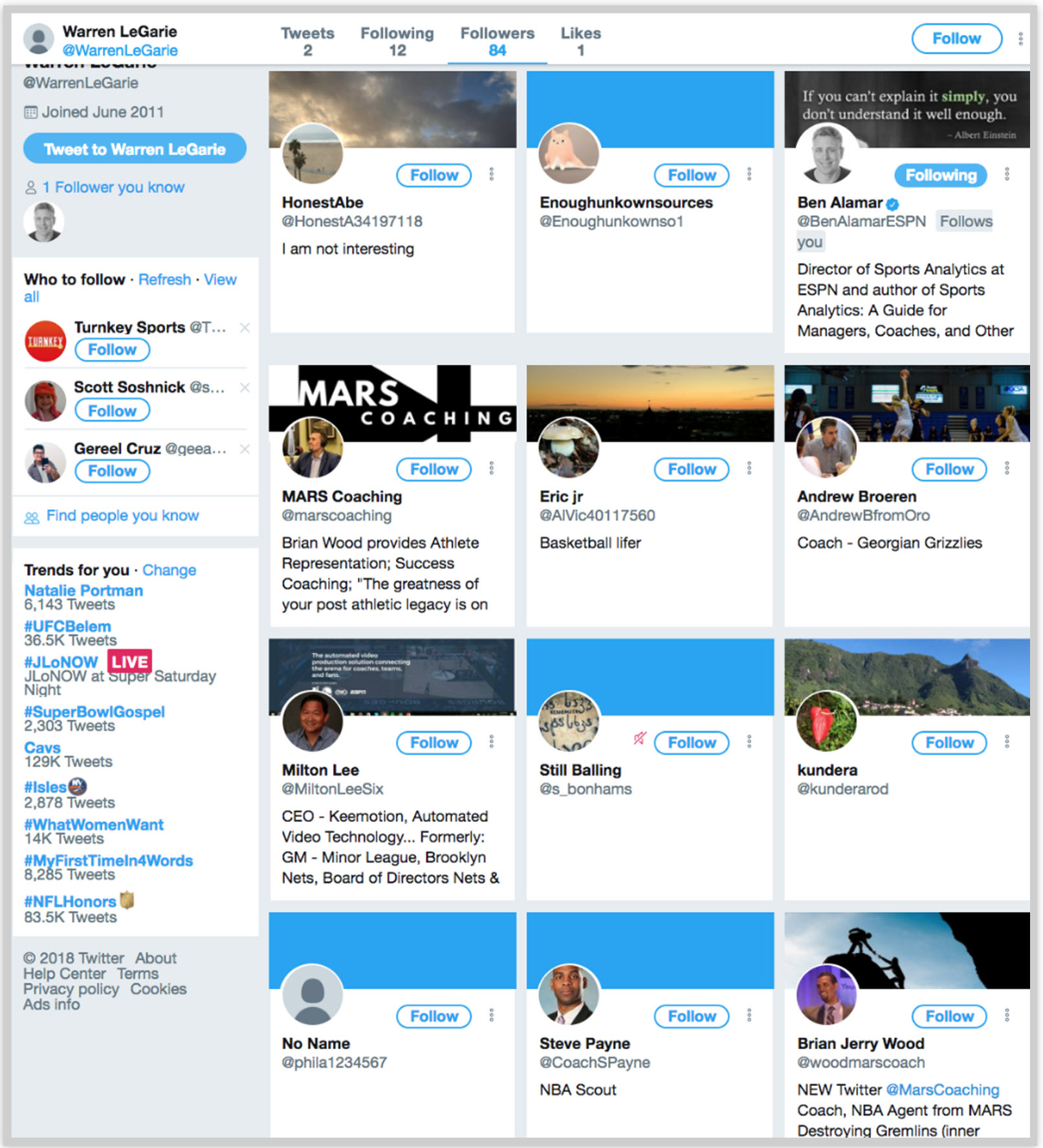
Another nexus linking all of the suspected accounts together is the user @WarrenLeGarie–the account of Colangelo’s former agent, who has only tweeted twice and follows a dozen users. Of these 84 users who followed LeGarie before The Ringer published its investigations, five are the Colangelo-linked accounts under question.
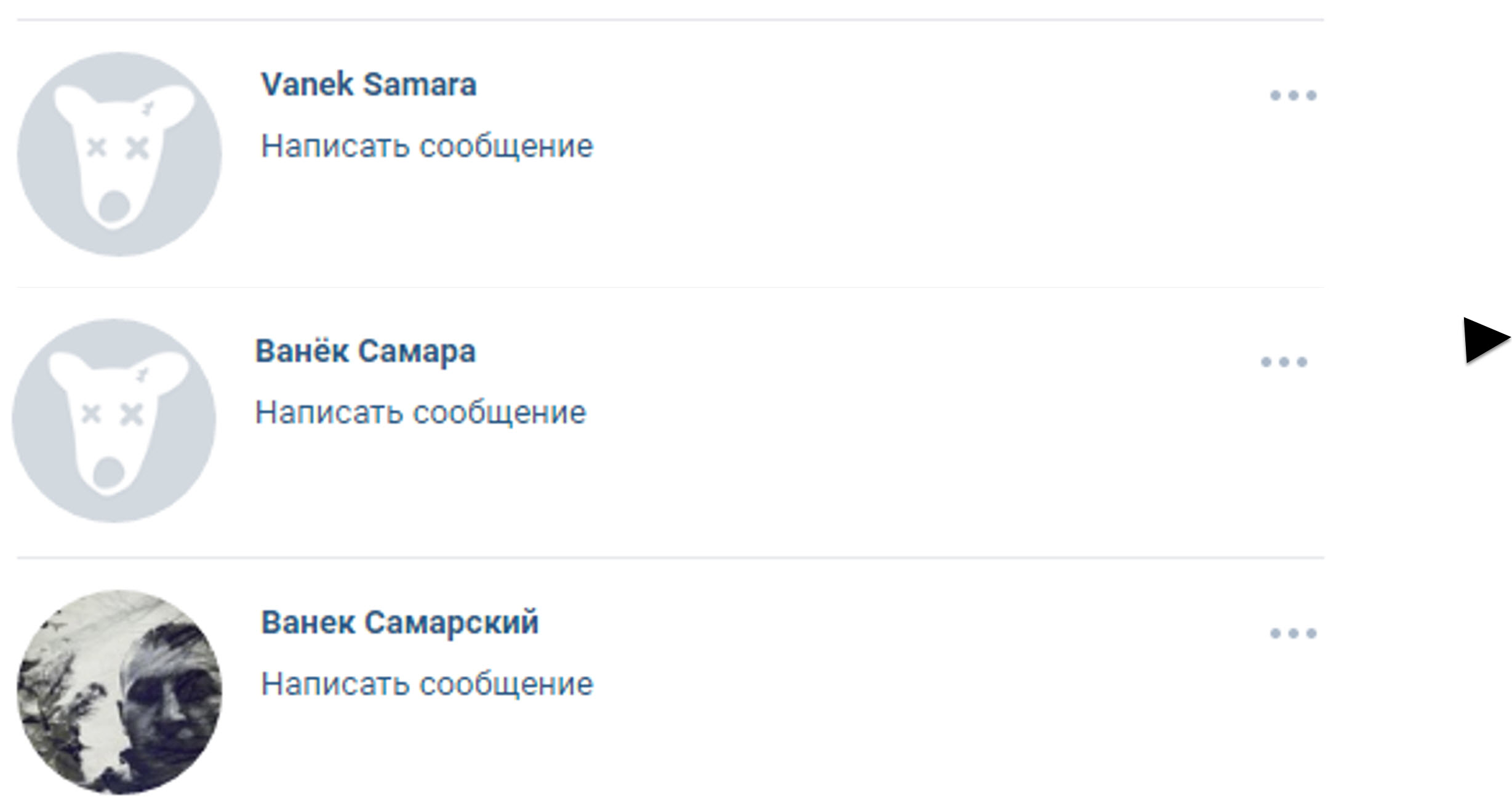
These “nexus accounts” are often valuable in discovering multiple accounts ran by the same person, as users often add the same people to their friends or follow list after making multiple accounts. For example, a separatist in eastern Ukraine who Bellingcat researched in relation to the downing of MH17 added his sister and wife on the popular Russian social networking site Vkontakte with each of his profiles. This separatist fighter would frequently cycle through accounts with similar usernames, but one of the few common links with all of them is that he added his sister and wife as a friend immediately after account creation. Below, three accounts of “Vanek Samarsky” (real name Ivan Krivobedry), two of which are now deleted, are present in the friend list of his wife and sister.
Email and Phone Password Recovery
After The Ringer published its investigation, one of the first steps taken by 76ers fans following up on research was to run password recovery on the five Twitter accounts under question. Tricking Twitter into thinking that you are an account owner who lost his or her password by using the Password Reset page will reveal a snippet of information about the information provided upon account registration, including a snippet of the registered email address and phone number. This process revealed that three of the accounts under question (“Still Balling”, “Eric jr”, “Enoughunkownsources”) had a phone number that ended in “91”, one (@phila1234567, which Colangelo admitted to operating) had a phone number that ended in “75”, and three used different Gmail addresses (starting with “di”, “no”, and “bp”).
Can anyone corroborate this? pic.twitter.com/qmsMm4B9Fn
— The Guy from TV's Burn Notice (@OhWowHmm) May 30, 2018
Ok 3 of the 5 use the 91 number pic.twitter.com/rM54cV8FFO
— The Guy from TV's Burn Notice (@OhWowHmm) May 30, 2018
The confirmed one uses a different number and email pic.twitter.com/n96sl9luMf
— The Guy from TV's Burn Notice (@OhWowHmm) May 30, 2018
The @phila1234567 account matches the personal information of Bryan Colangelo, including his email address (bpcolangelo@gmail.com) and his phone number (which ends in “75”, as confirmed by a number of reporters). In the most interesting twist yet to the story, some open source sleuthing revealed that Bryan Colangelo’s wife has a phone number that ends in “91”, possibly linking her to the Twitter accounts that tweeted the controversial information that has sparked a scandal. The only account with information directly linked to Colangelo was only used for monitoring news. For this step, 76ers fans used Gmail’s password recovery feature, which also reveals the final two digits in a phone number, along with a separate public page listing her phone number.
?????
Colangelo’s wife, Barbara Bottini has a phone number ending in 91, almost certainly linking her to 3 of the burner accounts.
WOW. pic.twitter.com/PQpe5GccEh
— Did the Sixers win? (@DidTheSixersWin) May 31, 2018
The official 76ers team investigation into the ongoing scandal has focused in on Colangelo’s wife, per ESPN. The recent findings of the owner of a “-91” telephone number seem to corroborate this investigative trajectory.
Researching Protected Accounts
While the journalists at The Ringer had full access to accounts that are now locked down to private, there are still some limited ways for those of us without this access to research private accounts on Twitter.
When a Twitter account is made private, only users who follow that account can read its tweets. A user who is followed by a private account — but does not follow it back — cannot see its tweets, even if they are directly mentioned (by tweeting “@username“) by the private user.
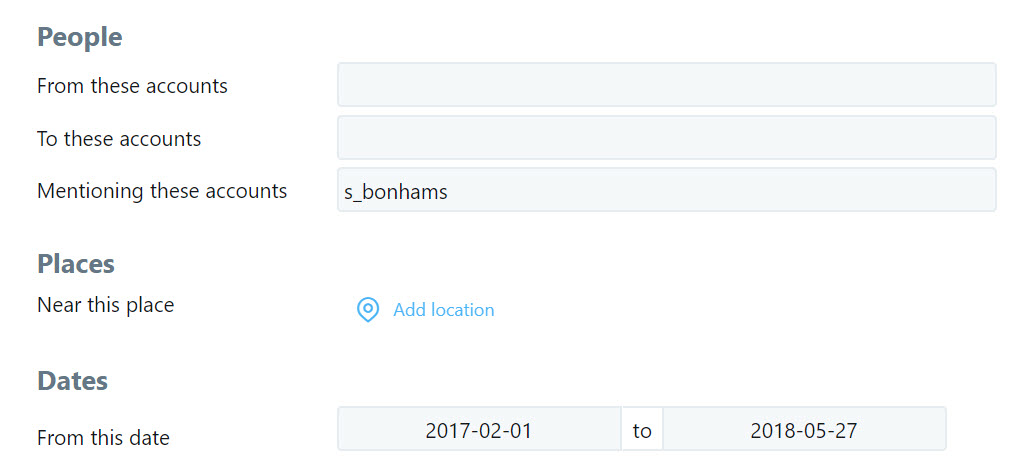
One laborious way to determine the accounts that a private user follows and is followed by, TweetBeaver has a mutual follower tool, which shows (one comparison at a time) the mutual or un-mutual followers of a private account. For example, in the case of “Still Balling” (@s_bonhams), TweetBeaver shows us that the account follows @BillSimmons, but not the other way around.
While we cannot directly access tweets from a private account on Twitter, we can observe tweets directed towards the user, often giving a clue at what is being discussed. From Twitter’s Advanced Search page, we can search for all tweets mentioning or sent to the now-protected “Still Balling” (@s_bonhams) account from its account creation (February 2017) to a few days before The Ringer published its investigation, providing these results. The same search can be done by typing @s_bonhams since:2017-02-01 until:2018-05-27 in Twitter’s search bar in the top-right of the user interface.
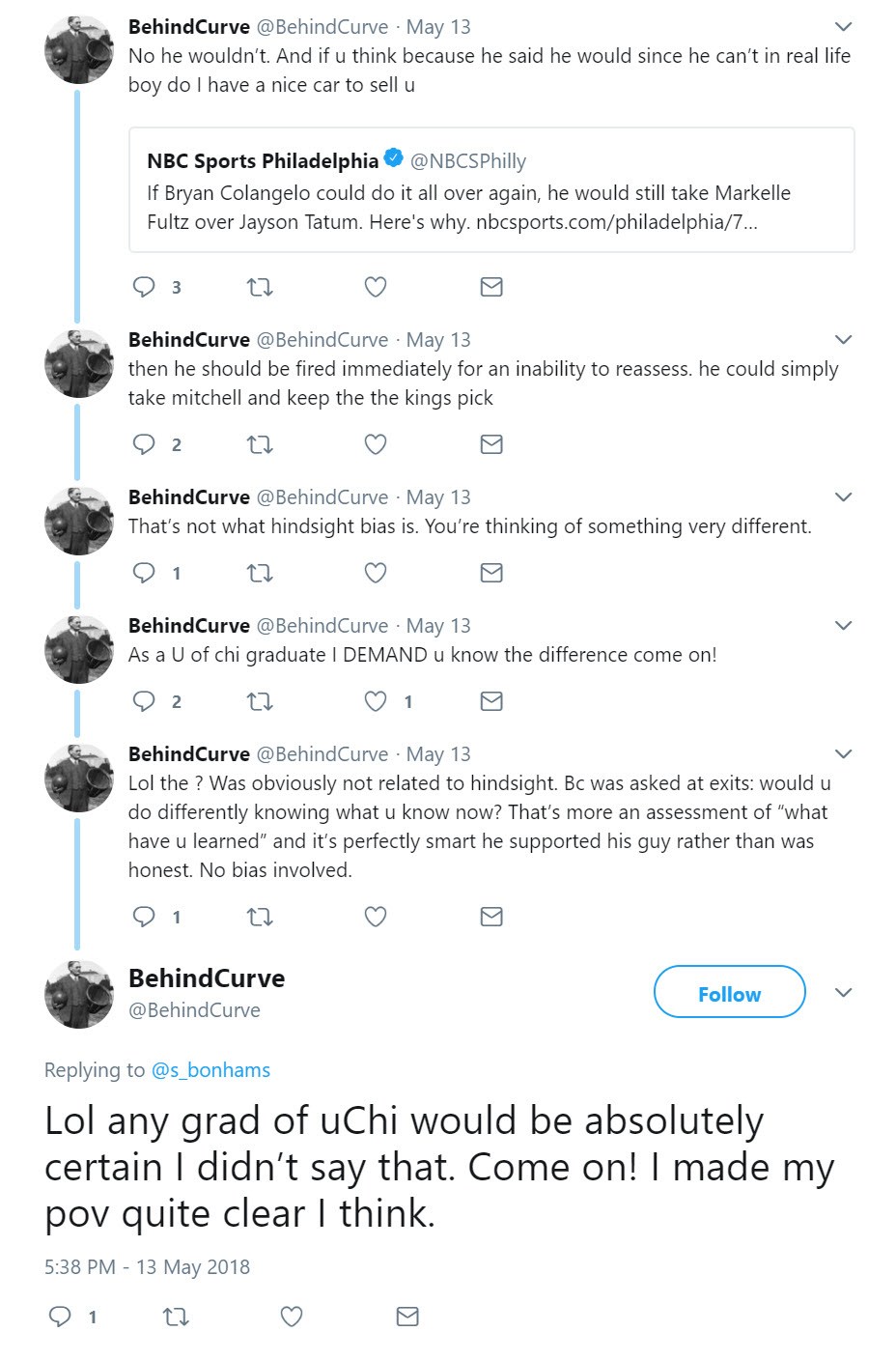
While the tweets from @s_bonhams / “Still Balling” are hidden from our view, we can still see the subject of the conversation in most cases. For example, in this series of tweets, it is clear that the account linked to Colangelo (or, more accurately, Colangelo’s wife) is speaking about decisions made by Bryan Colangelo and about the University of Chicago (“U of Chi”), where Colangelo’s son plays basketball.
Other solutions for finding tweets by protected users is searching usernames on search engines that have cached pages (such as Google, Yandex, and Bing) in hopes that a cached page exists with tweets. Additionally, the two most popular online archiving sites — web.archive.org and archive.today — can provide saved tweets from before a page was made private. Unfortunately, The Ringer did not save the pages of the now-private users on either of these archiving sites, as the oldest archived page for “Still Balling” is from after the story was published. For more information on how to use and access online archiving sites, see Bellingcat’s guide from earlier this year.
Lessons learned
Other than causing significant embarrassment for Bryan Colangelo, his family, and the Philadelphia 76ers, The Ringer‘s recent investigation also shows how much information is hiding in open sources, with only a few nudges necessary to find vital correlations. The majority of people are not familiar with techniques used by online sleuths, whether they be dedicated Reddit internet detectives or professional background investigators, and are thus vulnerable to accidentally revealing too much information. We have seen this not just with high-profile cases of FBI Directors and NBA personnel, but also young Russian soldiers in Ukraine, ISIS supporters in Europe, Ukrainian wives of corrupt officials, and American soldiers wearing FitBits on bases in foreign countries.
Nathan Patin provided additional research and editing in this case study.