Inside Wagnergate: Ukraine’s Brazen Sting Operation to Snare Russian Mercenaries
- On 29 July 2020, Belarusian state media announced that the country’s security services had arrested 33 fighters from the Wagner private military contractor. These men were, according to the report, part of a group of more than 200 fighters present in Belarus to destabilise the country in the run-up to its Presidential elections in early August. All of the men, whose names and dates of birth were published in the initial 29 July report, were Russian nationals while a handful also had dual citizenship with Ukraine and Belarus.
- Although Belarus initially accused Russia of meddling in the August election, the two countries appeared to reconcile with the return of the mercenaries to Russia and further cooperation in military and economic spheres.
- It later transpired that the appearance of the Russian mercenaries had nothing to do with the Belarusian elections or Russian meddling, rather it was part of a Ukrainian sting operation that had been cut short. The political fallout from these events continues to be felt over a year later, drawing in the last two presidents of Ukraine and much of the country’s security, military, and intelligence services.
A year-long investigation by Bellingcat and the Insider has established that the operation which resulted in the capture of 33 mercenaries in Minsk in July 2020 was in fact an elaborate sting conducted by Ukraine’s military intelligence service GUR MOU with the support of the counterintelligence department of the domestic intelligence agency, the SBU. Through the false-flag recruitment of mercenaries for a now defunct private military contractor (PMC), the operation aimed to lure dozens of Russian, Ukrainian and Belarusian citizens who, in the assessment of the Ukrainian authorities, had committed serious crimes while fighting for Russia-supported military entities in the country’s East.
Many, but not all of the targeted mercenaries, had fought in Ukraine’s Donbas region as part of the infamous Wagner private military contractor (PMC). Others fought as part of Russia-sponsored “volunteer corps” while others had been working directly for Russia’s military or security services. Most of the targeted men had at some point served as mercenaries for the Wagner group, whether in Ukraine or subsequently in Syria, Libya or the Central African Republic (CAR).
The operation had begun as early as 2018 as a run-of-the-mill intelligence-gathering campaign by GUR MOU. By late 2019, following the success of Ukrainian rendition operations such as the retrieval of former separatist military commander Vladimir Tsemakh, the project had taken a more ambitious turn. By early 2020 it had morphed into an opportunistic sting operation targeting hundreds of former mercenaries idling away during the Covid-19 lockdown in their home towns and villages across Russia. At this point, a number of outcomes were still under consideration. These included terminating the operation after sufficient intelligence had been gathered or luring the targets to a third country — such as Hungary, Poland, or the Baltic nations — and requesting their extradition to Ukraine.
In late 2019 and early 2020, several special operation commanding officers with successful rendition experience crossed over from the SBU to GUR MOU. Under their influence, the sting operation developed more concrete — and even more ambitious — contours. The mission became to lure, detain and prosecute a core group of several dozen mercenaries. At this point, the SBU was involved in the project planning with the aim of creating a shortlist of targets whose alleged crimes could be amply substantiated and were thus assessed to have a high likelihood of being convicted in court.
This final operational scenario was, according to three former security officers who spoke to Bellingcat, presented to and approved by Ukraine’s political leadership in early July 2020. It included the capture and detention of 33 mercenaries by staging the emergency landing on Ukrainian soil of an aircraft carrying the targets to their fictitious deployment destination. The choice of Minsk in Belarus as a starting point for the journey was a circumstance both forced (no commercial flights were taking off from Russia during the 2020 Covid-19 lockdown) and convenient. A flight from Minsk to Istanbul, the transfer hub to any number of plausible destinations, would require that the plane cross into Ukrainian airspace for approximately 28 minutes — just long enough to allow for an emergency landing at Kyiv’s Boryspil airport.
As the bus carrying the mercenaries crossed the border from Russia into Belarus on 25 July, the daring operation appeared to proceed according to plan.
But at the very last moment, a controversial decision was made to postpone the active part of the operation for a few short days. A new departure date to Turkey was set for 30 July, and the mercenary group was checked in, first to a Minsk hotel, and later to a spa hotel outside the city, to wait out the delay. In the early morning hours of the penultimate day at the hotel, Belarusian special services stormed the hotel. They detained the mercenaries, inadvertently compromising the remainder of the Ukrainian sting operation.
The timeline and context of the events chronicled in this investigation was compiled on the basis of dozens of interviews with participants in the sting operation: including Russian mercenaries who had fallen for the Ukrainian ploy and former Ukrainian intelligence operatives who had taken part in various aspects of the operation. Both groups spoke to Bellingcat to dispel what they perceived as disinformation narratives spread in both Russia and Ukraine.
To validate what these sources had to say, Bellingcat’s investigation team analysed and verified hundreds of electronic files including job applications filled out by the mercenaries, photographs of military awards and medals, letters of recommendation from former military commanders and health records which they had emailed to their fictitious new employer. Crucially, the analysis covered hundreds of audio files collected during the false flag recruitment process. Some of these documents and audio components had been leaked to Ukrainian media; however their authenticity had not been independently verified.
Bellingcat also verified key parts of the timeline of events with the Adhoc Inquest Committee of the Ukrainian Parliament. This committee has investigated, independently from Bellingcat, the circumstances surrounding the alleged failure of the same sting operation.
A detailed breakdown of the technical methods applied for this story, including our reasoning for including information from sources who could not be named, can be found in a companion article here.
The Origins of the Sting
According to interviews with four former Ukrainian special service operatives, who requested anonymity to discuss classified matters, and the former Ukrainian President Petro Poroshenko, Ukraine’s military intelligence agency, GUR MOU, and the domestic security agency, the SBU, began gathering data and creating profiles on Russian militants — including mercenaries — fighting in the East of the country in early 2014. The SBU, which also has a law-enforcement investigative function, began compiling criminal dossiers on individual militants who were judged to have committed serious crimes.
By the middle of 2018, Ukraine’s intelligence services had achieved a detailed understanding of the structure, practices and composition of Russia’s PMCs, primarily the so-called Wagner PMC affiliated with and funded via Evgeny Prigozhin, an entrepreneur close to the Kremlin. As Wagner PMC re-shuffled mercenaries from Ukraine to other hotspots such as Syria, Libya, CAR, Mozambique and other African countries, Ukraine’s intelligence agencies learnt more about military contractors’ methods of recruitment, promotion and rotation, as well as their interplay with Russia’s security services.
According to the aforementioned former special service operatives, two of these insights turned into crucial knowledge for the future sting operation. Firstly, the PMC mercenaries are rotated in and out of assignments and have to wait in their home towns or villages, sometimes for months or years, for their next job. This forces them to seek alternative employment in the meantime. Secondly, the PMC market in Russia is neither homogenous nor centralised: while Prigozhin’s Wagner group has been responsible for by far the largest number of government-sponsored overseas operations since 2014 and almost exclusively trusted for combat operations, there are several smaller companies controlled or tolerated by Russia’s security services. These provide non-combat services — such as security for valuable cargo or guarding resources for Russian companies overseas.
Based on these insights, the rough outline of a bold scheme had taken shape within Ukraine’s intelligence community. The goal was to entrap a small number of Russian mercenaries who were looking for work and had a provable history of violent crime in Eastern Ukraine. They would be lured to a location where they could be detained, extradited and handed over to Ukraine’s courts for prosecution. Early ideas discussed included baiting two to five idle mercenaries to a paramilitary training camp in Hungary where they would be attending a fictitious course for upgrading their security training level — a prerequisite for a higher pay grade in the PMC world. Similar small-scale concepts were considered with an extraction point in the Baltic states.
Higher Aspirations
On 27 June 2019, a joint GUR MOU and SBU operation on Russian-controlled territory in Eastern Ukraine resulted in the successful retrieval of a Ukrainian citizen, Vladimir Tsemakh, wanted for murder since 2014 when he had been a local militant commander in the town of Snizhne. At the time he had served as a commander of the anti-aircraft defence at Snizhne, a Russian-supplied BUK deployed just outside this village shot down flight MH17, killing all 298 people on board. This made Tsemakh an important witness, and possibly an accomplice, in the unlawful shoot-down — making his capture an even more notable achievement for the Ukrainian intelligence services (Tsemakh was subsequently surrendered to Russia as part of a prisoner swap, despite requests by the Dutch and Australian governments for him to be handed over to the Joint Investigation Team investigating the shoot-down.)
Despite the fact that Ukraine’s intelligence service suffered human losses during the sting (one officer was killed after stepping on a landmine, and another was severely injured), the operation boosted both the morale and the ambition of GUR MOU and the Fifth Directorate (which is responsible for Kyiv and the surrounding area) of the SBU’s counter-intelligence department.
The ad-hoc joint intelligence team had managed to perform a surveillance and detention operation deep in Russian-controlled territory. The team had been able to sneak the sedated suspect through Russian-controlled border posts by placing him in a wheelchair and pretending he was a sick relative needing urgent medical care in Ukraine. Possibly most importantly, the operation had proven that Russia’s security services did not have a firm grip on the whereabouts and safety of potential important witnesses and/or arrest targets.
According to the former GUR MOU operatives, the success of Tsemakh’s rendition and the knowledge of Russian security vulnerabilities which it yielded made the special operations team rethink its earlier plans. It now considered a more ambitious sting operation targeting dozens or even hundreds of suspects.
Operation Avenue 1.0
By September 2019, GUR MOU had accumulated background personal data, including current employment status, whereabouts and contact details, of over two thousand former mercenaries. Most had fought in Eastern Ukraine at some point between 2014 and 2018.
The Ukrainian intelligence agency thus already knew whom to target. The only question was how.
According to the same former special operations officers, a daring idea was proposed during a GUR MOU brainstorming session around this time. The idea was to set up a fake PMC to recruit the ex-mercenaries, with the initial goal to collect first-hand evidence and possibly confessions to crimes committed in Ukraine. As a second stage of the operation, the GUR MOU working group considered the option to lure a smaller group of shortlisted mercenaries to an international “assignment” and secure their capture outside Russia. The second stage was not however set in stone, as even the initial, evidence-gathering stage appeared both attractive and ambitious enough.
To implement this goal, a special operations team of six began working on a cover story and a detailed operational plan. To minimise the risk of compromise, they worked in isolation. The cover story required three key components: a credible PMC recruiting entity, a plausible international assignment, and a convincing project handler presumably from Russia’s secret services, or “kurator”.
The Fake PMC MAR
If they were to have any hope of enticing the mercenaries, the team required a plausible cover employer. Therefore, the team made the daring choice to surreptitiously co-opt a genuine but disused PMC that had been set up in St Petersburg in 2012. “PMC MAR” could boast of involvement in several operations “in the interest of the Russian State” in Eastern Ukraine in 2014. The self-declared government of the “DNR”, one of the Russian-backed separatist entities in Eastern Ukraine, had even praised MAR for its “humanitarian aid delivery”. Its website was active as of the end of 2019, and declared that the company would “support the interest of the state where the state cannot legally fulfil its obligations”. Its founder Alexey Marushchenko’s boisterous public statements (in 2015 he claimed that the company had deployed 70 persons in the Donbas and planned to send many more to Syria and Libya) had helped propel it to a position of outsized popularity among aspiring mercenaries. At the same time, international investigators such as the Conflict Intelligence Team cited PMC MAR as an example of an “empty shell” military contractor. On the PMC’s social media pages, people complained that its contact numbers and email did not answer job application requests.
All of this made PMC MAR the perfect bait for the planned sting operation.

PMC MAR’s founder Alexey Marushenko, second left (source)
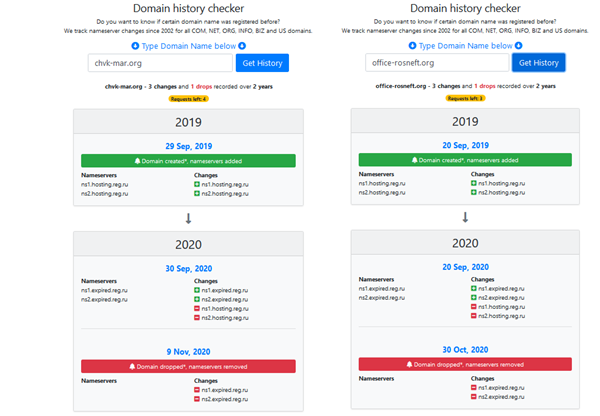
To intercept incoming recruitment queries, in September 2019 the GUR MOU team registered a lookalike domain and a cloned website, chvk-mar.org (the original MAR website was chvk-mar.ru). This also allowed them an email domain for communication with employment candidates.
The Fake Rosneft
Now the team had to come up with a credible destination for its fake recruitment drive. By the end of 2019, Wagner PMC was the exclusive proxy army used by Russia internationally. That meant that those giving shape to the sting operation had to strike a fine balance. They needed to create a potentially dangerous mission which would require the mercenaries’ military experience. It also had to appear legitimate and in the interest of the Russian state in order to deter suspicion among applicants. This came in the form of a mission to guard oil installations in the Middle East owned by Rosneft, Russia’s state-owned oil giant. As of late 2019, Rosneft was operating oil wells in the region , and Russian private security companies were reportedly in business deals with oil companies in Syria. In Iraq, Rosneft’s existing oil wells were near frontlines and naturally needed protection. The team decided to use Rosneft as the fictitious client for the upcoming security mission. To this end, the team registered — again via a Russian registrar — the bait domain name office-rosneft.org. This domain would be used for email correspondence with the candidates.
An analysis of the DNS histories of the domain names chvk-mar.org and office-rosneft.org shows that they were registered within nine days of one another at the end of September 2019, in keeping with the timeline presented by the former operatives interviewed by Bellingcat.
The Fake “Sergey Petrovich”
Every tall tale needs a main character. Therefore, the GUR MOU planning team co-opted the services of a special operations operative with actual combat experience. This individual, known under the pseudonym “Sergey Petrovich”, was well-versed in the conflict in the Donbas as well as the jargon and cultural references used by Russian mercenaries. He volunteered to act as the fake recruiter and kurator of the project, supposedly on behalf of Russia’s secret services.
Bellingcat was unable to interview this person due to the fact that investigators were only aware of his cover identity. Information about this individual’s role in the sting operation comes from interviews with the former operatives, as well as through analysis of hundreds of audio recordings of job “interviews” conducted by “Sergey Petrovich” with dozens of candidate mercenaries.
The GRU Mole
Another important source co-opted for the project, according to the former operatives interviewed, was a former mid-ranking officer of the GRU, Russia’s foreign military intelligence agency, who had been compromised and recruited by Ukrainian military intelligence during his deployment to the “DNR” several years earlier. In 2019 — back in Russia and having retired — he offered to look for employment once more with the Russian armed forces, at the suggestion of his Ukrainian handlers in the GUR MOU. This ensured an inside man for the planning team who could provide both information and risk alerts. It was hoped that he would potentially be useful in further legitimising the recruitment operation.
Just like “Sergey Petrovich”, Bellingcat was not able to contact nor establish the actual identity of this GRU officer. Information about his role in the sting operation comes only from the interviews with the former operatives.
Fake Casting 1.0
With a convincing Russian intelligence asset on board, the sting could begin in earnest. The aforementioned clone of the PMC MAR website included contact details replaced by emails and phone numbers controlled by GUR MOU. To trigger incoming queries, a number of ambiguously worded job postings were placed on Russian classified websites that were known to have been previously used to recruit mercenaries.
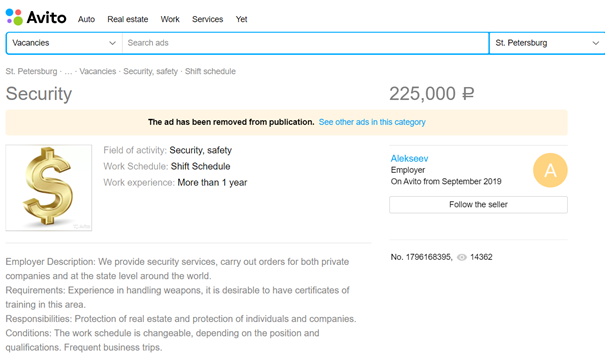
In a listing on the popular Russian classifieds site Avito.ru, under the heading St Petersburg/Security job postings, the following security position was advertised on 25 September 2019 by a user identifying himself as “Alekseev” (the original listing in Russian can be seen here, archived here).
From the context of the job applications and recorded job interviews analysed by Bellingcat, it appears that “Alekseev” was the purported “HR Director” of the fictitious PMC MAR.
The listing advertised a job paying 225,000 roubles (approx. US$3,200/ EUR 2,900) a month, suggesting an overseas posting to guard a company’s assets. Experience in weapons handling and training certificates in the same were a requirement, apparently an attempt to filter out applicants with no prior combat experience.
The employer’s page shows that it had received two critical comments, in January and April 2020. Both users complained about being asked to send their application documents to “the manager” but receiving no feedback. A 31 March response from the employer “Alekseev” noted that recruitment had finished and expressed regret about the negative feedback.
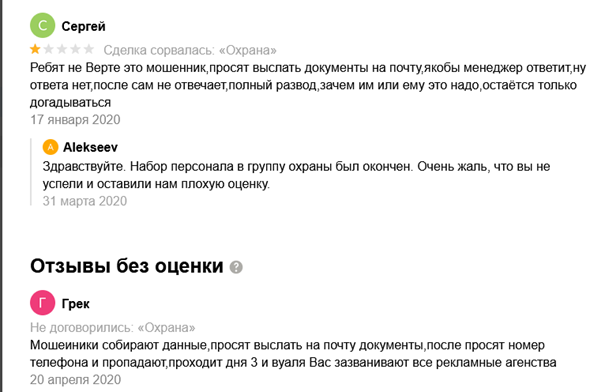
“Guys, don’t believe this fraudster. They ask you to send documents, claim that some manager will answer you, then nobody answers. They entirely distance themselves. As to why he or they needed anything at all from you, well, all you can do is guess” writes Sergey in response to the Avito listing.
According to interviews with the former GUR MOU operatives, these comments were the result of the fake recruitment campaign attracting too many applicants who were unsuitable for its goals. While some had military experience, they had not fought in the Donbas and were not of interest to Ukraine’s military intelligence. Indeed, emails sent by applicants to the email account controlled by GUR MOU, info@office-rosneft.org, and shared with Bellingcat, showed that at although they had not taken part in operations in Eastern Ukraine, at least some of them had fought in the Soviet Union’s war in Afghanistan and in the two conflicts in Chechnya after its collapse.
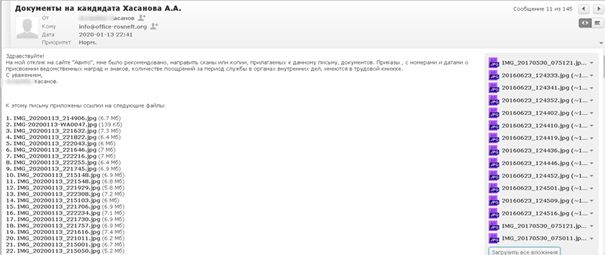
Example of an email sent by an applicant (A. A. Khasanov), including extensive attachments of documents attesting to prior military service.
According to Bellingcat’s interviewees, after receiving too many irrelevant applications mostly from people of little intelligence value, the operational team decided to change strategy. They needed a more focused approach that would yield more — and importantly more prominent — targets.
Help from the Shaman
In April 2020, a key Ukrainian special operations operative formerly with the SBU’s counter-intelligence department who had supervised the Tsemakh retrieval operation was placed in charge of “Project Avenue”, the code name that had been officially given to the sting operation, and which Ukrainian media would later dub “Wagnergate”. This officer, unlike the original godfathers of Project Avenue, came from a security background, and gave a more proactive push to the previously intelligence-driven operation.
After taking stock of the available applications and other collected intelligence, “Sergey Petrovich” began conducting job interviews with some of the most promising candidates. His task was to establish whether any of them could be used as proxy recruiters of other relevant targets, a method similar to social scientists’ snowball recruitment practice for their interviewees. To achieve this, the operatives explained, “Petrovich” was given a special untraceable telephone without a SIM card, and caller-ID spoofing software that was set to show a Syrian calling number — the mercenaries were told that their kurator was currently in Syria.
Two of the early applicants who had submitted their job applications in September 2019 seemed to fit the description. One of them appeared particularly promising: Artyom Milyaev, born in 1981. Not only had Milyaev written that he had accumulated military experience in Chechnya, the Donbas and Syria — he noted that he had been deputy commander of an assault brigade in the “DNR”, where he had commanded over 100 fighters. In his first communication with the “HR manager”, he offered to recruit from among his old subordinates. He was known to his military comrades, and by extension to Ukrainian intelligence, by his callsign “Shaman”.
In April 2020, “Sergey Petrovich” contacted “Shaman” again using his spoofed Syrian number, asking how many of his group of 120 mercenaries could be hired for the PMC MAR project. Milyaev responded that he needed to double check and call each of them again. He explained that “ too much time passed”, presumably since he first proposed his network-for-hire in late 2019, and “as many as half of them may have signed up with the Musicians”. The term “Musicians” is a coded reference to the Wagner PMC widely used in the phone calls heard by Bellingcat. Its significance, along with that of other codewords used by the mercenaries, was confirmed by Bellingcat’s Russian interviewees.
“Sergey Petrovich” then asked if there were experienced snipers among the group. “Shaman” replied that he knows five snipers with experience using 0.338 calibre sniper rifles in Syria. They also discussed the need for other experienced fighters, including artillery spotters and large-bore machine gunners.
“Shaman” is also heard asking “Petrovich” about “the money situation”, and whether the pay will be in cash or to bank cards. “Sergey Petrovich” instructs Milyaev to refer all money questions to the “email of the HR department”.
Several days later “Petrovich” called Milyaev again, apparently after the latter emailed “the HR department” that he was ready with a list of available people. In the call, “Shaman” said he was ready to serve, with a list of ten fighters, and would send a detailed roster with their names, specialisation, language skills and yellow-fever immunisation status. Milyaev requested that “Petrovich” call each of the fighters in person, so that “they can see where you call from” — a reference to the Syria caller ID — to feel confident that the operation was legitimate. Milyaev asked “Petrovich” how many positions were still available to be filled; “Petrovich” replied that as many as 50 more could be hired if they had the relevant experience.
At the end of the call “Petrovich” and Milyaev agreed on a process of working with applicants. The latter was to send “Petrovich” batches of 10 fighters at a time, and “Petrovich” would then call each of them, referring to “Shaman.” After vetting each candidate, they would be referred back to Milyaev who would collect their resumes and supporting documents via email.
In the following two months, “Petrovich” called Milyaev over 40 times (all phone calls were made available to and reviewed by Bellingcat). With each new call, “Petrovich” could be heard grooming “Shaman” to believe he would be a commander in the new operation, promising him freedom to choose his lieutenants and structure the unit as he pleases. He also offered him freedom to bring his own phone (other fighters would not be allowed). “Petrovich” could also be heard encouraging Milyaev to recruit fighters with recent combat experience, especially snipers and those with anti-aircraft and artillery spotter experience — all qualifications that would, again, likely narrow down the recruits to those who might have committed prosecutable offences while deployed in Eastern Ukraine.
By early May 2020, “Sergey Petrovich” had told Milyaev that the total project would require three platoons of approximately 50 fighters, each with a platoon commander who would report to Milyaev. Petrovich also tasked Milyaev with recruiting the first platoon that was to depart within weeks. The two agreed on a financial incentive for “Shaman” — he would get RUB 2,000 (EUR 24/$28) for each completed application form.
A Deluge of Applications
The decision to outsource the recruitment to “Shaman” quickly bore fruit for GUR MOU’s planning team. By the end of May, the fake PMC had received dozens of new applications, all citing “Shaman” as their reference. The forms sent to applicants were crafted to look like those previously used by the original PMC MAR, with each carrying the “PMC MAR” stamp that bore the name and initials of the “HR Director Alekseev” — the same name which had posted the job listings. The forms — which were ultimately completed by more than 200 applicants — contained full personal data, including current address, telephone numbers and emails, height, weight and shoe sizes, education and military experience. All have been seen by Bellingcat.

Example of a “PMC MAR” application form filled out by a mercenary. A stamp confirming receipt bears the name “A. S. Alekseev”
Following a candidate’s “approval” at the end of a casting call by the kurator, each was told to send his detailed (military) resume, along with copies of any proof of military experience, medical certificates, military references from their commanders, and scans of military awards and medals to “Shaman” along with the simple message: “Tell him you’re approved”.
The applicants duly did. By early June 2020, the two email accounts controlled by GUR MOU had received hundreds of pages of detailed, handwritten confessions as to their role in warfare in Eastern Ukraine, the Middle East and Africa, along with names of commanding officers, photos of medals issued by the Kremlin or by the two unrecognised republics in Eastern Ukraine, and even previously unseen video and photo materials of the downing of a Ukrainian military helicopter over the Donbas in 2014.

Screen grabs from phone video showing aftermath of downing a Ukrainian helicopter emailed by Denis Kharitonov (right on second photo)
The combatants’ resumes also contained direct admissions and details of how Russia’s hybrid war in Ukraine had developed. Some militants described their arrival to Donbas in 2014 as “under the cover of rebels”, while others described their presence there as direct deployments by their regular Russian army units. Crucially, the GUR MOU team started noticing names among the applicants that they knew were already wanted by their colleagues at the SBU for what they believed were serious crimes committed in 2014 and 2015 in Eastern Ukraine.
A random selection of the biographies sent to PMC MAR can be seen below:

An autobiography sent by Artyom Shatsky to PMC MAR, admitting his service with the Zarya Battalion, a militia which fought in eastern Ukraine for the “LNR” Russian-backed separatist entity, in 2014. He also acknowledges serving with a Russian motorised rifle brigade in the Luhansk region of Ukraine in 2015.
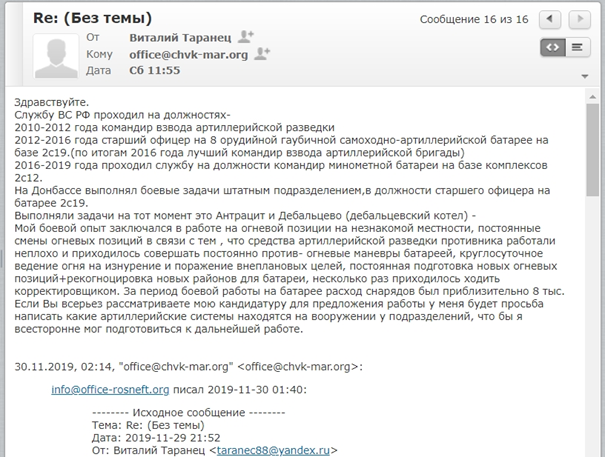
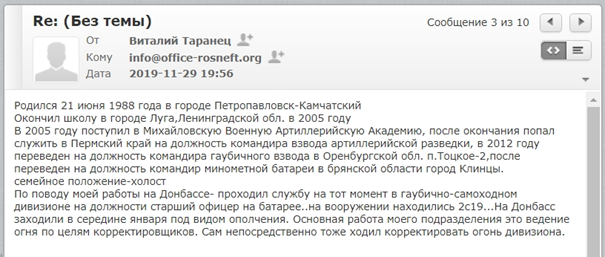
An autobiography sent by Vitaly Taranets to PMC MAR and the fake Rosneft email address, stating that he served as an officer in an artillery unit and fought in the Battle of Debaltseve in 2015.

A photo of an award confirmation sent by Alexander Rudenko to PMC MAR. It confirms that he received a medal “for the return of Crimea” from the Russian Ministry of Defence on 7 May 2014. His stated job title attests to playing a military role in the illegal occupation of the peninsula.
Many of the recruits also provided insider data on how the Russian government had provided support to and steered the operations of the ostensibly private Wagner PMC. In the presumed job interview with Alexander Krivenko, arguably the most senior officer the GUR MOU team were able to recruit, the lieutenant colonel described how in 2014 he was instructed by his regional voenkomat (the Ministry of Defence’s conscription and recruitment office) to form a battalion to fight in Eastern Ukraine. He also told “Petrovich” of his later role as a combat training chief for “Wagner”, which took him to Syria and the Central African Republic, where he served as advisor to that country’s chief of staff. Notably, he describes a previously undisclosed training program that was provided to the CAR’s chief of staff at the GRU’s Frunze Academy in Moscow. Krivenko, who at the time was serving with Wagner PMC, notes that he also attended the training.
Waiting for Petrovich
The hundreds of phone calls between “Petrovich”, Milyaev and the recruited mercenaries show that by the end of May 2020, the fictitious small private army — numbering 180 people divided into three platoons — had taken on an organisational life of its own. Recruits were jockeying for choice positions in their platoons; some were trying to circumvent “Shaman” and get promoted directly by “Petrovich”; many complained about having to wait too long for the launch of operations and for the first salaries to be paid. In one call from 31 May 2020, “Shaman” can be heard warning “Petrovich” to be wary of a particular candidate who the presumed kurator had promoted to platoon commander, as “he has a tendency to backstab and create intrigues”. One of the would-be mercenaries, unhappy with his personal situation, even threatened to complain to Russia’s security service, FSB (declassified intelligence data provided to the Ukraine’s Ad-Hoc Inquest Commission suggests the person did inform the FSB about the ongoing recruitment, but there is no evidence that the security agency acted on this tip).
Many of the recruits wanted to meet their commanders and “Sergey Petrovich” in person — and several fictitious plans were made for get-togethers in Moscow or St Petersburg. This obliged the GUR MOU team to come up with ever more implausible pretexts to delay such events. Fortunately for the organisers of the sting, in early to mid-2020 the Russian government introduced a series of Covid-19 lockdowns. These provided plausible justification for both the delay in meeting “the boss” and in the departure date for deployment. As of May 2020, all Russian airports were closed to commercial traffic until further notice.
Milyaev himself was getting impatient, having to allay the anxieties of hundreds of presumed subordinates, while himself never seeing his kurator in person nor getting any meaningful income. Although he had been promised RUB 2,000 per applicant, he had yet to receive that money so was owed RUB 320,000 (roughly $5,000). To prevent the risk of a mutiny at the top, the GUR MOU team decided to pay him this accrued fee in early June. It resulted in a freshly motivated ”Shaman”.
Still, the sting operation was becoming a logistical challenge: with 180 recruits clamouring to leave “on assignment” and requiring constant attention, “Sergey Petrovich”’s own life had turned into a 24-hour helpline, having to keep people across seven time-zones motivated and preventing them from signing up with competing mercenary projects which actually existed. Project Avenue needed to be either put to rest, or given a new lease on life.
The Death of Sergey Petrovich
On 2 June 2020, “Sergey Petrovich” was killed in action while on assignment in Syria. Or at least this was what a shocked “Shaman” was informed in an email from the self-styled Rosneft project manager.
During the following two weeks, the 180 recruits were frantically trying to figure out what that tragedy meant for their job prospects. Then Milyaev received a phone call from a Venezuelan number. The person on the other end of the line introduced himself as “Artur Pavlovich”, a new kurator who took over from “Petrovich”. Like “Petrovich”, “Pavlovich” was a GUR MOU operative; his identity has not been disclosed to Bellingcat due to his ongoing work as a clandestine operative.
Unlike “Petrovich”, the GUR MOU team decided to place “Pavlovich” not in Syria but in Venezuela, where Rosneft also had drilling operations. Тhe number used by “Pavlovich” — spoofed by the GUR MOU team using a caller-id changing app — belonged to the consular service of the Russian embassy in the Venezuelan capital Caracas. The new kurator had good news: Rosneft needed about the same number of experienced fighters to guard its facilities from bandits in the South American republic.
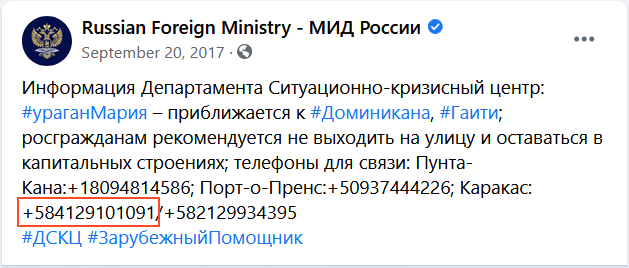
A Tweet by the Russian Foreign Ministry warning Russian citizens about the approach of Hurricane Maria towards several Caribbean countries. It provides an official number for the embassy in Caracas — the same number successfully spoofed by “Pavlovich”.
The decision to kill off “Petrovich” was made by members of the GUR MOU team as they sought to allay the mounting discontent among the fictional mercenary brigade. They had also needed to buy time to decide if — and how — to proceed with the sting operation. A new kurator, they believed, would be a legitimate justification for yet further delays.
He would inherit a roster of hundreds of fighters, would need to review every person and might also need to make changes to the mission plan. If, in the meantime, a decision was made by GUR MOU to shut down the sting operation project permanently, a new kurator could provide the cover for a graceful exit, without the fallout of the mercenaries — and potentially the Russian intelligence services — finding out they had been duped.
According to interviewed former operatives and as confirmed by the Ad-Hoc Inquest Commission, at this point in time the team members were split between people who preferred to to terminate the project, and others – led by the former SBU counterintelligence officer – who wanted to proceed with the active operation – the sting. Ultimately, the proactive scenario prevailed, and Project Avenue entered into its 2.0 phase: the active sting operation.
According to data shared with Bellingcat by the Ad-Hoc Inquest Commission, the death of “Sergey Petrovich” marked the formal termination of the intelligence-gathering project that had started in 2018.
Moving to Active Phase
The GUR MOU team used this time which they knew could not exceed a month without losing most of the recruits to other assignments, most likely with the “Musicians” of Wagner PMC, to evaluate the feasibility of continuing with the sting operation. This would require testing various operational scenarios and, equally importantly, checking there would be political support for such a daring plan.
The Final Research
Presented with 180 targets, from which they could pick a subset that would be of biggest interest to prosecutors, the team gravitated towards a mass capture of several dozen individuals. This could theoretically be achieved by forcing the landing of a plane that was carrying militants over Ukraine. But this required a very specific confluence of circumstances, especially hard to achieve with the obstacles to air travel in mid-2020 — Russian airports were in an effective lockdown and air travel in the rest of Europe was also reduced.
The team sought advice from an experienced travel agent to find out what options existed for flights out of Russia. It became clear that for most Russians trying to take flights for summer vacations, only one option remained: travelling via car or bus to Minsk in Belarus and flying from there to Istanbul, a hub that could take them to their final holiday destination.
However, even travelling to Minsk was not trivial. While in normal times there is no controlled land border crossing between Russia and Belarus, Covid-19 lockdown rules had resulted in enforced border checks. Crossing from Russia to Belarus was furthermore restricted to only three permitted reasons: medical treatment, business trip to enter employment with a Belarus state-run company or transit.
The transit option via Belarus appeared to be the most practical. The GUR MOU team decided to send a test passenger — a GUR MO asset residing in Russia — from Moscow to Minsk, using a public bus. No obstacles were expected; after all, the arriving mercenaries would have ongoing flight tickets from Minsk National Airport. The test traveller had therefore booked a flight from Minsk for the day after his entry to Belarus. However, there was a hitch when he was initially prevented from entering the country. Instead, he was taken off the bus and directed to a border-side kiosk selling travel insurance. There, he was offered a combination of travel insurance and a pre-stamped employment agreement with a Belarus state company, for a package price of RUB 1,000 ($15). As recent arrests in Belarus have shown, this corrupt scheme has since been acknowledged as a popular solution to the problem of closed borders. Once the test traveller showed border guards the freshly filled “employment contract”, he was allowed to enter Belarus.
The GUR MOU team checked off the “fake employment” route as a realistic entry mechanism for the mercenaries. Nevertheless, according to the former operatives Bellingcat interviewed, crossing the Russia-Belarus border was assessed as the highest-risk bottleneck in the whole operation. Getting the mercenaries out of Russian territory without incident would entail the entire team staying below the radar of the Russian secret services.
Planning a Plane-Jacking
Assuming the GUR MOU team were able to get the mercenaries across the border, the most crucial part of the sting was going to be the forced plane landing. That part of the plan required the most meticulous research and preparation. Not only did it need to be conducted in a manner safe for a commercial airliner and its passengers, the method also had to allow deniability while appearing to be within the boundaries of international law.
Problematic Parallels
There was international outrage in May 2021 when Belarusian blogger and opposition activist Roman Protasevich was detained after the Ryanair flight he was travelling on between Athens and Vilnius was diverted to Minsk. A fake bomb threat was called in while the plane was in Belarusian airspace and Protasevich was arrested when the aircraft touched down. Michael O’Leary, the head of Ryanair, described the incident as “state-sponsored hijacking” while Ireland’s minister of foreign affairs told NPR that it was “wrong” and “illegal”. It also led to outcry and further sanctions from the EU and US against Minsk.
In an interview with Ukraine’s 1+1 TV channel on 24 June 2021, President Zelensky would implicitly acknowledge the murky circumstances of Ukraine’s own operation by drawing parallels with the arrest of Protasevich. However, he added the caveat that the idea for the controversial operation was the initiative of “other countries”.
“And as to the fact that it failed — and once again I draw a parallel with what happened in Belarus — I think, thank God that we put our foot down on that important issue”, concluded the president.
According to the interviewed operatives, it was at this point, in mid-June 2020 that the GUR MOU team decided to bring in the expertise of a military colleague assigned to the Ukrainian Air Control Center, (UkrAeroRukh). In this expanded group, the team considered various scenarios for achieving the three goals.
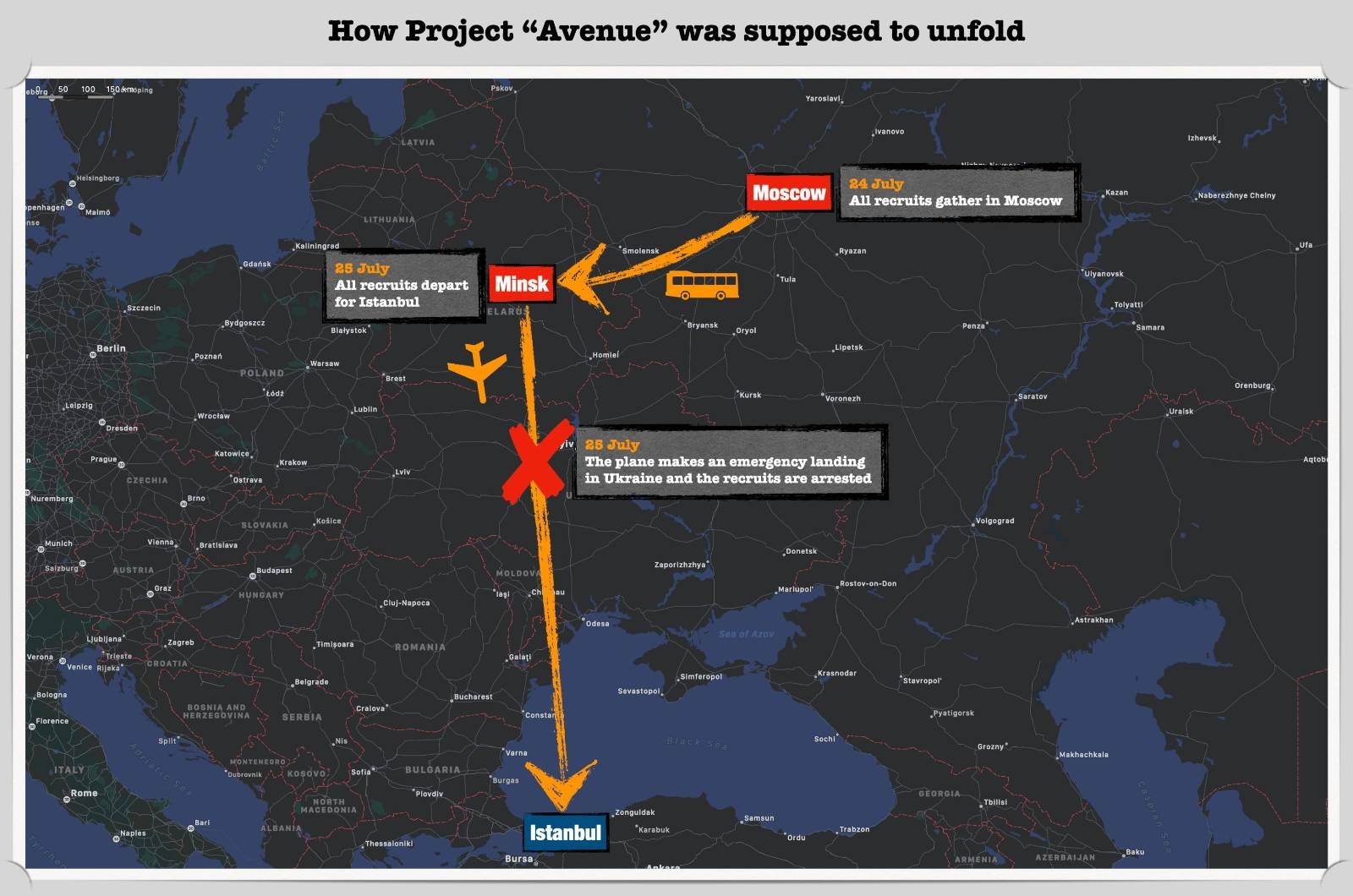
A flight path from Minsk to Istanbul appeared to be convenient: a plane on this itinerary would spend approximately 28 minutes in Ukrainian airspace — just long enough to implement an emergency landing procedure under false pretences.
However, if the plan was to work out, every second of these 28 minutes needed to be put to use.
After consulting the Chicago Convention regulating commercial air traffic, the team concluded there were only two scenarios that would allow Ukraine to legally land a plane on its territory. The first scenario was a medical emergency: if a passenger on board the flight required immediate medical care, for example as a result of a heart attack, the plane would have to make an emergency landing at the nearest airport. Technically, the nearest airport after crossing over into Ukrainian airspace would be one of the two in Kyiv. However, the distance from the Ukrainian border to Minsk airport was not significantly longer, running the risk that the pilot might instead choose to return to Belarus. This rendered a medical emergency far too risky if the sting was to succeed.
The second scenario was a bomb threat on board. In this scenario, once the respective ground control had been informed of the threat, it was within its discretion to instruct the plane to land on an airport of its choosing — as the hypothetical risk from an explosion extended not only to the passengers but also to the population on the ground. Moreover, under international law, Ukrainian air control authorities could instruct the pilot to not inform passengers of the emergency, or even of the change of flight path. As this appeared a more convenient and less risky option, the GUR MOU team made a choice to go with it.

Warnings to be issued to pilots of flights over Ukrainian airspace in the event of emergency landings. . Source
A preliminary operational plane was conceptualised for this scenario. It would require that someone physically located at Minsk airport phoned in a warning to Ukraine’s air traffic control, alerting them that they had a credible reason to believe a bomb was placed on board the respective flight. In this particular case, the cover story would be that this individual had overheard two male passengers in the airport cafe discussing their hostility to Ukraine and appearing to discuss a terrorist act onboard the flight. The call would have to be made just as the airplane was entering Ukrainian airspace.
To minimise the risk of leaks, and maximise plausible deniability, the GUR MOU team decided to only involve a small core group of colleagues from law enforcement.
The Political Go-Ahead
By the second half of June 2020, the GUR MOU team had 180 willing mercenaries ready to leave Russia on what they thought would be a well-paid overseas mission lasting several months. With the change of kurators, the cover story for the mission had also changed — “Artur Pavlovich”, unlike “Sergey Petrovich”, was responsible for the security of Rosneft’s oil wells in Venezuela, therefore the former fighters were being prepared to leave for the South American nation.
However, it was clear to the operatives that capturing all 180 mercenaries would be unfeasible — for one thing, as many Russians began flying out via Minsk to summer destinations, tickets for flights to Turkey became scarce. It would also be counter-productive: many of the mercenaries who had signed up were of scant interest to Ukrainian law enforcement, having either no or limited fighting experience in Eastern Ukraine and no proven “kills” for which they could be prosecuted. Furthermore, the apparent crimes of many applicants were only known from their own claims made during the recruitment process, some of which could well have been exaggerated. The GUR MOU team estimated they could only realistically aim to capture about 40 mercenaries that could plausibly be added to the “initial platoon” to be deployed to Venezuela.
To this end, “Artur Pavlovich” reconfigured the command structure of the 180 mercenaries by splitting them into four platoons of roughly 45 members each. “Shaman” would retain command over the company of 180 but would also lead the first platoon that would leave, while other senior fighters — including Lt. Col. Krivenko — would be in charge of the other platoons. According to the cover story, the platoons were going to depart to Venezuela sequentially, with a few days gap between departing batches. Logically, only the first platoon were likely to ever depart — and be captured — thus the focus was on deciding who went into that group.
The GUR MOU team needed the SBU’s help in drafting the short-list of the mercenaries that were most important to Ukraine from a law-enforcement perspective. However, they were unable to directly task the domestic intelligence agency – they needed this to be done by the country’s political leadership.
According to the interviewed operatives, this was not the only reason GUR MOU needed the involvement of the Office of the President. What they were preparing was a high-stakes sting operation, probably one that would significantly escalate tensions between Ukraine and Russia. They needed the approval of the country’s political leadership.
According to interviewed former operatives from GUR MOU, the Ukrainian President was first informed of the proposed sting operation on 15 June 2020, during the regular Monday security briefing with the chiefs of the intelligence services. The interviewees told us that President Volodymyr Zelensky endorsed the operation in principle on 26 June 2020, and requested a fleshed-out plan to be prepared. That concept plan, according to the former operatives, was prepared and approved by the then Minister of Defence on 1 July 2020.
Bellingcat requested a confirmation of the former operatives’ contention that the proposed plan was approved by the President, both from the Office of the President and from the current director of GUR MOU, Kirillo Budanov. Mr. Budanov replied that while the intelligence agency cannot comment on individual cases due to their classified nature, the agency’s director does not need formal approval from the Office of the President. He did confirm however that the Director of GUR MOU visits the Office of the President on a regular basis and informs him, in his capacity of Supreme Commander, of the fulfilment of the agency’s tasks. The Office of the President did not respond by press time.
In the telling of the former operatives, from the moment the active phase was approved by the Minister of Defence and presented to the President, there were regular update briefings to the President on the progress of Project Avenue by the two senior officers in charge of the project: Vasily Burba, then director of GUR MOU, and Ruslan Baranetsky, deputy director of the SBU.
Involving the SBU
Once the go-ahead was given, the GUR MOU team could begin sharing data and coordinating the plan with their colleagues from the SBU, Ukraine’s domestic security agency. The SBU serves both as a domestic intelligence and as an investigative body for major crimes such as terrorism; thus alleged crimes committed during wartime in Eastern Ukraine fell within its jurisdiction. SBU investigators had compiled terabytes of data on fighters in the Donbas, including hundreds of thousands of intercepted phone calls. These investigators, the GUR MOU team thought, would be best suited to assess the importance of each of the mercenaries from the angle of criminal prosecution. They could also validate some of the self-confessed war stories by trying to match them to telephone intercepts.
In order to leave nothing to chance and to prevent possible digital leaks, the GUR MOU team decided not to share any of the gathered data digitally with the SBU. Instead, according to the operatives interviewed, in the last days of June 2020 the GUR MOU team leader delivered to SBU several large bags bulging with manila folders containing each mercenary’s personal file.
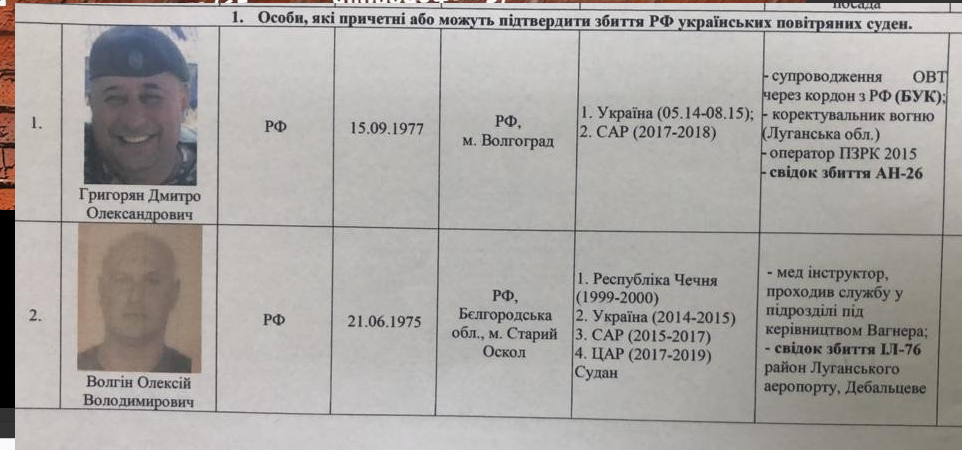
The SBU colleagues did not take long to let GUR MOU know that they were sitting on a goldmine — not only were most of the self-described roles in battles in Eastern Ukraine validated by phone intercepts, but many of the people on GUR MOU’s list were already on the SBU’s shortlists of wanted terrorists. Among them were fighters who had taken part in the crucial battles at Ilovaisk and Debaltseve that had cost the lives of hundreds of Ukrainian soldiers. Others had taken part in the June 2014 downing of a Ukrainian military transport plane near Luhansk carrying 49 troops — all of whom were killed. Importantly, at least two of the mercenaries claimed to have used sophisticated, Russia-provided anti-aircraft weaponry in and around a location near Snizhne on certain days that might make them useful witnesses in the ongoing MH17 trial. One of the mercenaries had even spoken of having escorted a BUK Telar across the Russian-Ukrainian border — an anti-aircraft weapon of the same type as of the one that shot down MH17 – in early July 2014. He had also named a senior Russian general who had supervised the border crossing of the weapon.
The SBU team quickly prepared their own shortlist of persons of interest — it numbered 28 individuals. To the GUR MOU team this was a convenient number: they would pad it up to approximately 45 with mercenaries who did not have Ukrainian fighting experience in order to prevent the platoon members becoming suspicious if they realised they were all Donbas veterans.
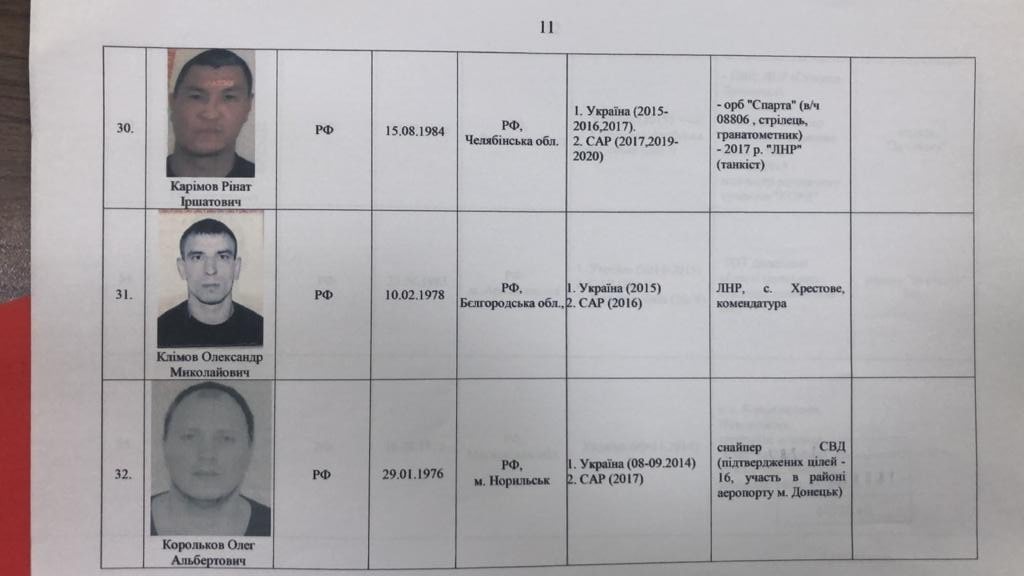
Excerpt from the SBU shortlist, section caption: “Individuals who are complicit or could provide evidence on shooting down of Ukrainian aircraft by the Russian Federation”
Deniable Operationalising of Intelligence
At the end of June 2020 the GUR MOU and the SBU had agreed on the importance of conducting the sting operation and were working together. However, to assure the operation’s long-term success, they needed to ensure it was deniable — i.e. that the SBU, as part of law enforcement, did not formally take part in a sting operation that involved diverting a passenger plane, thereby potentially violating international law. Instead, it had to appear as though they simply took action to arrest persons of interest once they accidentally ended up on Ukrainian territory.
To achieve this tactical goal, the two teams plotted a sophisticated ruse: an anonymous whistleblower would inform the SBU tipline of an ongoing unlawful mercenary recruitment operation, and would provide it with the email address — including login details — of the info@rosneft-office.org email account. Once the SBU responded to such a tip, they would land in the middle of the whole virtual PMC — and would be able to download all thousands of pages of incriminating documents, including resumes, photos and videos. The SBU would also be able to track the preparations for the departure of the mercenaries from Russia — with the aid of tickets and flight plans. They would be able to react immediately once they discovered that — accidentally, following a bomb alert — the plane carrying these persons of interest had landed at Boryspil International Airport near Kyiv.
The SBU would also be able to obtain court-approved arrest warrants for the mercenaries and place them on detention lists across the national border and police databases — ensuring that once the plane landed in Ukraine and border guards started processing the passengers, all of the targets would trigger arrest alerts. The detainees would be handed their indictments immediately upon arrest.

Scan of a report to the Director of the SBU’s Investigative Department from 13 July 2020, informing him of the discovery of an unlawful recruitment by a certain “Sergey Petrovich” on behalf of PMC MAR, as well as of a list of the initial 47 mercenaries prepared to be deployed overseas.
The Trip Begins
Back in Russia, hectic preparation for the upcoming trip to Venezuela was in the works. “Artur Pavlovich”, the new fictitious Venezuela-based kurator, had given Shaman instructions to gather the initial advance platoon of 47 people. The GUR MOU team also provided Shaman with an initial “business trip” budget of per diems for the first platoon. To disguise the money’s origin, funds were first delivered to Russia through a network of GUR MOU assets, including citizens of Chechen origin, and subsequently wired to the end recipients from Russian territory using Russian money transfer services.
Finding 47 tickets on a flight from Minsk to Istanbul in July, however, proved problematic. Using the Ukrainian travel agent co-opted by the team, 34 tickets were found on a flight leaving for Turkey on 25 July, while an additional 13 tickets were found for a flight two days later.
An initial group of 34 mercenaries was selected (again, with a view to retaining a high ratio of “persons-of-interest” to those with no links to warfare in the Donbas) to fly on 25 July. The remainder were told they would travel on the later flight.
Thirty-four tickets from Minsk to Istanbul were thus purchased on 15 July for the first flight 10 days later. The planned return date was 19 October, with tickets reserved to fly from Istanbul directly to Moscow (Covid-19 restrictions permitting). This was in line with the cover story that the initial deployment would be for a three month period. For plausibility, another set of return tickets was booked for the second group of 14 mercenaries, although it was known they would never be used.
“Shaman” — who would travel as the leader of the initial cohort — created a WhatsАpp group chat called “1st Group 🇷🇺”, which served as a coordination platform for the 34 travellers. He instructed the group’s members to gather at Moscow’s central bus station at 8:00 am on 24 July, where a bus would transport them to Minsk. They would arrive late that evening and would go directly to the airport where they would depart the next morning at 10:50 am.
Thirty-three members of the first group made it to Moscow on time, although one of them — Igor Tarakanov — got cold feet at the last moment and failed to show up. Milyaev handed each their per diem, fake employment contract with a Belarusian company, print-outs of their electronic tickets and a copy of the group travel insurance. Everything appeared orderly and professional. The provision of per diem money appeared to allay some of the concerns which had accumulated after many weeks of delays and changes to plans.
The bus with the mercenaries left for Minsk at 9:00 am.
A Change of Plans
What the mercenaries were not told was that by the time they had left for Belarus, the departure plans from Minsk had already changed, and their bookings for the onward flight to Istanbul had been cancelled.
The two senior security commanders in charge of Project Avenue — GUR MOU’s Burba and the SBU’s Baranetsky — arrived at the President’s Office on the day before their mercenaries’ departure, according to Vassily Burba and former operatives who say he called them immediately after the meeting. Burba and Baranetsky intended to present a final status update on the impending sting operation. As President Zelensky was busy at that moment, however, Burba told Bellingcat that they could not meet him in person.
According to Burba, the head of the Office of the President, Andriy Yermak, proposed a postponement of the operation by a week. The previous day, President Zelensky had reached an agreement with Russia and Russia-supported separatists for a ceasefire in Donbas, an achievement which he announced at a joint press event with the then President of Switzerland, Simonetta Sommaruga. The ceasefire, which still needed the sign-off of the Normandy Four nations (comprising Russia, France, Germany and Ukraine) that aim to resolve the war in Donbas, would enter into force on 27 July 2020. According to Burba, the position of the Office of the President was that if the sting operation would continue as planned and culminate in detentions on 25 July, the ceasefire would be dead before it started.
Bellingcat could not independently verify this conversation, and the Office of the President did not provide comments for this investigation.
Burba said he replied that a delay of a week was not feasible and would result in either loss of confidence from the recruits, or in suspicions being raised among Belarusian or Russian counter-intelligence services, or both. Burba said representatives of the Office of the President, trying to meet the GUR MOU team halfway, then proposed to shorten the delay to four days – with the departure and capture moved to Wednesday, 29 July 2020. This would have allowed the ceasefire to at least enter into force. According to Burba, the intelligence chiefs surmised that finding a new set of tickets at such short notice were slim, but promised to see what could be done.
This second conversation, like the first, could not be independently verified by Bellingcat.
The next morning, as the first group of 33 were already leaving Moscow, the GUR MOU team were able to successfully rebook their tickets not for Wednesday 29 but for Thursday, 30 July. The second group of 13 mercenaries had their tickets changed to Saturday, 1 August. Later that morning Burba said he reported to the Office of the Presdient that the plan was still on, albeit with a five-day delay.
Enemies Within and Without
Yet as the bus with the 33 mercenaries departed, all was not well in Belarus. Presidential elections were scheduled less than two weeks later, on 9 August, and the political mood was tense. Fearing enemies from within and without, Belarus’s incumbent president Alexander Lukashenka was cracking down on his perceived rivals. Belarus’s domestic intelligence agency, the KGB, had already jailed the main opposition figure Syarhey Tsikhanousky just two days after he had announced his candidacy. On 15 July, however, his wife — Sviatlana Tsikhanouskaya — entered the presidential race amid widespread international support and sympathy for the country’s opposition.
Lukashenka’s paranoia was not limited solely to supposed Western plots to displace him. He also reportedly feared a treacherous intervention from his sole ally, the Kremlin. At an off-the-record meeting with members of the Belarusian media on 9 July, Lukashenka reportedly said that four GRU officers had been detained in the country, and that they had “worked in coordination with [opposition leader] Syarhey Tsikanousky”. At a video of a speech to Belarusian Spetsnaz officers on 24 July (since deleted from the President’s website but still available via an archived version), he spoke of unspecified external forces that might try to create “a Maidan” [popular uprising] by use of “professional soldiers” working for big money in private military companies and experienced in “creating provocations around the world”.
On the afternoon of 24 July 2020, as Lukashenka was making his bellicose speech, just such a group of 33 experienced mercenaries coincidentally arrived at the Belarusian border.
According to members of the mercenary group interviewed by Bellingcat, their initial attempt to cross the border using the fake contracts did not succeed. Despite carrying documents that were more or less identical to those used by the previous GUR MOU test-passenger they were told the documents were not in order. Belarusian border guards asked where the men were going. Some of the mercenaries jokingly answered they were all going to see their sick grandmother in Minsk.
Yet after a short wait at the border, it became apparent that the same corrupt procedure used by the test passenger would work once more. All 33 were sold “correct” employment contracts at 1,000 RUB each and were allowed to cross into Belarus.
33 Sober Men in Minsk
Once on Belarusian territory and on their way to Minsk, “Artur Pavlovich” informed Milyaev of the change of plans, and directed the bus to a three-star Minsk hotel where the travel agent had booked the men to stay for the first night of the five-day wait. Initially, after finding out about the delay, the men were upset. But after “Shaman” received a confirmation from “Pavlovich” that their sojourn in Minsk would be treated as paid employment, they relaxed and followed the strict instructions to comply with military discipline, not to drink alcohol and not to loiter around in town.
Due to an occupancy shortage, however, the men could not stay at the downtown hotel for longer than two days. On 27 July, 32 of the 33 present were relocated to “The Belarusochka”, a health resort just outside the city boundaries. The remaining mercenary — the only one who also held a Belarusian passport — stayed with his relatives in Minsk.

Address registrations of one of the mercenaries, Vladimir Li, Vladimir Li, at the two hotels. Data provided by hacktivist group Belarus Cyber Partisans.
For the next three days, the men followed strict discipline and instructions from “Shaman”. As a hotel employee quoted by Belarusian media would later say: “the Russian men stood out by the fact that none of them visited entertainment establishments or consumed alcohol.”
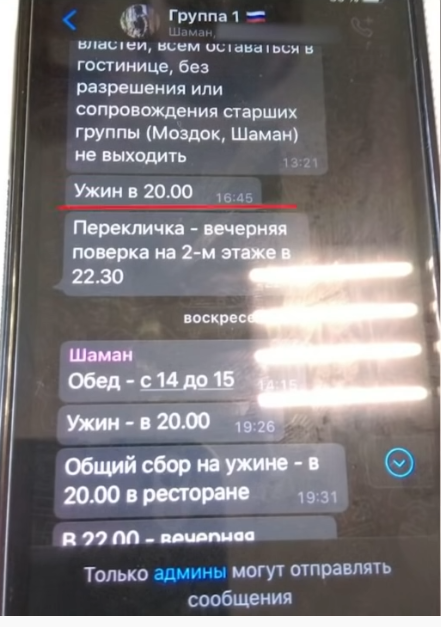
Screenshot from the WhatsApp chat group: “1st Group”. Instructions from Shaman include: Everyone should stay in the hotel and leave only with permission of the senior commanders (Mozdok or Shaman); lunch from 14:00 to 15:00, dinner at 20:00 and roll call at 22:30, etc. Source: Screengrab from the Belarus-1 state TV channel’s report on the aftermath of arrests, 29 July 2020.
The Arrest
At about 7:00 pm on 28 July, one of the mercenaries interviewed by Bellingcat said he and his comrades noticed an unusual minibus parked near The Belarusochka. They immediately recognised it as a surveillance vehicle from the KGB. They did not attribute great significance to it, assuming that the Belarusian intelligence services were just keeping an eye on the mercenaries and making sure they left the country without causing any trouble. After all, our interviewee told us, “given the all-pervasive presence of the KGB in Belarus, they would definitely have been aware that we were booked on a flight two days later, on 30 July”.
However, later that night, there was to be a dramatic and unexpected surprise for the 32 mercenaries. Just before dawn, at 4:30 am, a Spetsnaz team from the A-Group of Belarus’ KGB raided the hotel, launching stun grenades into the Russian mercenaries’ rooms through their balconies. The balaclava-clad assault team handcuffed the Russians at gunpoint. They then made them lie on the beds face down and covered their heads with pillows, while — according to at least one mercenary who claimed in an interview with RT that he could see what was happening through an opening under the pillow — they ransacked the Russians’ luggage and clothes looking for weapons.
After no weapons were found, and a long wait, a team from the OMON special police force arrived and took the Russians to the district police department. The 33rd recruit — who had stayed with his relatives — was detained later that morning.
The mercenaries were held at the police department, handcuffed, kneeling and facing a wall, for 22 hours.

Belarusian security services detain the mercenaries at their place of residence outside Minsk. Footage from Belarus-1 state TV channel’s report on the aftermath of arrests, 29 July 2020.
Just before midnight on 29 July, they were read their arrest and charging papers. The mercenaries were then moved to a central police department where they were interrogated by what appeared to be KGB officers. The interrogators asked the detainees if they knew Syarhey Tsikhanousky and Mykola Statkevich — another Belarusian activist and presidential candidate who had been jailed at the end of May. The mercenaries said they knew of no such people. According to one mercenary who spoke to Bellingcat, the questioners appeared sincere in their conviction that they were dealing with would-be coup plotters, and at one point even asked if it was possible that the mercenaries were not aware that they were going to be used to overthrow the government. Others from the group expressed the same view in the aforementioned RT newscast.
Despite their earnest denials, the mercenaries were charged with plotting to overthrow the government and cause public riots in cooperation with detained opposition figures Tsikhanousky and Statkevich.
ALTUKHOV A.V., VOLGIN A.V. KOZHEVNIKOV A.Y., LI V.A., MASLOV S.A. MILYAEV V.A. AND OTHER PERSONS, ACTING DELIBERATELY, AS A GROUP OF PERSONS BY PRIOR COLLUSION, BEING IN THE REPUBLIC OF BELARUS, INCLUDING MINSK AND MINSK REGION, HAVING DISTRIBUTED ROLES AND COORDINATED ACTIONS, IN THE PERIOD FROM NO LATER THAN MAY 2020 TO THE PRESENT TIME, CARRIED OUT ACTIVITIES TO PREPARE FOR PARTICIPATION IN MASS DISORDER, ACCOMPANIED BY VIOLENCE AGAINST PERSONS, VIOLENT MAYHEM, ARSON, DESTRUCTION OF PROPERTY OR ARMED RESISTANCE TO REPRESENTATIVES OF THE AUTHORITIES.
— Excerpt from Belarus’ criminal database, courtesy of hacktivists Belarus Cyber Partisans

Detention and indictment documents presented to the 33 mercenaries; copy issued to and obtained from one of the mercenaries interviewed by Bellingcat
Wanted by Ukraine
On the day of the arrests, Belarusian state TV aired the now infamous footage of the detention. Lukashenka made a public statement accusing the Russian mercenaries of having arrived to interfere with the upcoming elections and gathered the Security Council for an emergency meeting. In the following days, he would dangle the 33 detained mercenaries before both the Ukrainian authorities and the Kremlin, suggesting he was indifferent as to which country got them in the end, and inviting each to make its case for receiving the captives.
As soon as news of the arrests came in, both interviews and leaked documents show, the Ukrainian authorities changed tack. They moved to persuade Belarusian officials to release the detainees into Ukrainian custody. This required both a formal line of attack — preparing all legally required charges and extradition documents — and an informal engagement with Minsk in an attempt to coax Lukashenka into handing over all or at least some of the detainees.
The formal approach included serving the detainees with an indictment, then informing Belarus through legal channels that the men had been charged with serious crimes in Ukraine. Extradition requests were also filed. Based on interviews with members of the mercenary group, some — but not all — of the 33 received notices of criminal charges brought against them in Ukraine via registered mail to their home addresses. The charges were dated 29 July 2020 — the date of the Minsk arrests.
On 30 July 2020, the Belarusian foreign minister summoned Ukraine’s interim ambassador to Minsk to inform him of the arrests and to request information from Ukraine on possible crimes committed by the men on Ukrainian territory.
On 3 August, the General Prosecutor of Ukraine submitted to Belarus a request for a temporary arrest of 28 of the 33 men, pending a formal extradition request. The formal extradition request was submitted eight days later, on 11 August 2020.
Meanwhile, Ukrainian authorities busied themselves with informal engagement on at least two fronts. According to one of the interviewed members of the GUR MOU team, the SBU provided their Belarusian counterparts with information on the mercenary background of the 33 men, as well as on the remaining men “recruited” by PMC MAR. It is likely that this tip was the origin of the statements by authorities in Minsk on 30 July that they were searching for up to 200 more men from what they called “PMC Wagner” on Belarusian territory.
In addition, President Zelensky personally lobbied for the extradition of the men to Ukraine in a phone call to President Lukashenka on 5 August 2020.
Wanted by Russia
Russian authorities initially appeared taken aback by the arrests and at the accusations Lukashenka levied at them. Initial reactions both from Kremlin officials and from Kremlin-friendly media indicated confusion about what the 33 men were doing in Minsk. After a day of silence, Russian President Vladimir Putin’s senior aide, Dmitry Peskov, commented on the arrests on 30 July, dismissing accusations that Russia had attempted to destabilise the situation in Belarus in any way, asking Belarus for “exhaustive information on what the Russians [were] accused of’. In a statement posted on Russia’s Ministry of Foreign Affairs website, Moscow’s ambassador to Minsk insisted that the Russians were members of a private security company waiting for a plane en route to a third country. On 31 July, Putin met the national security council to discuss the case, but the generic Kremlin press release following the meeting said little about what had actually transpired.
Several Russian citizens who had commanded self-styled “volunteer” militant units in Eastern Ukraine made statements in support of the detained mercenaries. Acknowledging that some of them had fought under their command in Eastern Ukraine, they hypothesised that they were en route to a third country for an assignment as part of a PMC. Even a war-focused Telegram channel popular with former mercenaries explained the Russians’ stay in Belarus with reference to the complex routing needed from Moscow to Caracas in times of Covid-restricted travel.
As late as 3 August 2020, Kremlin officials seemed unaware of the true backstory of the 33 Russians’ predicament, as both Peskov and Russia’s consul to Minsk made statements that the men were members of a private security company “on the way to a deployment to a third country” and had simply missed their flight.
These initial Russian statements were bluntly dismissed by Belarusian officials. No Russian PMC would arrange travel to a third country via Belarus without its handlers — “from FSB or GRU” — first liaising with their Minsk counterparts, countered the chairman of Belarus’s security council Andrei Ravkov.
Just as Ukraine had done, on 5 August 2020 the Russian general prosecutor submitted a formal request to the Belarusian prosecutor’s office to hand over the 32 detained Russians to Moscow . The sole Belarusian citizen was apparently not included.
The Denouement
As of 6 August 2020, Belarus’s president appeared ambivalent about whose pleas to honour. He even invited the general prosecutors of Ukraine and Russia to come to Belarus and “solve the case with the Belarusian prosecutor-general based on international agreements”.
However, subsequent events appeared to have influenced his final choice.
While Russian authorities and intelligence agencies initially appeared to be at a loss as to how the 33 Russian mercenaries had ended up in Minsk, they seemed to have cracked the case a week later. Using its unimpeded access to the internet logs of Russian providers, Russia’s FSB had been able to trace the Ukrainian connection to at least part of the operation. This included the IP log data for the original job posting on the Avito classified website and the Ukrainian registration of one of the travel agencies that had booked tickets for the mercenaries. The discoveries were published in the pro-Kremlin newspaper Komsomolskaya Pravda which openly referred to Russian intelligence services as the source of the findings and published an interview with a disguised FSB officer. On the same day, Russia’s investigative committee began looking into the case.
The following day, President Putin called President Lukashenka to discuss the situation with the detainees. However, Lukashenka seemed undeterred. As late as 9 August — the day of the presidential elections in Belarus — he was repeating that he did not believe the Russian narrative about the role of a “third country” in the arrival of the mercenaries.
Yet what followed the presidential election was unprecedented in Belarus’s history. Mass protests and anti-government rallies broke out around the country in defiance of what many Belarusians thought were rigged elections.
It is not known what shuttle diplomacy and negotiations between Moscow and Minsk took place over the next few days, nor whether Russia offered and provided assistance to Lukashenka in quashing the mass protests. However, at least three Russian military and/or FSB planes made previously unannounced trips to Minsk in the week following the elections, including two flights on 12 August.
On 14 August, Russia’s General Prosecutor announced that Belarus had released the 32 Russian citizens to Russia and that they were on Russian territory. The announcement, which has since been deleted from the prosecution’s website (but can be read in archived form here) appears to have been premature. Mercenaries interviewed by Bellingcat said they were only released to Russia on 16 August, and were bussed to a location near Moscow where they were placed under a 14-day quarantine. During these two weeks, the mercenaries said, the 32 Russian men were interrogated repeatedly by FSB officers trying to piece together exactly what had happened since the first mercenary had answered a job posting on a Russian classified website nearly a year earlier.
Primary author Christo Grozev, with contributions from Aric Toler, Pieter van Huis, and Yordan Tsalov
*Correction: An earlier version of this story mistakenly referred to Artyom Milyaev’s Covid-19 immunisation status when Milayev was instead talking about his yellow-fever immunisation status. This article has been updated to reflect this.