Massive White Supremacist Message Board Leak: How to Access and Interpret the Data
The Internet Archive has removed the SQL leak; however, the information is freely available at Distributed Denial of Secrets here.
Today, the entire SQL database from Iron March, a now-defunct neo-Nazi / white supremacist message board, was posted onto the Internet Archive by the user “antifa-data“. You can access this data dump on the Internet Archive, and via a torrent file found here, or through this Magnet link.
Apparently the entire SQL database of the international neo-fascist Iron March forum (where Atomwaffen first properly organised). Contains info on all users, including user emails, IP address, and private messages, as well as all posts and comments. Enjoy. https://t.co/iq8D7IRorU pic.twitter.com/GTzz31HxGs
— Jake Hanrahan (@Jake_Hanrahan) November 6, 2019
This leak contained the entirety of the site’s information, including user names, registered emails, IP addresses of users, all of the forum’s public posts, and even the private messages between members. This message board was linked with the violent neo-Nazi group Atomwaffen Division, and has been widely studied by anti-extremist groups and researchers, such as the Southern Poverty Law Center (SPLC). The SPLC has also scraped all of the public posts from the site — well over 150,000 of them — and has been researching them over the last two years.
How to access the files
There are two ways to read and access the leak. The first is through the SQL database within the torrent, which can be accessed through an SQL database viewer (for example, MySQL Workbench or DB Browser for SQLite). However, this is quite arduous for the average user.
It is much easier to read through the exported spreadsheets that are included within the torrent file. The most important spreadsheets for analysis, and the most important columns within them, are:
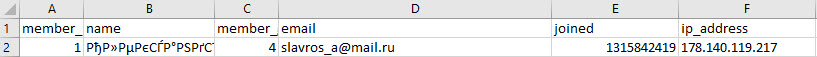
core_members (All users)
- Column A indicates the member ID, which is reflected across other spreadsheets as well.
- Column B indicates the username within the site.
- Column D indicates the registration email used by the user.
- Column E indicates the time that the user signed up, converted into Unix time. You can convert the timestamp into normal time here; for example, the first user sign-up was at 1315842419, or 12 September 2011 at 3:46pm (UTC).
- Column F indicates the IP address at registration; however, this could be spoofed if the user deployed a VPN or proxy connection.
- Columns M-O indicate the date of birth provided by the user.
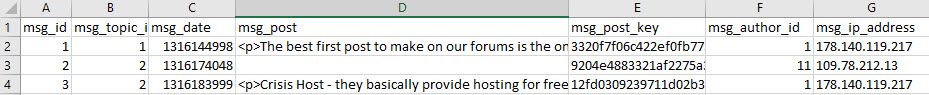
core_message_posts (All private messages)
- Column A indicates the unique message ID — every single message sent on the forum has its own ID.
- Column B indicates the message topic (thread) — each conversation between users has its own thread, and will not always be sequential to message ID, depending on how fast the users were writing back to one another.
- Column C indicates the time of the message, converted into Unix time. You can convert the timestamp into normal time here.
- Column D indicates the message content. Note that there is sometimes a blank space before the message begins, making it (falsely) appear blank in a preview on Excel.
- Column F indicates the member ID, which can be cross-referenced with Column A in core_members.
- Column G indicates the IP address used by the user who sent the message. This can be cross-referenced with Column F in core_members.
Cross-referencing private messages (core_message_posts) and the users sending them (core_members) is quite easy, in just cross-referencing usernames and member ID numbers. Click this image, created by Jake Godin, to see how to easily cross-reference these data sets.
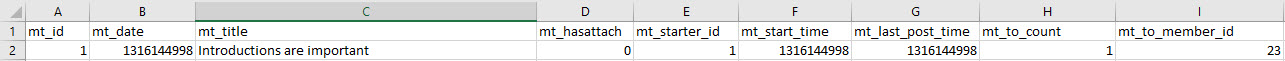
core_message_topics (Titles of all private messages)
- Column A indicates the topic (thread) ID number, which can be cross-referenced with Column B in core_message_posts.
- Column B indicates the time that the message was sent, in Unix time. You can convert the timestamp into normal time here.
- Column C indicates the title of the private message thread.
- Column E indicates the member ID of the person who first sent the message, which can be cross-referenced with Column A in core_members.
- Column I indicates the member ID of the recipient of the thread, which can be cross-referenced with Column A in core_members.
core_search_index (All forum posts)
- Column F indicates the post content.
- Column H indicates the member ID of the poster, which can be cross-referenced with Column A in core_members.
- Column J indicates the post time, converted into Unix time. You can convert the timestamp into normal time here.
Potential research leads
In a cursory survey of the data, there are a number of investigative paths for identifying active users of this forum for violent white supremacists. In particular, there are a number of users who identified themselves as active serving members of the military in Western countries, especially the United States.
We have started to compile potential leads for these users, which can be accessed here. We encourage journalists and investigators to follow up on some of these, and other, leads that can be found in these data sets. Additionally, users can suggestion additions or revisions to the existing data set.