305 Car Registrations May Point to Massive GRU Security Breach
In an unprecedented step, the Dutch Military Intelligence and Security Service (MIVD) and the United Kingdom’s Ministry of Justice on October 4, 2018 disclosed the identities under which four Russian individuals, believed to be officers of the cyber-warfare division of the Russia’s Main Directorate of the General Staff of the Armed Forces (GRU). The four individuals travelled to the Netherlands in April 2018 in an attempt to hack into the computer network of the Organisation for the Prohibition of Chemical Weapons (OPCW), based in The Hague. These four men travelled under diplomatic passports, two of which had consecutive issue numbers.
Following this disclosure, Bellingcat and its Russian investigative partner, The Insider, attempted to verify that the identities disclosed by the Dutch authorities were in fact the authentic identities of the persons involved. Comparing data from different databases dated 2002 to 2014, Bellingcat was able to confirm that these identities are indeed real, as opposed to cover personas, which is the case with the two GRU officers involved in the Skripal poisoning case.

Figure 1. Aleksei Morenets, one of the four accused GRU officers, as seen on the diplomatic passport disclosed by the Dutch authorities.
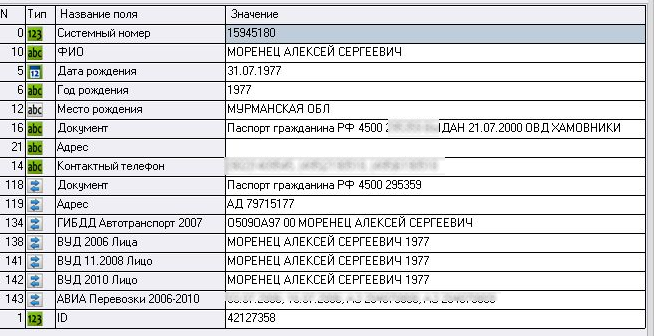
Figure 2. Data on Aleksei Morenets from a 2010 Russian database.
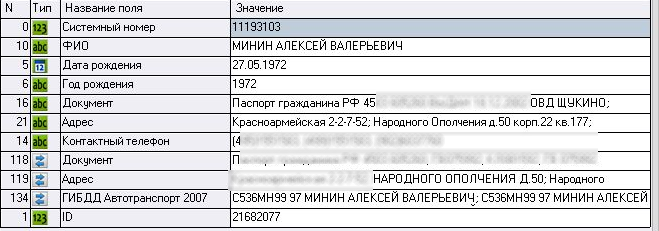
Figure 3. Personal records on Aleksei Minin, a second suspect. The address at which Aleksei Minin was registered as of 2011 was listed as Ulitsa Narodnogo Opolcneniya 50, the official address of the GRU Conservatory.
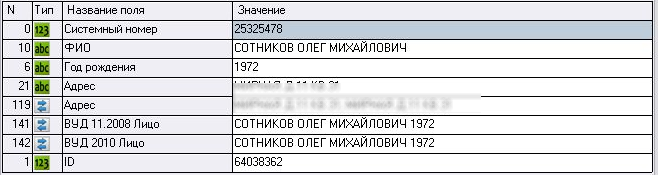
Figure 4. Records on the third suspect, Oleg Sotnikov
Registration at the GRU Conservatory
Database records for one of the four suspects indicated that he was registered as residing at Ulitsa Narodnogo Opolcheniya 50, an address in Moscow where the Military Academy of the Ministry of Defence is situated. This Academy is popularly known as the GRU Conservatory.
In the course of researching the authenticity of the personal data of the four individuals, Bellingcat was able to locate one of the four GRU officers identified by the MIVD in a Russian automobile ownership database. As of 2011, Alexey Morenets was the registered user and/or owner of a Lada (VAZ 21093) car.
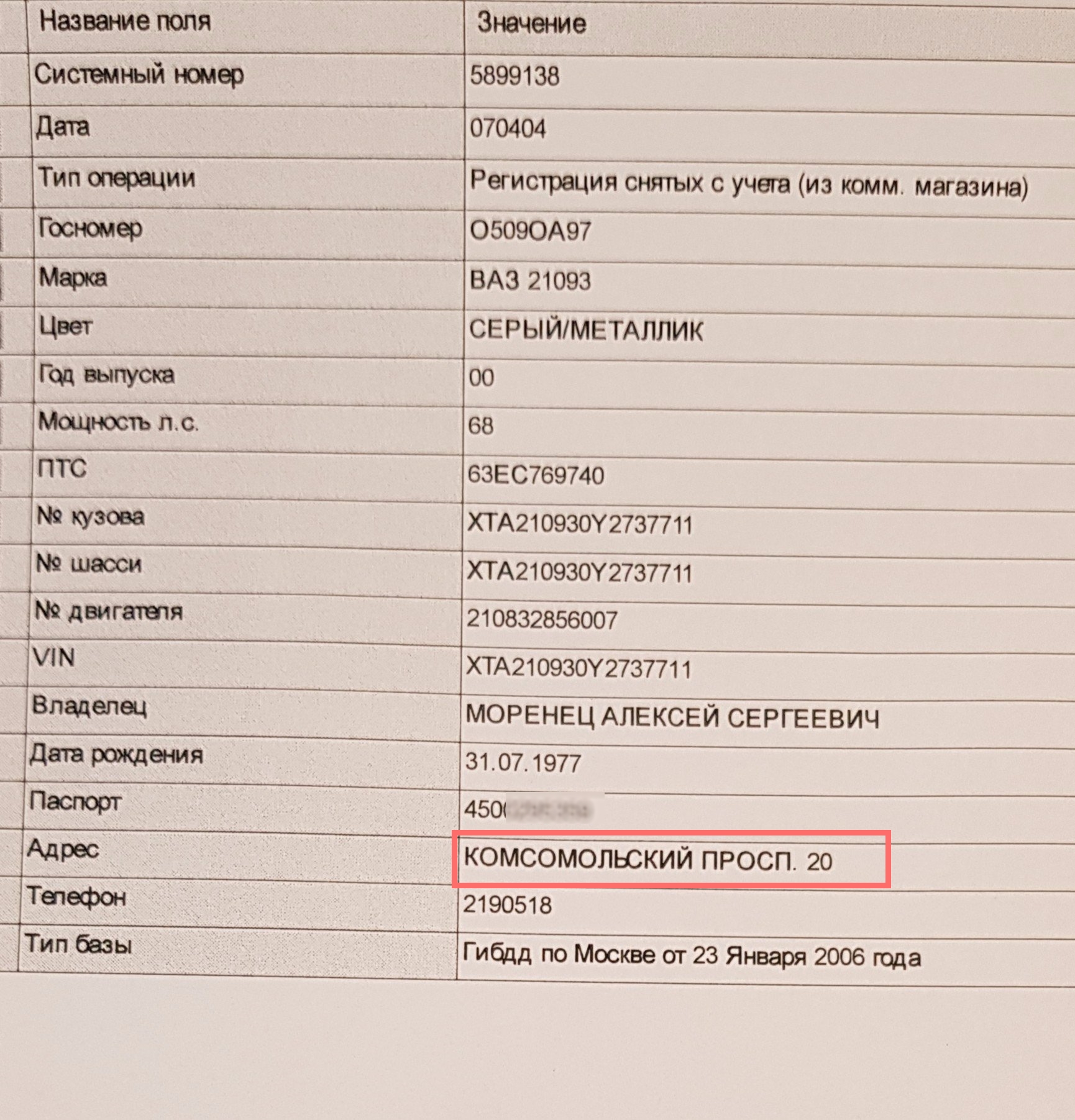
Figure 5. Vehicle registration information for Alexey Morenets. The highlighted address is Komsomolsky Prospekt 20, the address of military unit 26165 of the GRU.
The address to which the car was registered, Komsomolsky Prospekt 20, coincides with the address of military unit 26165, described by Dutch and U.S. law enforcement as GRU’s cyber warfare department. The database entry contained Morenets’s passport number.
305 Cars for 305 Officers
By searching for other vehicles registered to the same address, Bellingcat was able to produce a list of 305 individuals who operated cars registered to the same address. The individuals range in age from 27 to 53 years of age.

Figure 6. A part of the list of 305 individuals who operate cars registered to the same address as Mr Morinets
The database contains their full names and passport numbers, as well as — in most cases — mobile telephone numbers. Besides the physical street address, the address entry points out the specific Military Unit: 26165. This is the same unit as the one identified in the United States Department of Justice indictments that were also announced on October 4, 2018.
If these 305 individuals — whose full personal data is available in the automobile registration database consulted by Bellingcat — are indeed officers or otherwise affiliated with the GRU’s military unit 26165, their listing in a publicly accessible database may constitute one of the largest mass breaches of personal data of an intelligence service in recent history.


