Uncovering A Pro-Chinese Government Information Operation On Twitter and Facebook: Analysis Of The #MilesGuo Bot Network
An ongoing information operation is using a network of bots made up of newly created and stolen accounts to target a businessman, exiled from China, who has spoken critically of China’s response to COVID-19.
Yet identifying the network has revealed a much larger operation amplifying content across multiple languages, platforms, countries, and topics, with links to information operations against protests in Hong Kong, as well as involving cryptocurrency, coronavirus disinformation, and the most significant of all, the long-standing targeting of Guo Wengui, an exiled Chinese businessman residing in the United States.
Over a period of nine days, I captured data from Twitter, both in real-time and past, and conducted an ongoing analysis of the dataset as it grew. This report will show the initial findings from the dataset.
The findings indicate that there is a well-structured information campaign displaying a number of criteria similar to those of past campaigns identified as “significant state-backed information operations” originating from within the People’s Republic of China (PRC) in a disclosure report by Twitter in August 2019.
This report does not focus on the veracity of the targets of the information operation, nor does it seek to discredit or support the claims presented herein. The analysis is on the structure and operations of the network alone.
Methodology: Capturing Data And Conducting The Analysis
The dataset was made by capturing activity from Twitter over a period from 25 April – 3 May, 2020. I captured data that was based on two hashtags that were present in many of the tweets:
- #郭文贵
- #milesguo
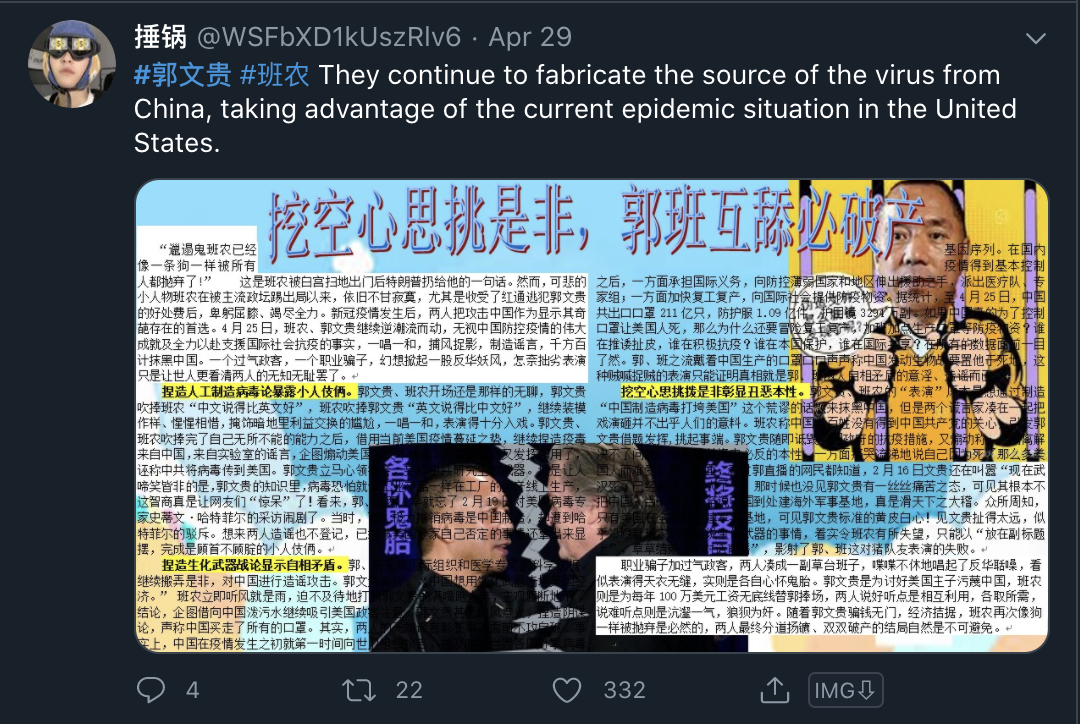
Here is an example of the content and style of the tweets:
The data around these hashtags was captured in real-time using the open source platform Gephi, and historical data was also captured for accounts and tags using the Python tool Twint.
The data that was captured consisted of tweets, retweets, likes, comments, and mentions.
In total, more than 2500 accounts were collected, which forms the basis of this analysis.
While the dataset is large enough to identify trends, there is the limitation of time, location, account history, and details only Twitter is privy to.
Given more time spent capturing this data in the same manner, or given a chance that Twitter would publish account details in its regular transparency reports, a more complete picture of the network could be analysed.
However, the following evidence is what is present in this existing dataset, and it is already very interesting.
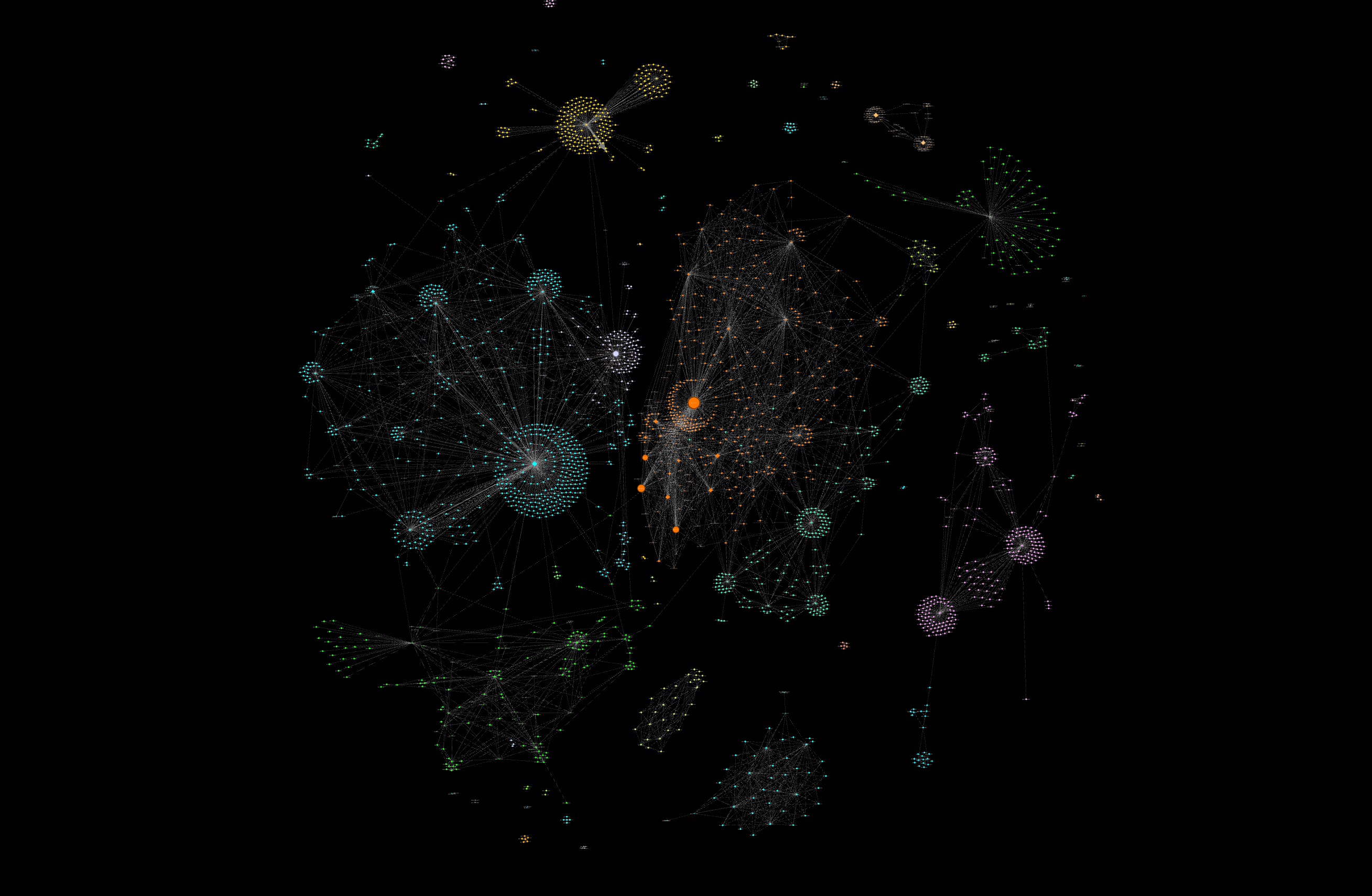
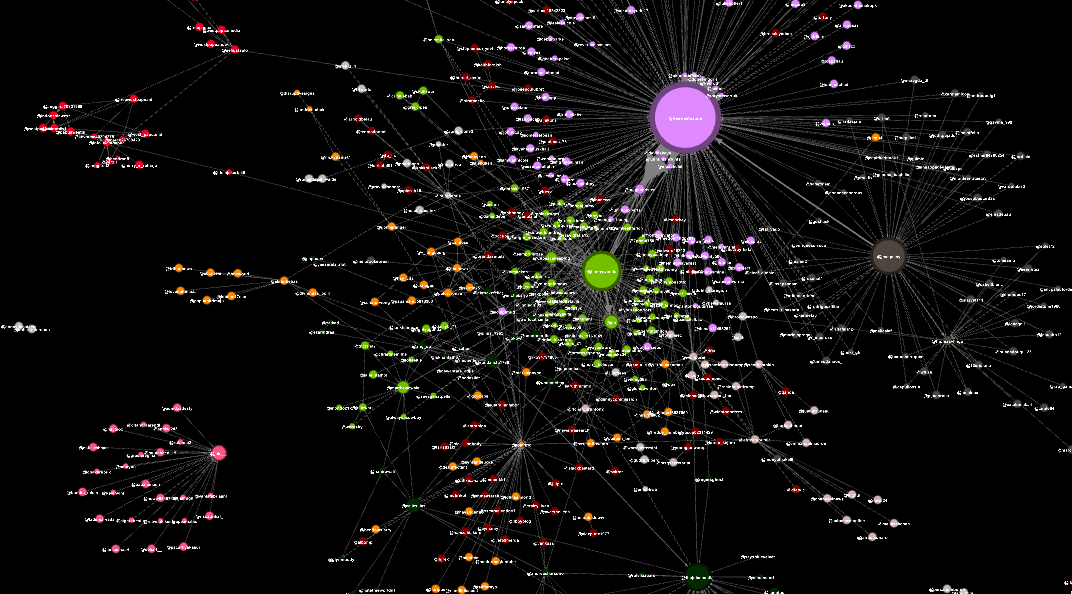
Visualising The Network: The Modularity Graph
The data captured was visualised in Gephi. Using both modularity and hit detections automatically categorised the accounts into modularity classes and allowed for clusters to be formed based on their interractions in the network. You can see these clusters in the overview below.
In the visualisation above there are two important features present:
- The coloured dots, which are referred to as nodes’ signify individual Twitter accounts
- The lines between them, which are referred to as edges, are the interactions between the accounts
Of the 2504 accounts, there were 8714 edges, or interactions in a directed graph format.
Structure Of The Network: “The Great Retweet”
This network operates in a structured manner to ensure brand new accounts with zero followers and zero accounts following are able to post one tweet and have that tweet magnified with, on average, between 200 and 1000 likes and retweets.
This can be seen in the image above. The red boxes included are clusters that operate within this network to post and amplify the campaign’s agenda.
This is a sustainable and effective model for the network — when it suffers account closures and mass deletions, it can simply create new accounts to re-support that model.
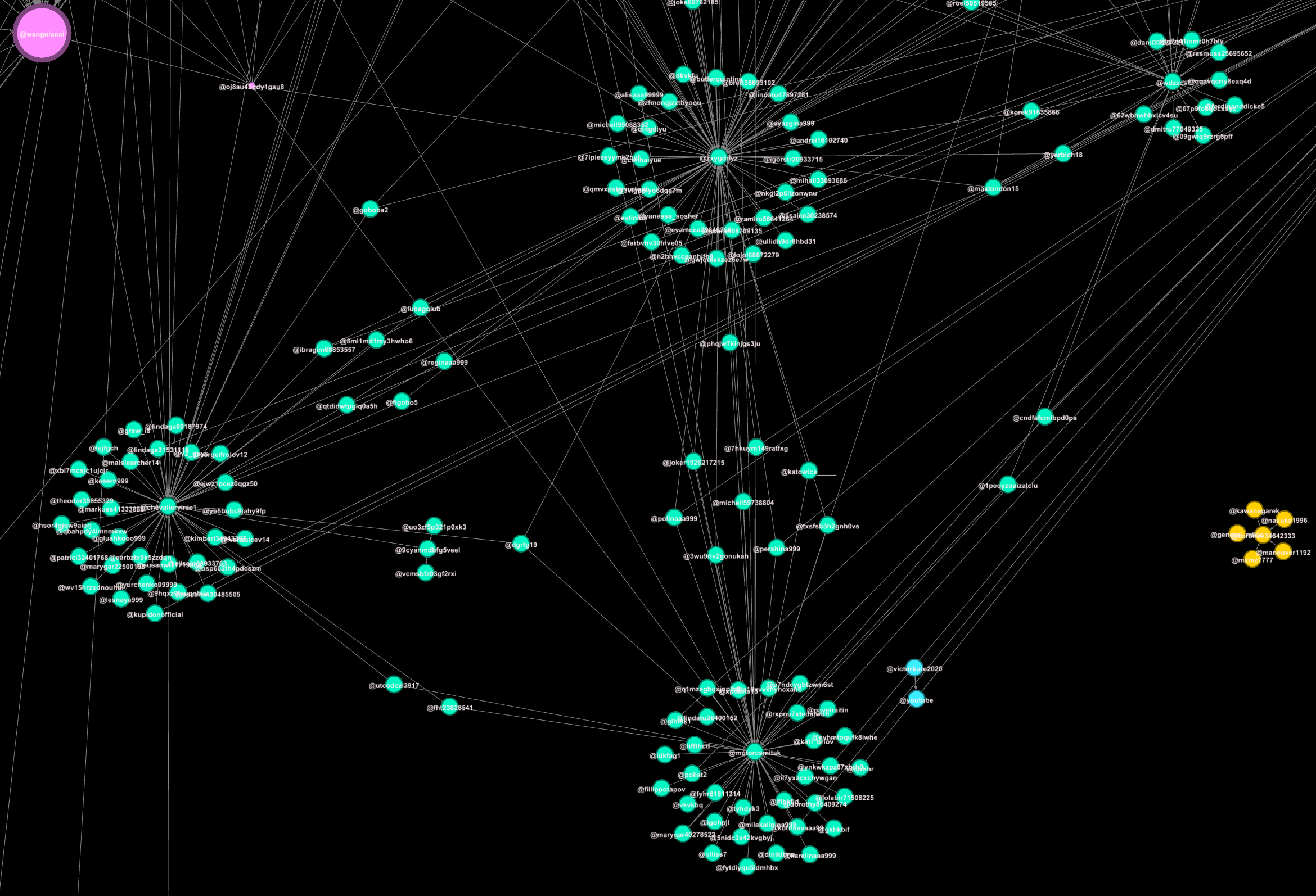
To carry out that task, the network consists of two limbs: posters and amplifiers. Each has their function in the chain of operations. This can be seen in the image below, which shows central accounts that would have posted content, and the surrounding accounts that retweeted it.
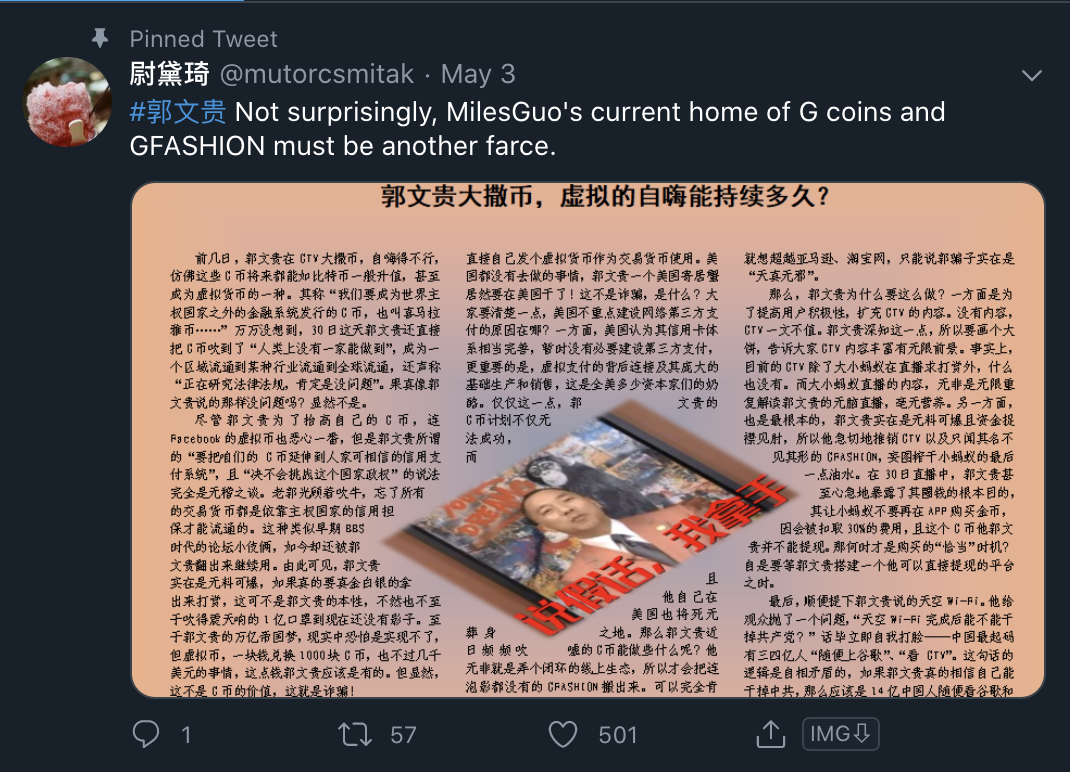
First, I will use the example of account mutorcsmitak. It operates as a poster. It has 10 people following, and 4 followers.
Below is an example of a tweet it posted that is critical of Guo Wengui.
The likes and retweets are unnaturally high for an account of this nature.
However, it is not the only account posting content like this. Many other accounts with very few followers — yet with exceptionally high retweet and like ratios — are posting this content.
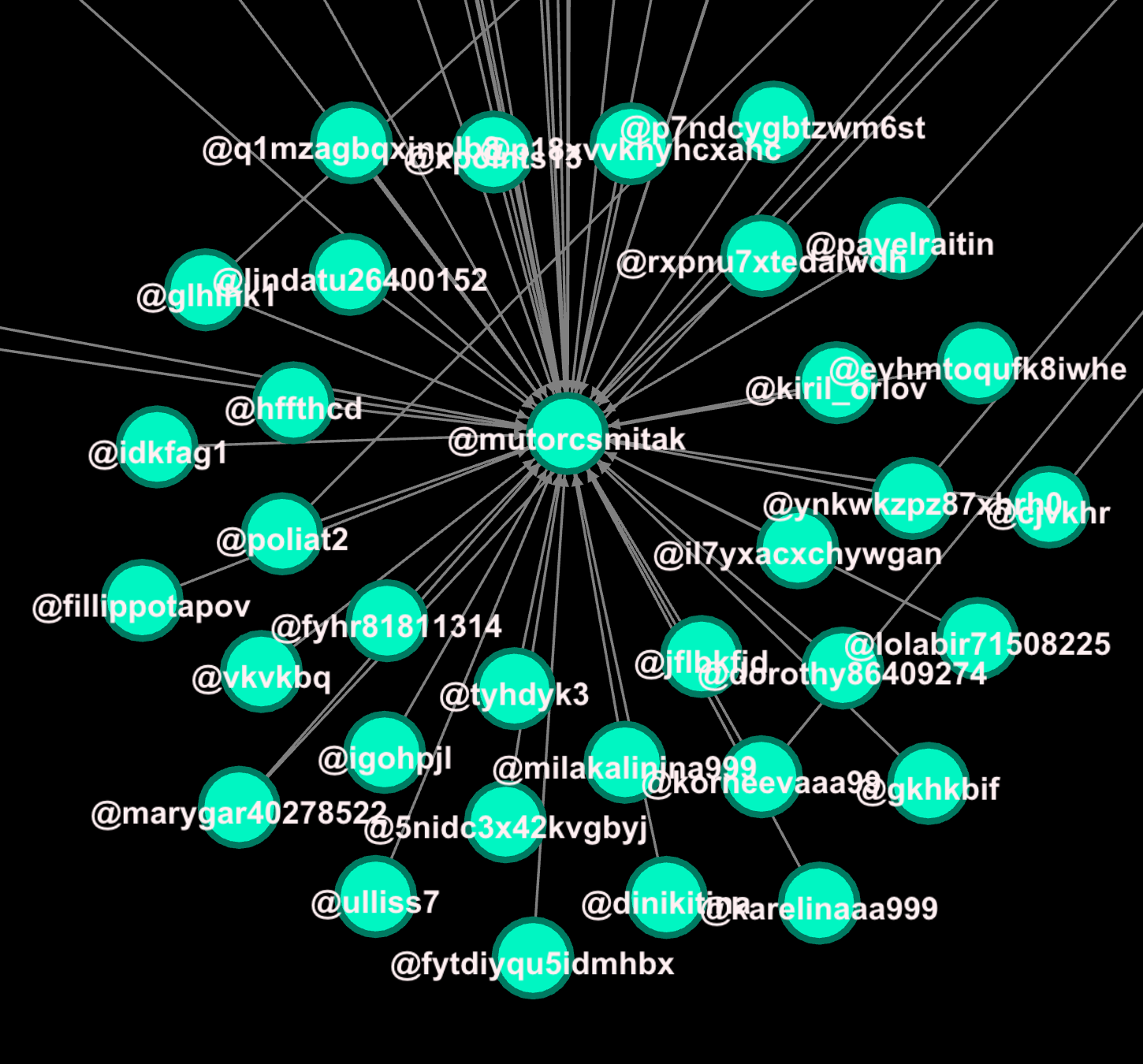
In the data visualisation, we can see mutorcsmitak’s amplifier network, with the accounts surrounding mutorcsmitak, seen below.
The network accounts surrounding mutorcsmitak are the amplifiers of mutorcsmitak’s content, as well as other poster accounts that require amplification.
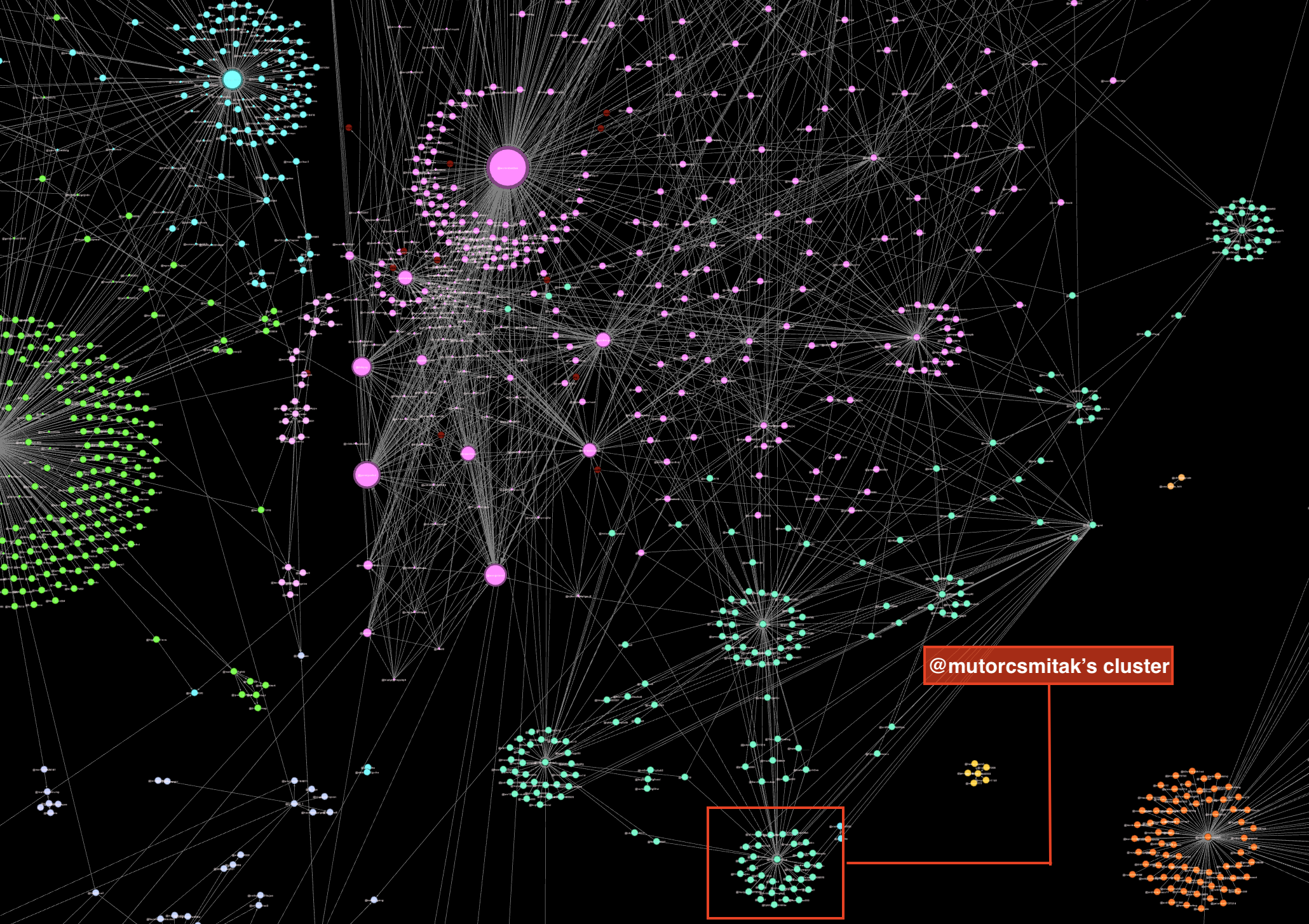
This smaller cluster of poster and amplifier accounts, like mutorcsmitak’s cluster, is repeated across the entire network, drawing resources from many other accounts. You can see this in the image below, which shows stronger edges (the lines) forming the links between clusters in the network.
Creation Of New Accounts To Fuel The Network
The network supports its operations by creating new accounts every day. Over the time the dataset was collected, many new accounts were created to join the network.
Over the space of four days, the following numbers joined the network:
- April 27, 2020: 52 accounts
- April 28, 2020: 97 accounts
- April 29, 2020: 109 accounts
- April 30, 2020: 151 accounts
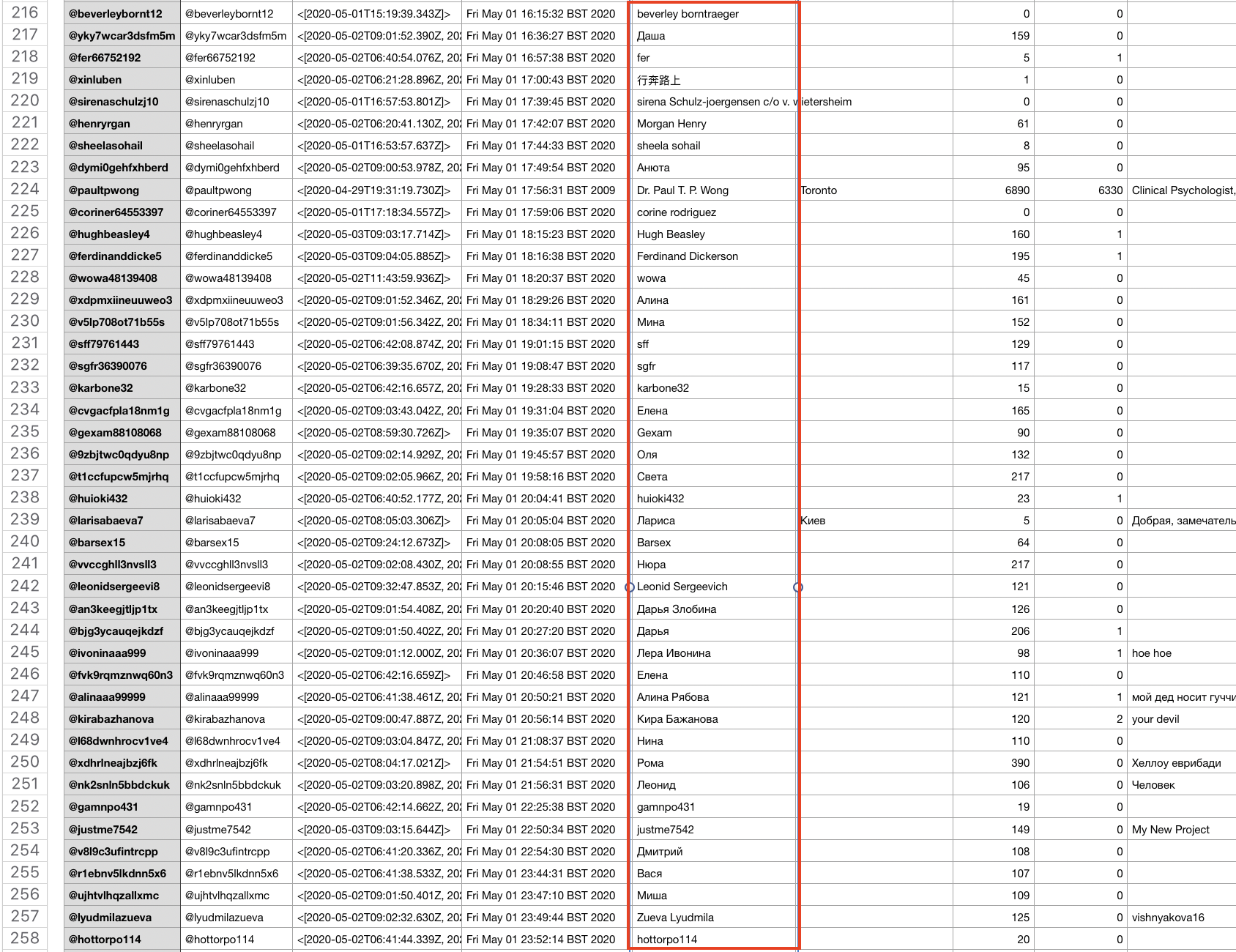
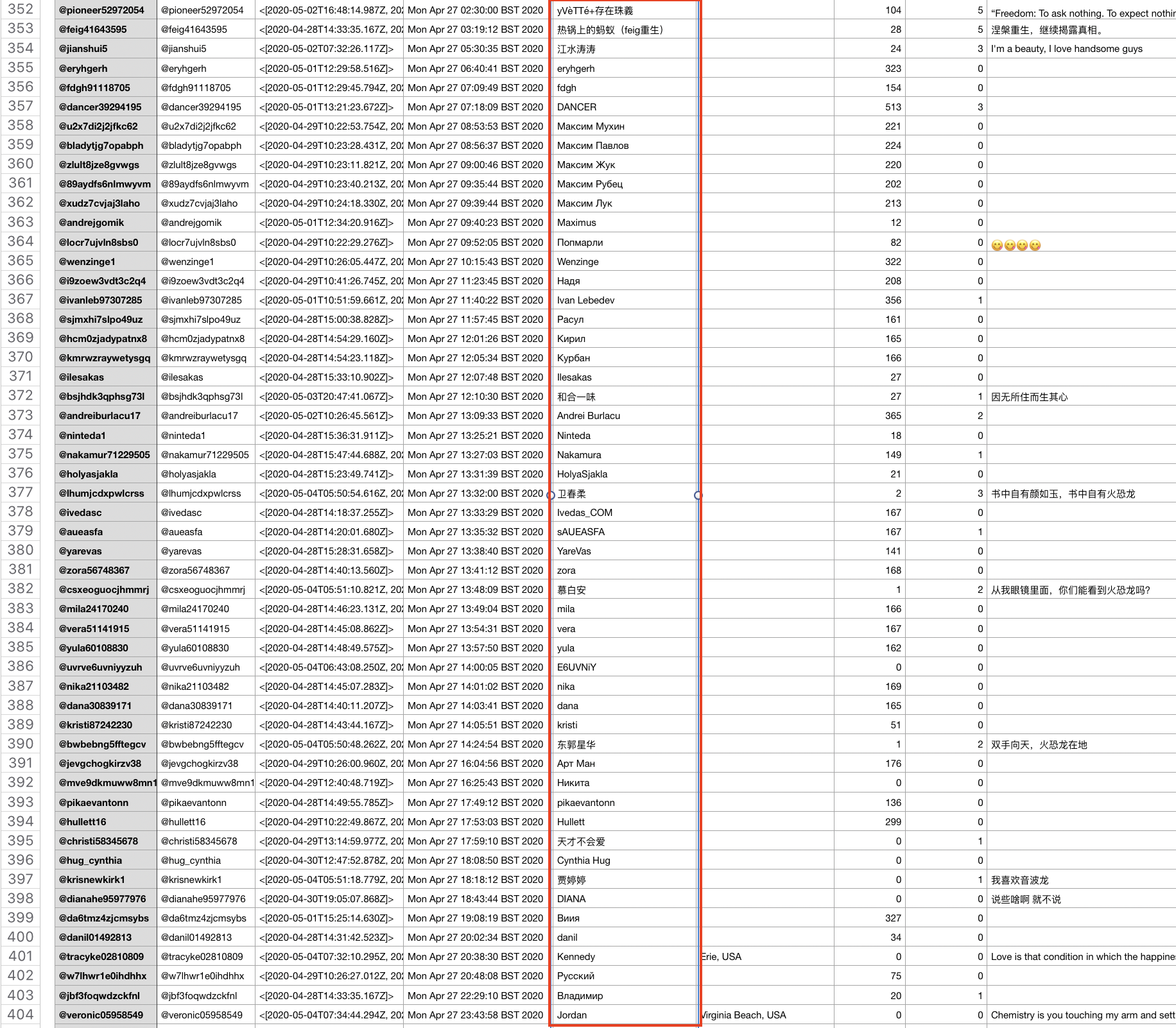
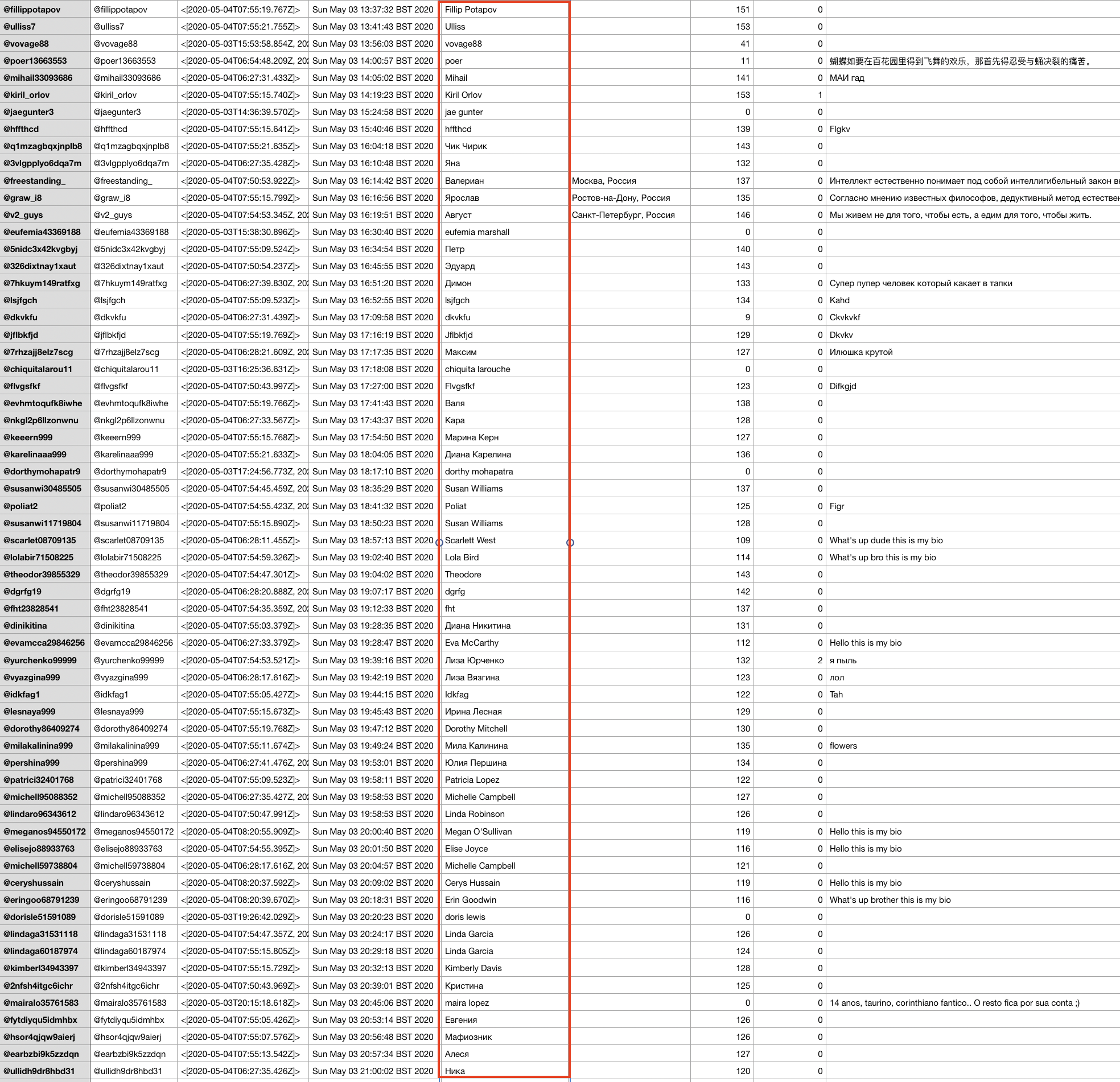
I have provided screenshots below of samples from those dates to show the accounts created, their generic Twitter handles, and usernames.
Not only are the mass creation dates and times visible in this, but also the nature of the accounts’ names, of which many appear in cyrillic, yet support a pro-Chinese government narrative.
Language Themes Of The Network’s Accounts
The accounts providing the amplification vary in languages and the style of names Twitter, and when there is a bio present, they vary in that too.
Some accounts use names written in Chinese, while other accounts in the network use Russian Twitter account names written in Cyrillic alphabet.
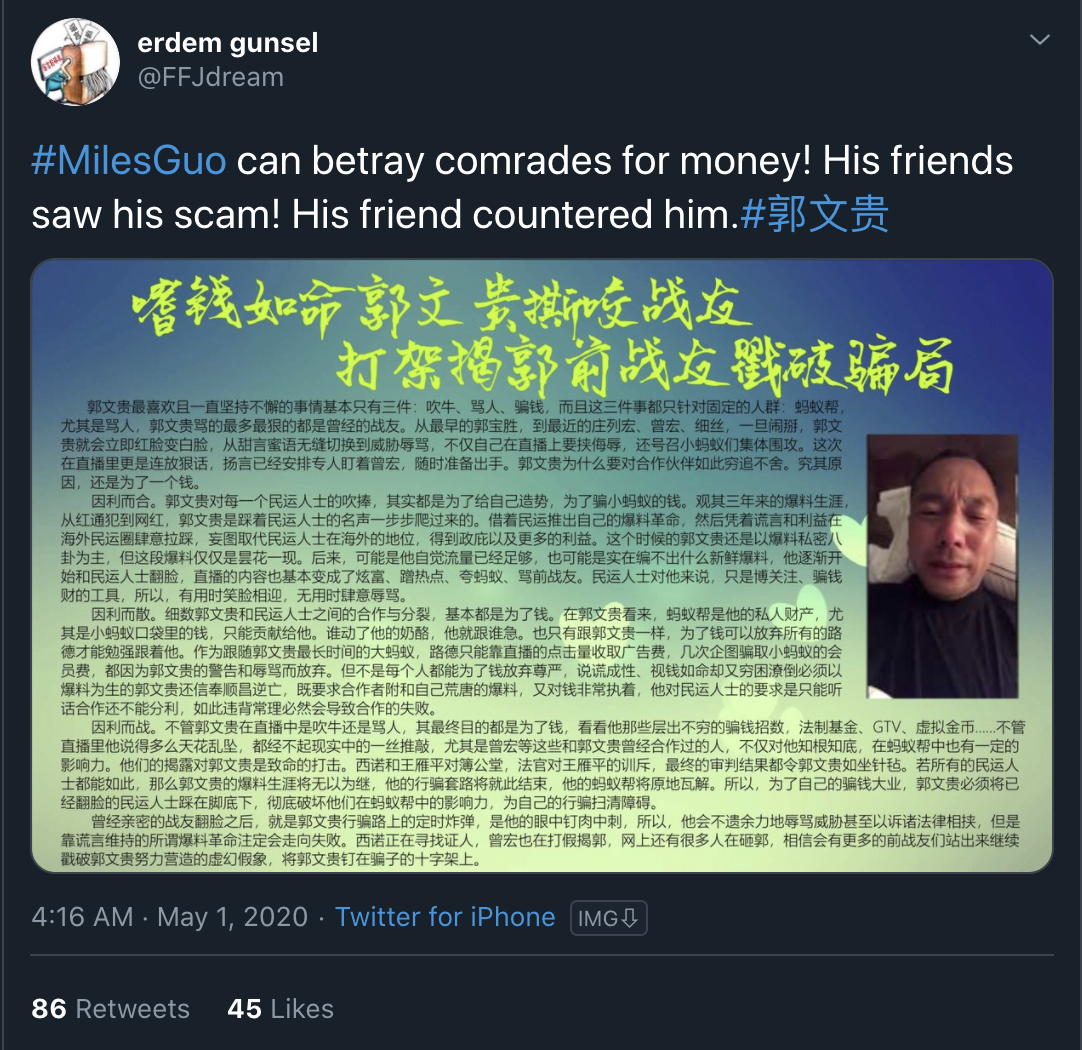
For example, let’s look at account FFJdream, one of the posters of the more common media seen displayed under the MilesGuo hashtags.
The retweets appear to come from a mix of different accounts, but for the majority, they display in Cyrillic-based languages, primarily in Russian.
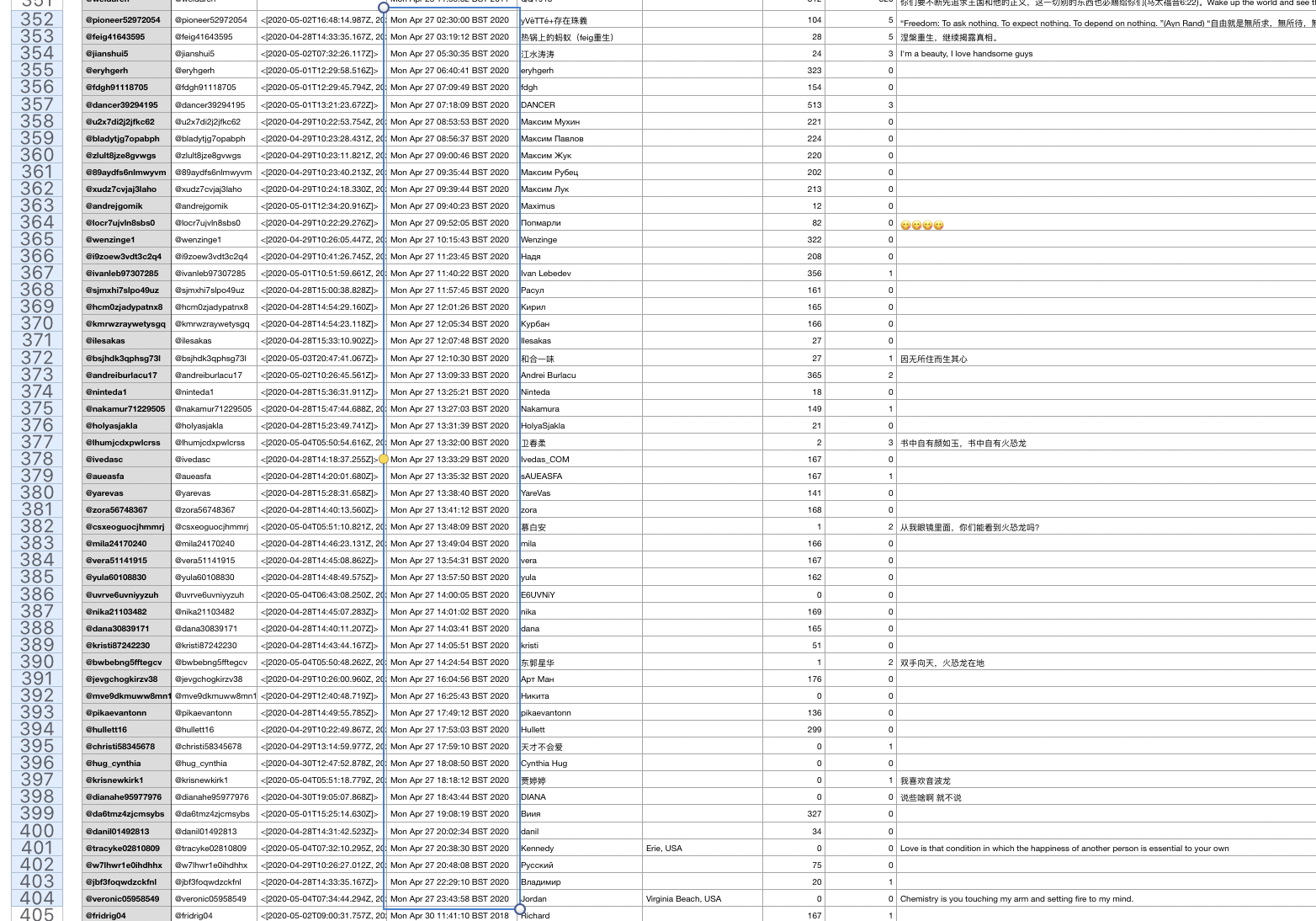
It is evident by looking at the data in spreadsheet format that there is a tendency to use Russian names. Below are some of the screenshots from the days that saw significant account creations. The names column is identified in red.
Content Of The Network: The Case Of Guo Wengui
Many of the accounts are part of a sustained information campaign against Guo Wengui, an exiled Chinese businessman residing in the United States.
This is not the first time Guo, also known as Miles Kwok, has been subject to a coordinated campaign on Twitter. A report from ASPI in 2019 identified operations targeting him as far back as April 2017.
Guo has been critical of the Chinese government in the past, and more recently he has criticised its response to COVID-19. Many of the accounts in the network target these claims specifically.
This analysis does not support claims made by Guo, nor does it negate them. The focus of this report is on the network, not Guo.
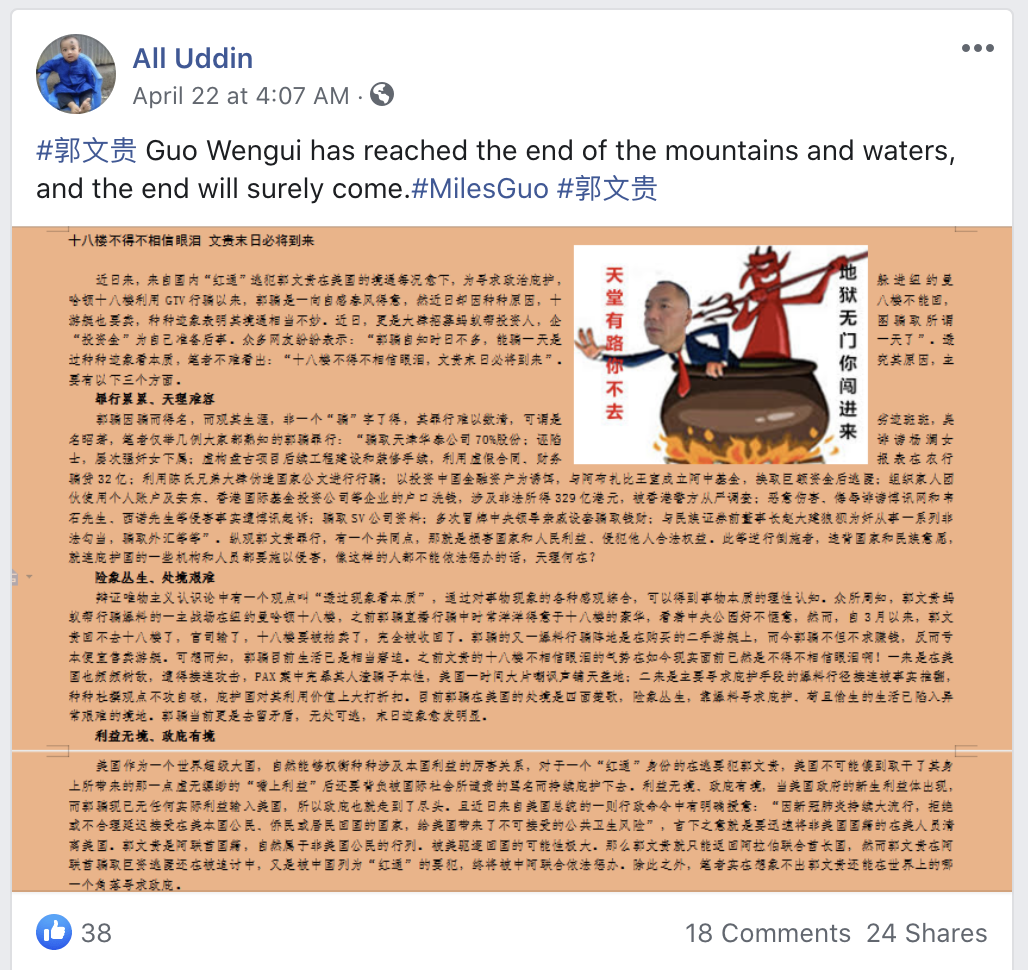
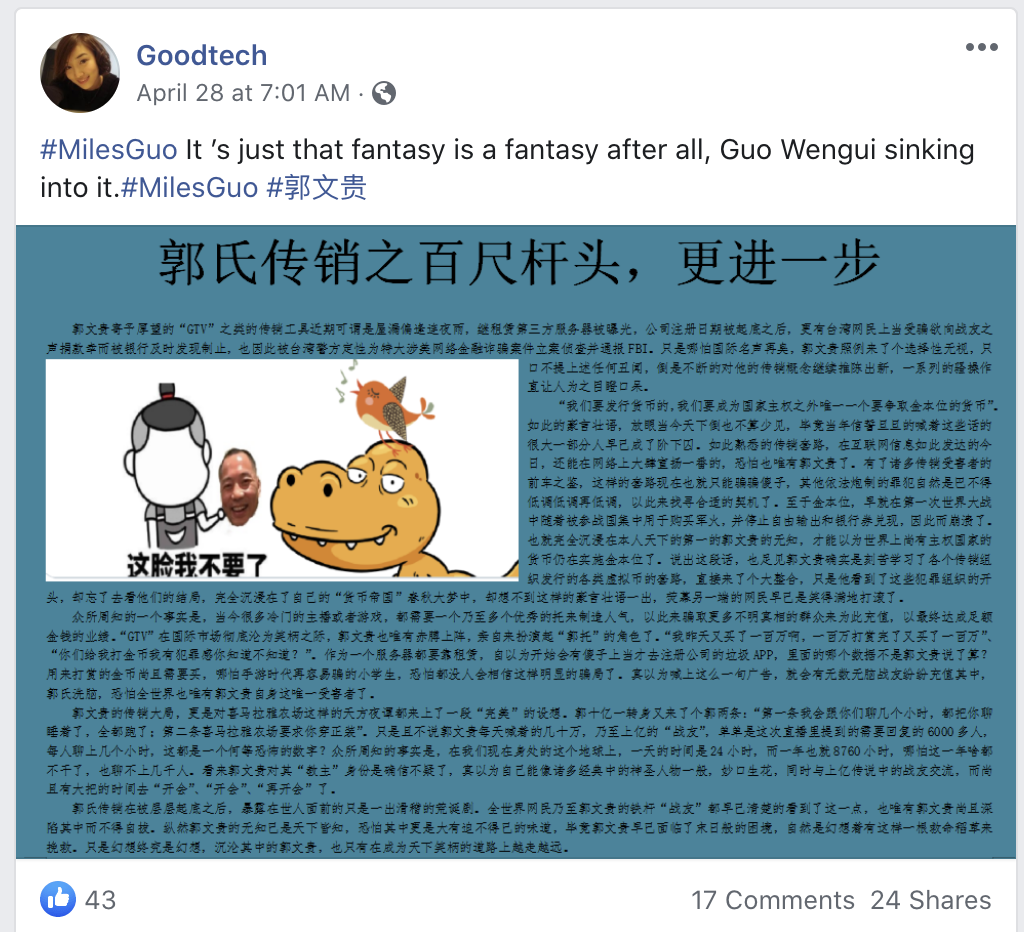
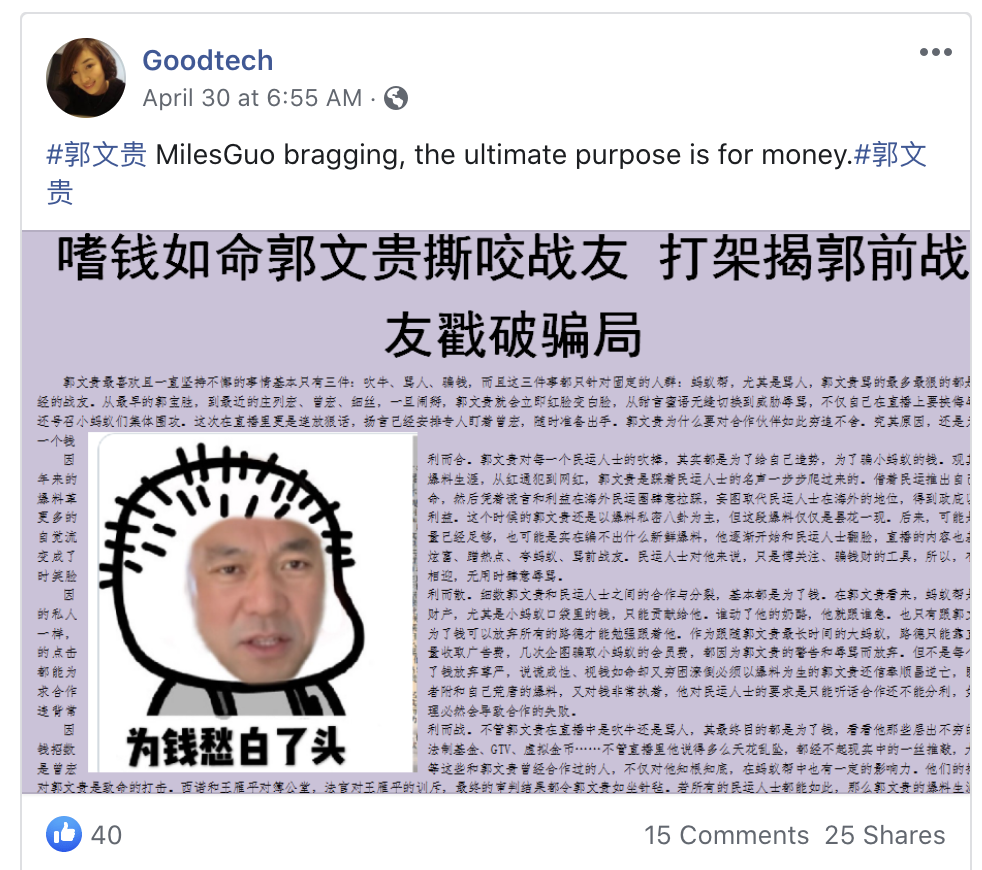
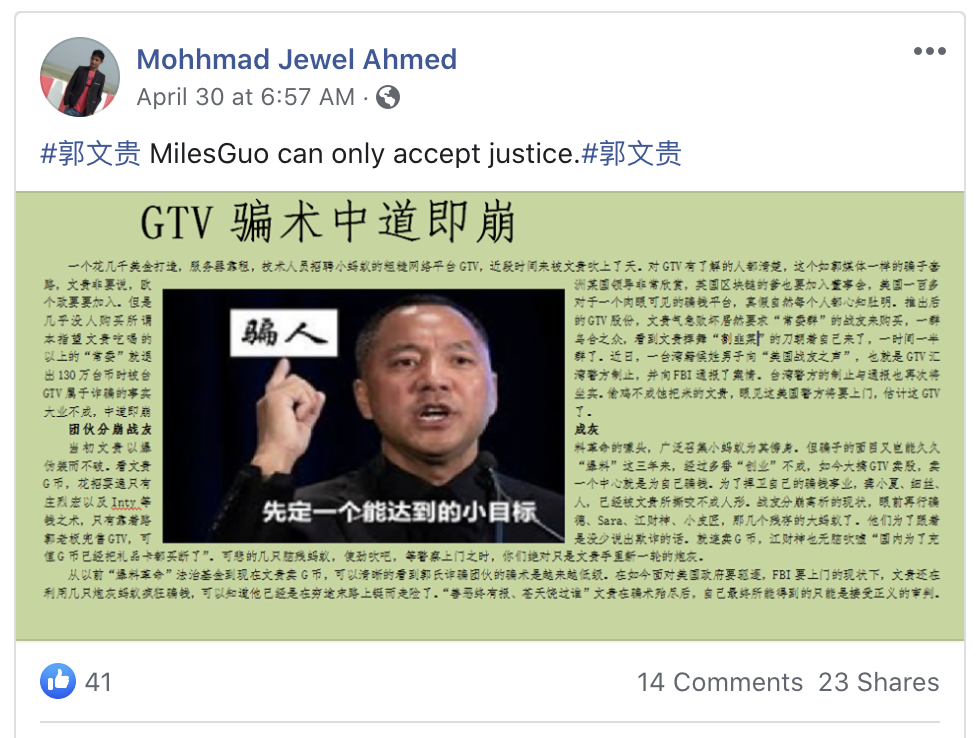
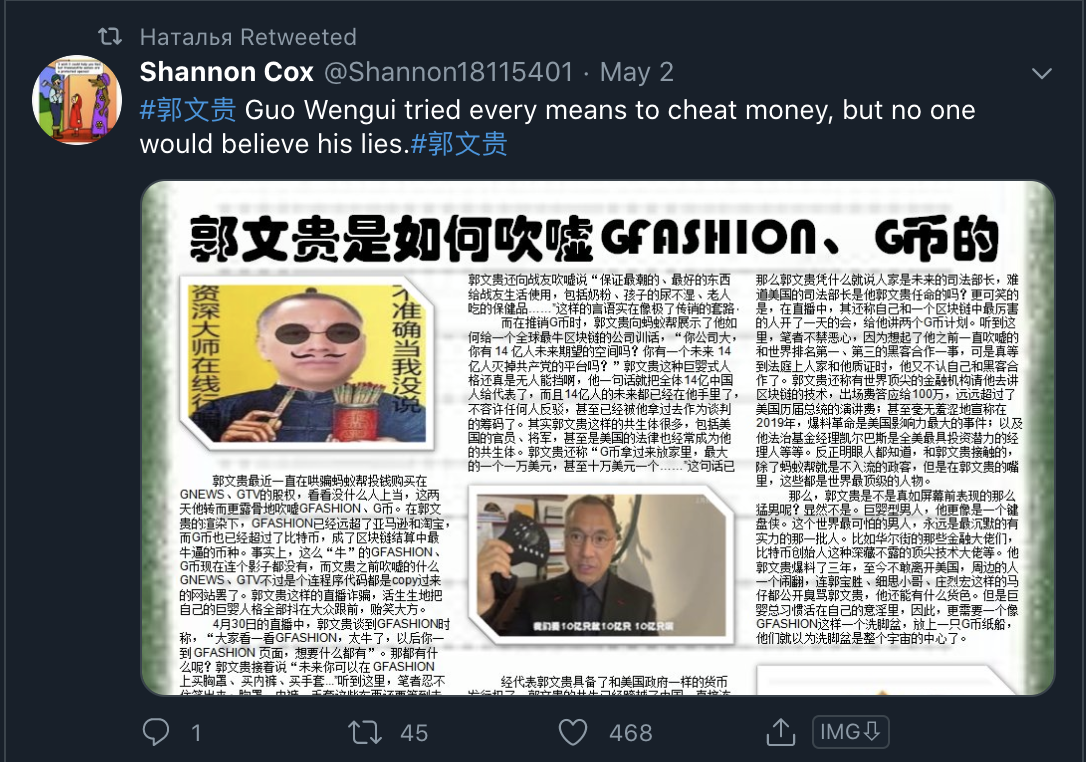
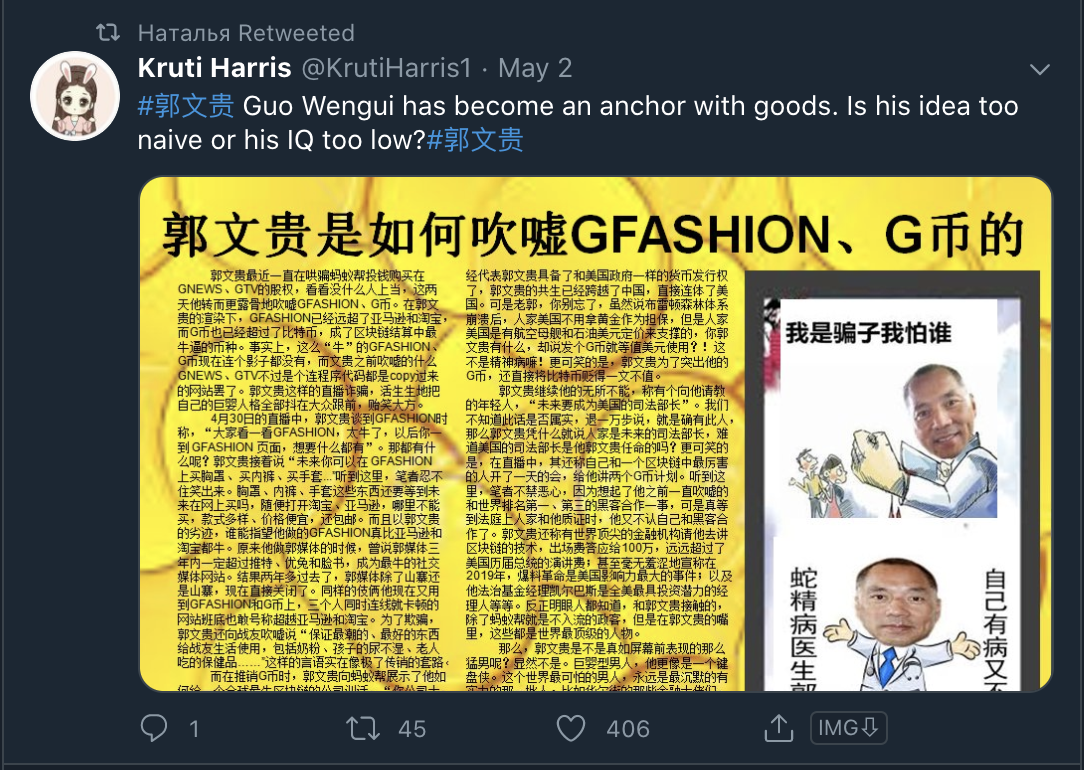
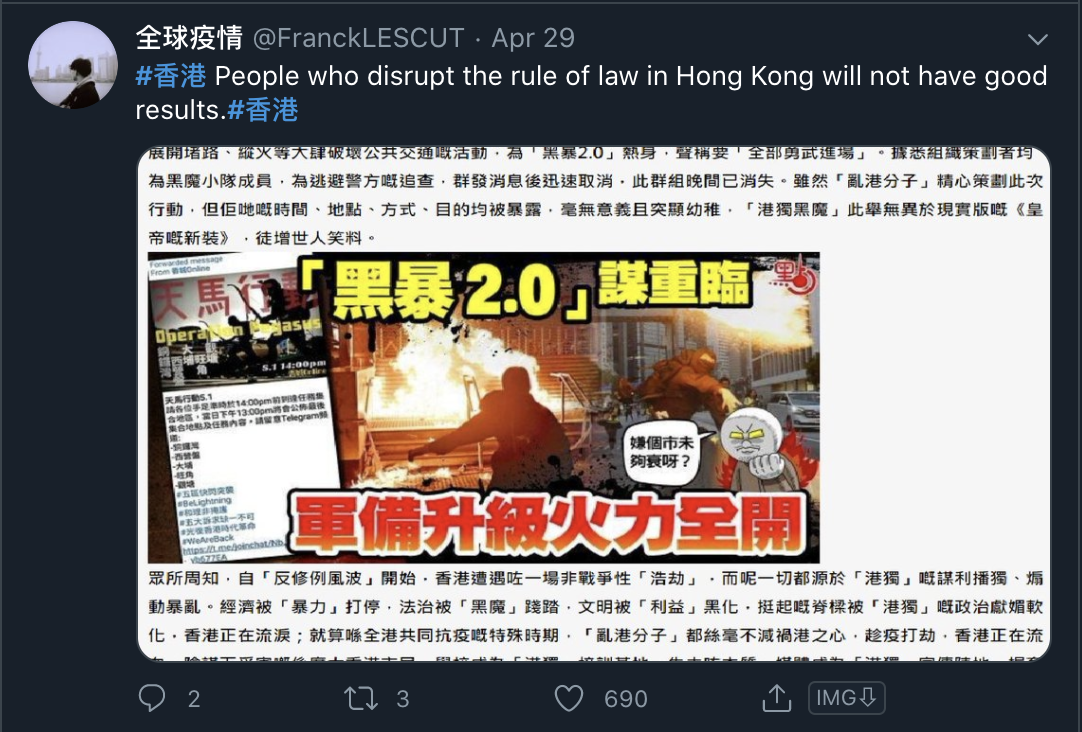
Common points of the network are the previously mentioned poster and amplifier system, as well as the posts, which consist of graphics and text written in Chinese.
The text is critical of Guo and his claims and appears to counter some of the claims he makes.
These posts are echoed largely in the network, as seen below
The content is also present on Facebook, where the network also operates using hijacked accounts and pages.
Content Of The Network: Alternative Topics
The network on Twitter does not just amplify content based on Guo. It also appears to target other areas in coordinated efforts, for example the Hong Kong protests, cryptocurrency, and COVID-19.
Hong Kong Protests Content
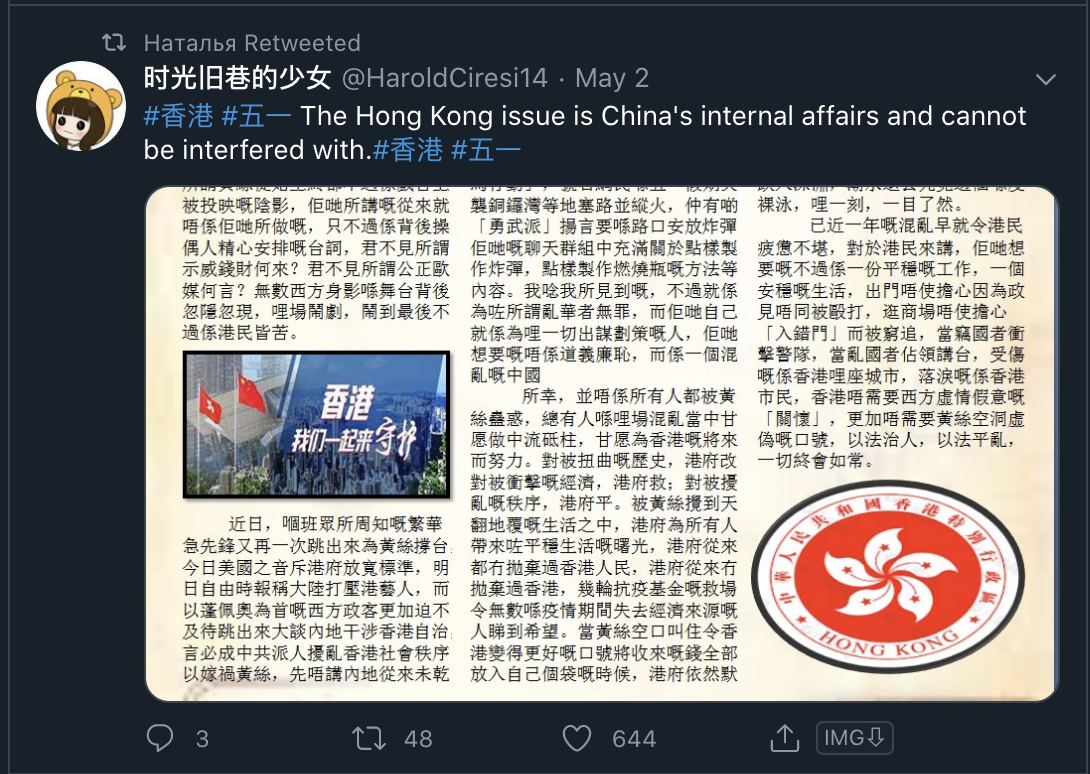
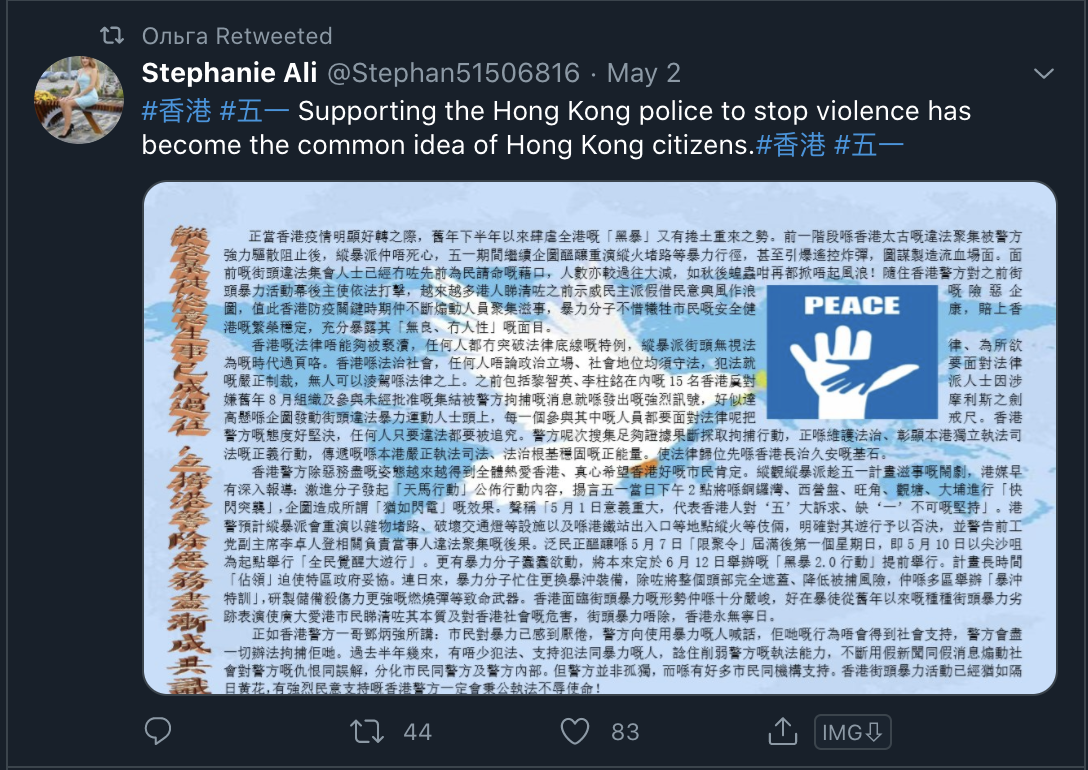
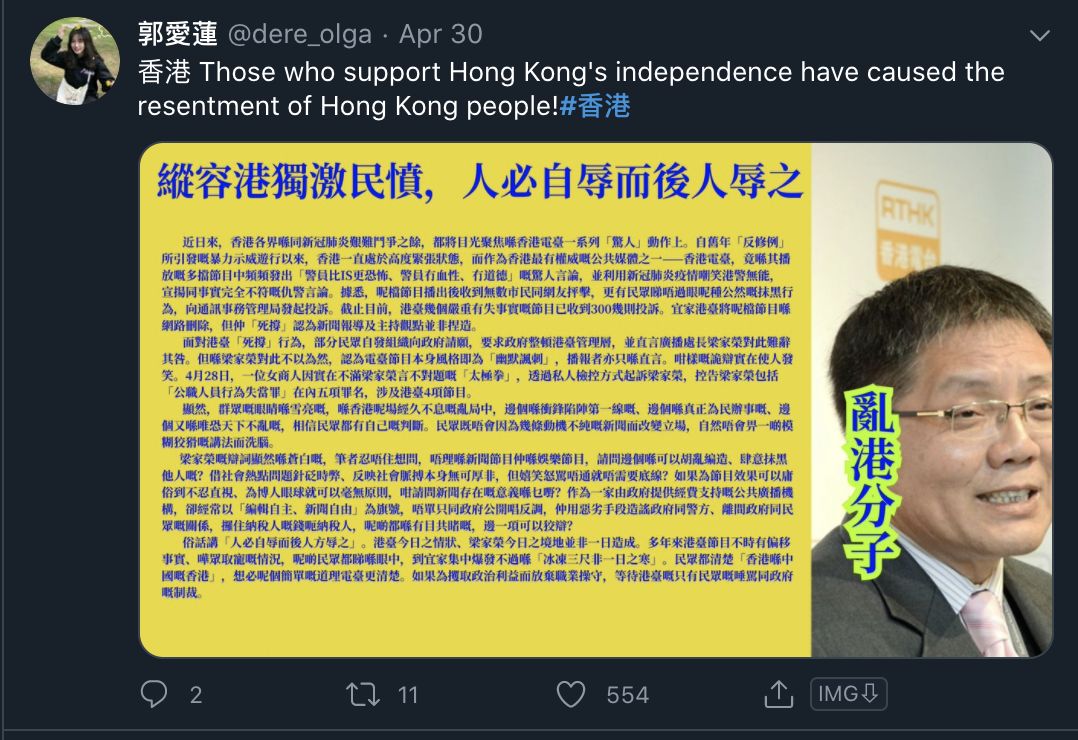
The same network amplifying content related to Guo is also critical of the Hong Kong protest movement. These findings are consistent with the 2019 report made by ASPI as well as the targeting of political opponents and protestors.
In the network, a number of amplifier Russian-themed accounts have been identified. By looking at the activity of those accounts we can identify the links to potential efforts of the network.
Below is an amplifier account active in that network.
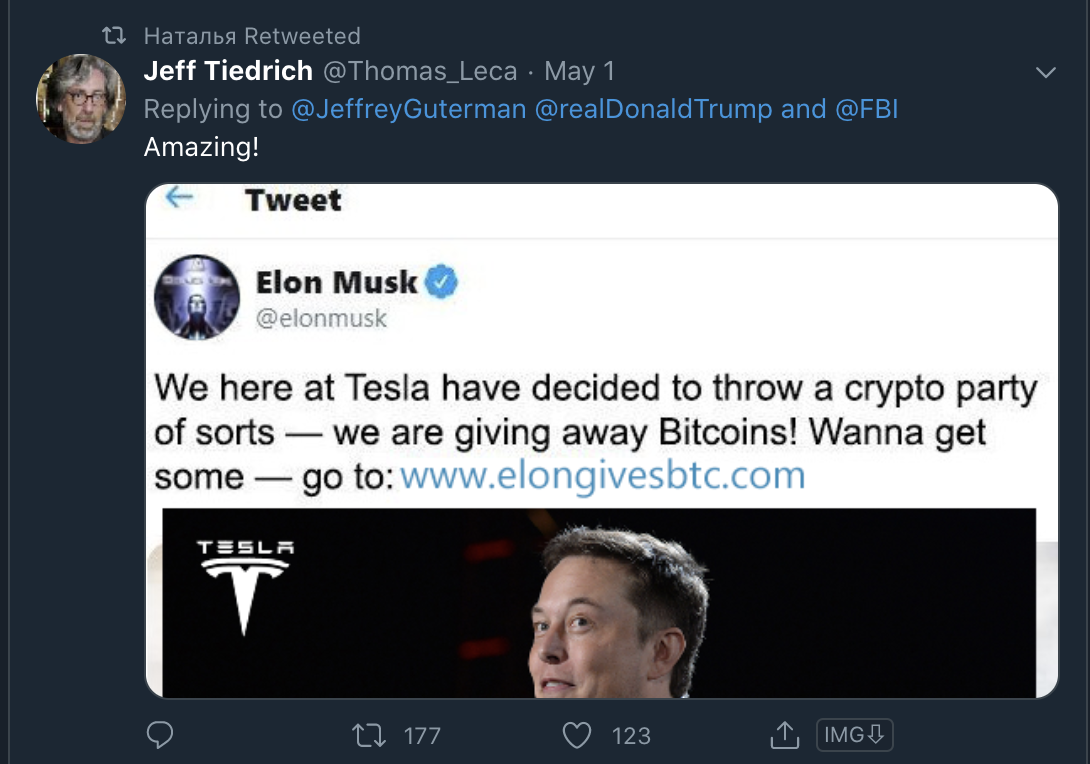
It retweets content consistent with the efforts of the network — as seen below, there are tweets about Guo and tweets on Elon Musk and cryptocurrency (these will be shown as part of the network’s targeting in the next section).
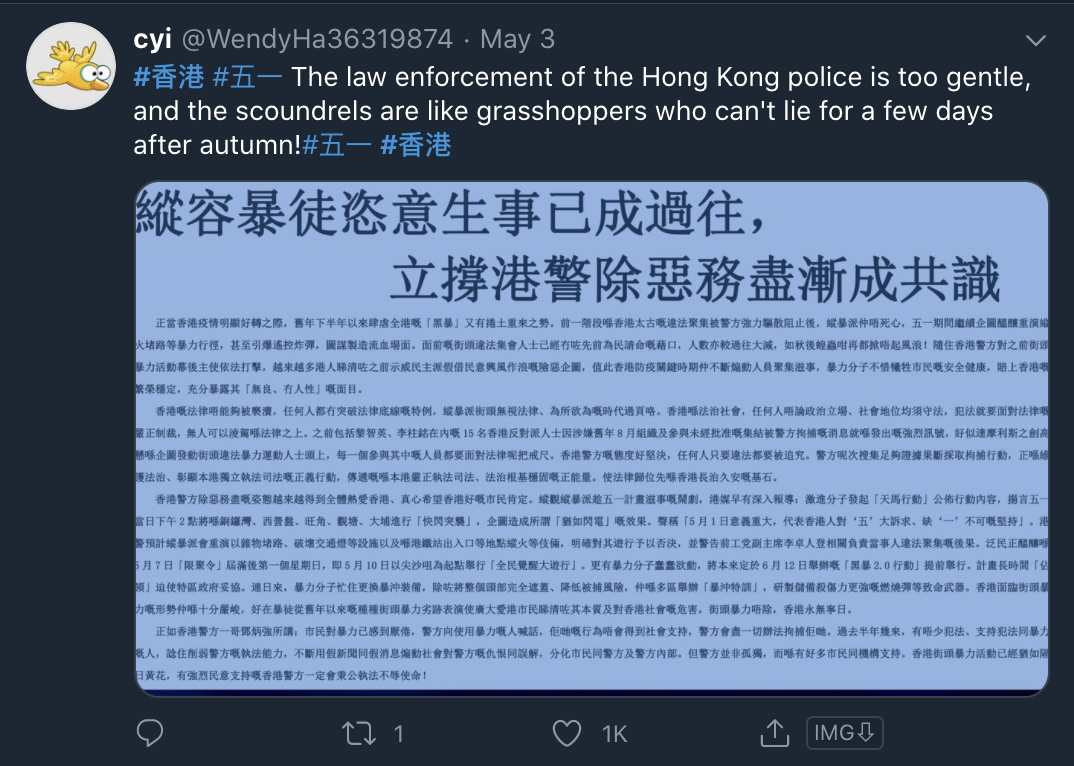
The same account reposted this tweet supportive of China’s actions in the Hong Kong protests.
The network amplifies a series of tweets supportive of the police in Hong Kong and critical of those who seek independence. Screenshots of some of the posts in the network by other Russian or Chinese-named amplifiers are as follows.
Cryptocurrency/Elon Musk Content
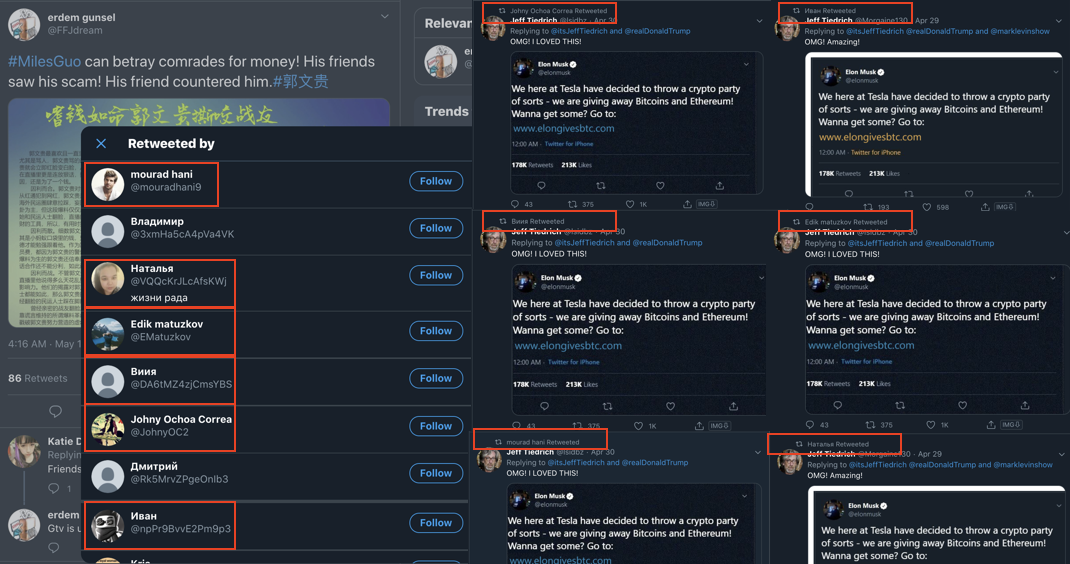
Another example of the content retweeted by this network is evidenced below. It is content related to Elon Musk and cryptocurrency.
The graphic below represents retweeters of one of the Guo posts on the left and those same accounts retweeting the Elon Musk crypto post. I have matched them to all retweeting the same Elon Musk/crypto-related post that was a comment underneath a post from Donald Trump.
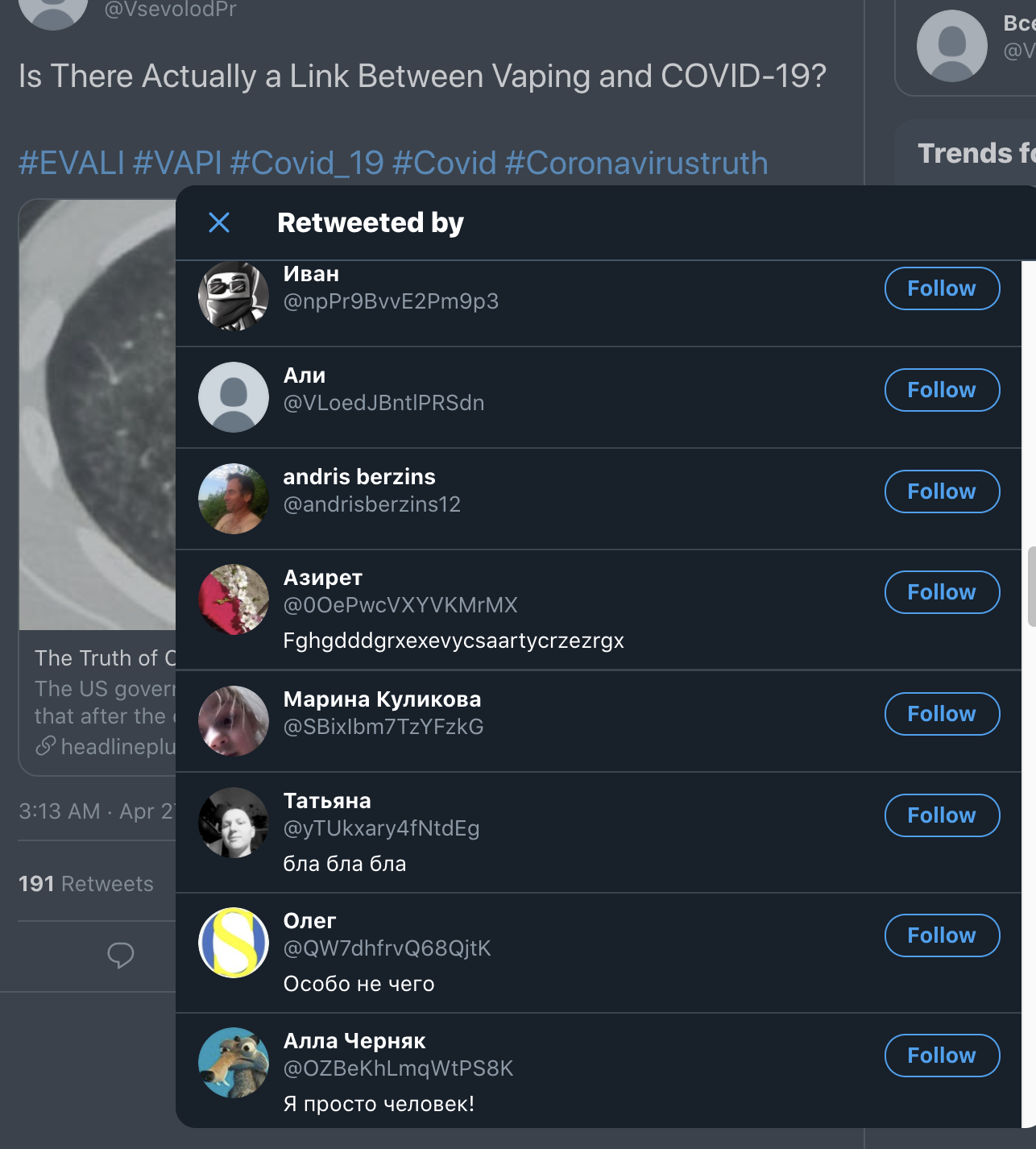
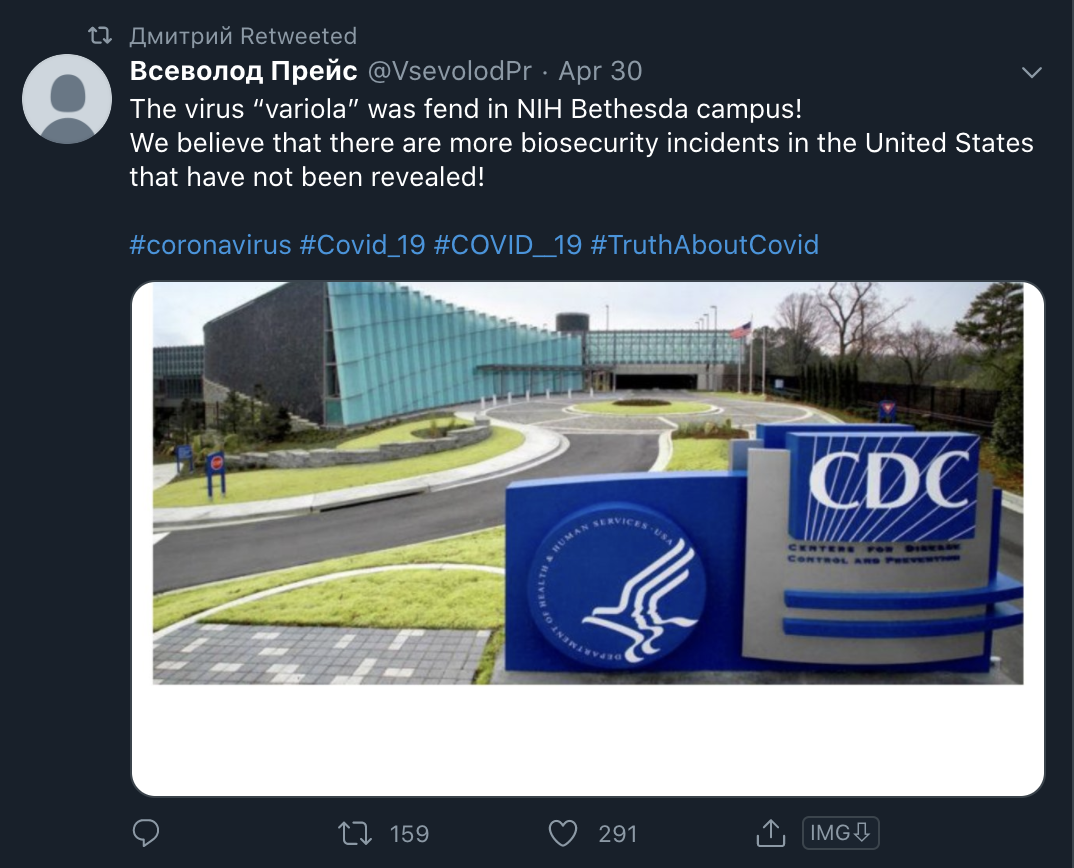
COVID-19 Content
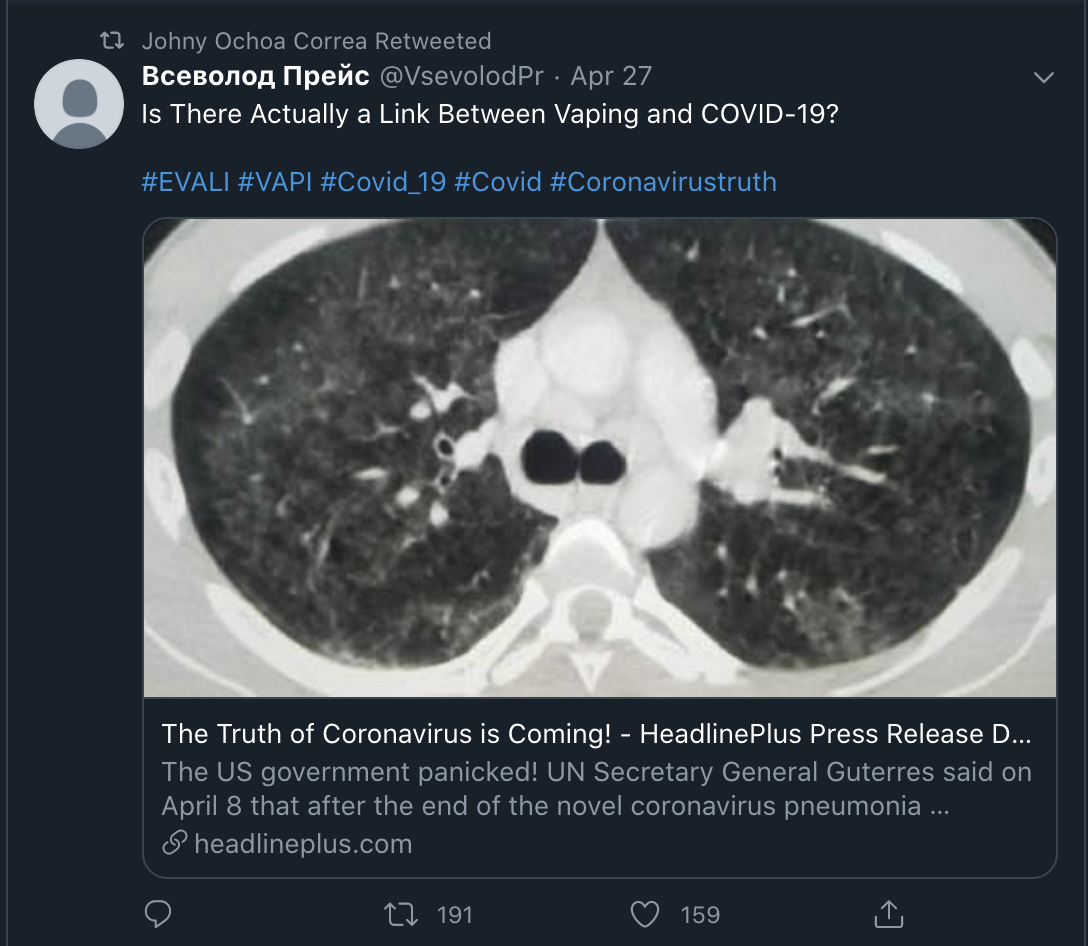
That same cluster seen above has also amplified specific posts on COVID-19, targeting the U.S. These accounts posting the content follow the same structure of name, account creation, and targeted campaign areas.
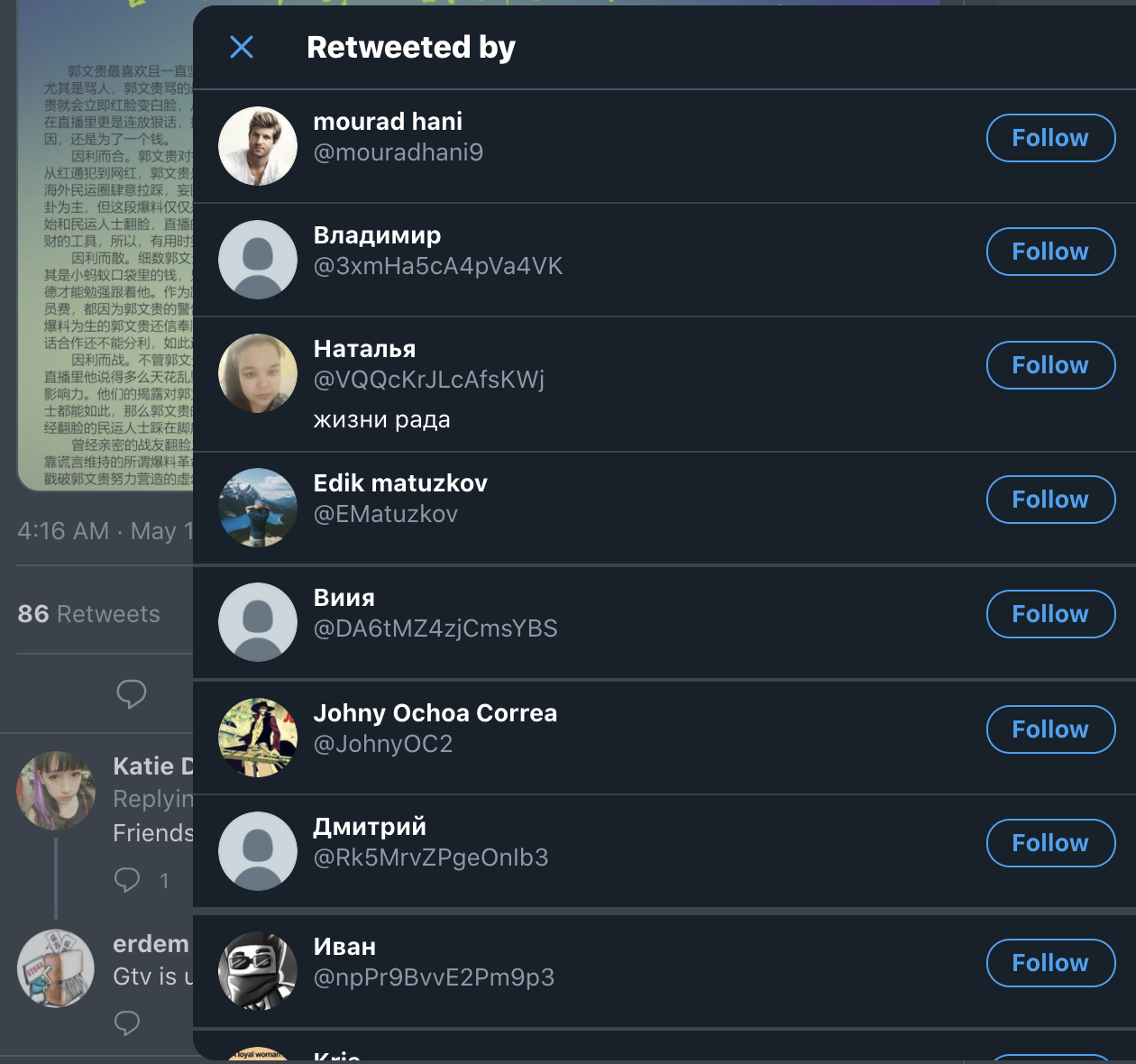
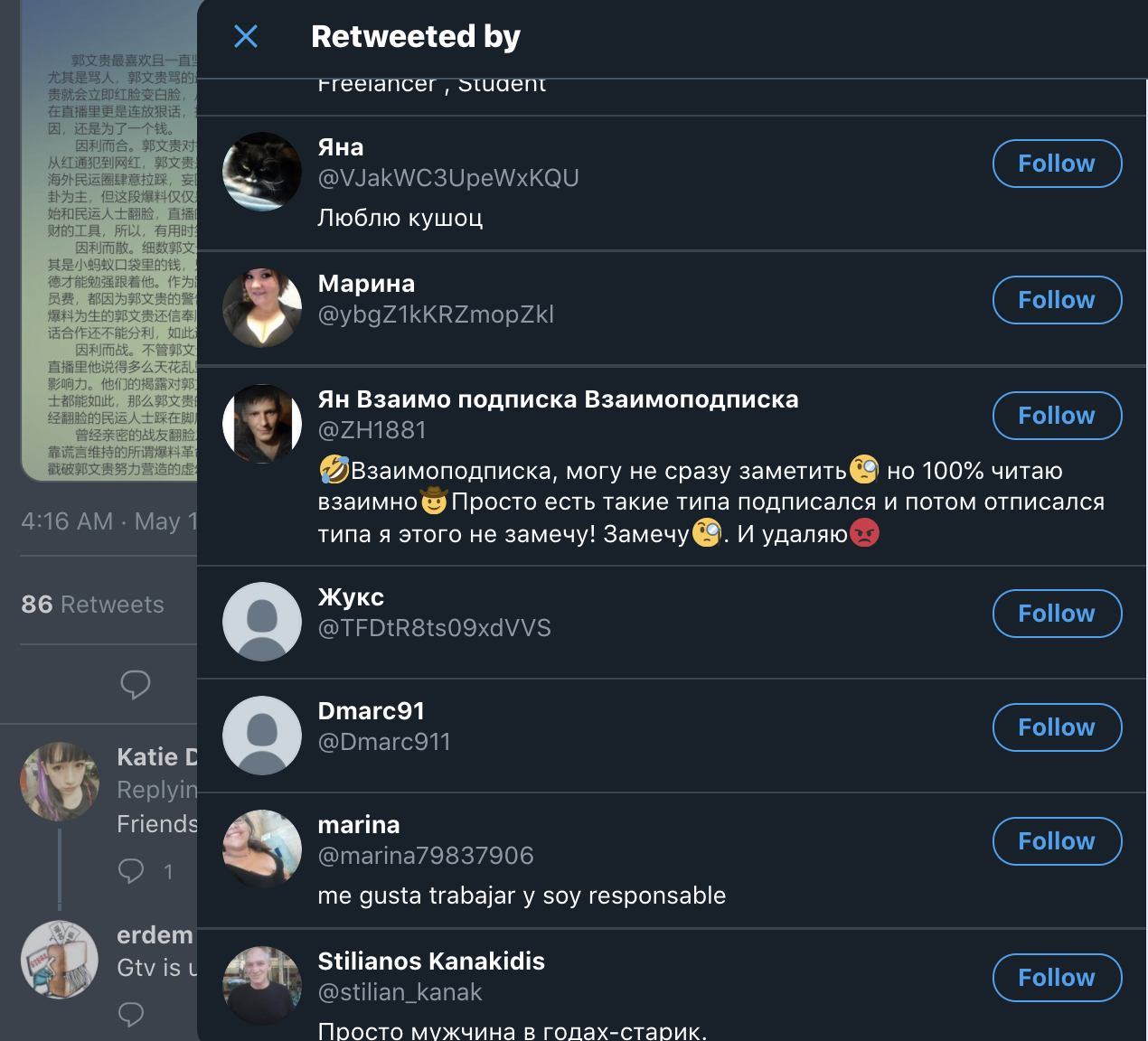
The posts seen include subject matter of health posts on links between vaping and COVID-19 and allegations of biosecurity incidents in the U.S. with the tags #coronavirus and #TruthAboutCovid. Examples can be seen below, these are screenshots from two of the same accounts that were seen above (Johny Ochoa Correa, Наталья).
Again, the retweets of the above post follow the same signs present among amplifiers in the network.
And below are the retweets of the post above.
Summary Of Findings
This analysis shows that there is an active network of accounts targeting subjects in a coordinated approach to skew the narrative around varying topics, and to push set agendas. Many of these agendas are supportive of the Chinese government and critical of either popular figures or protestors who are against it.
The network operates through consistent account creation to add more numbers and seeming veracity to its network, using a system of poster and amplifier accounts to “stage” trending topics, and to provide the illusion of viral tweets.
This network exists on both Twitter and Facebook.
Content of the accounts correlates with findings made in the past, both by Twitter and other entities, of state-linked information operations that are being run out of People’s Republic of China.