The GRU Globetrotters: Mission London
In a series of previous investigations, Bellingcat and the Insider identified the two key suspects in the Novichok poisoning of Sergey and Yulia Skripal, and the subsequent poisoning death of Dawn Sturgess. We identified the two suspects, who travelled under the fake identities of Alexander Petrov and Ruslan Boshirov, as Russian military intelligence (GU/GRU) officers Anatoliy Chepiga and Dr. Alexander Mishkin, both having rank of colonel and both recipients of Russia’s highest military award.
Bellingcat subsequently identified a third GRU officer who travelled to London during the Salisbury poisoning operation under the cover identity of Sergey Fedotov. We established that his real name is Denis Sergeev, and that his rank was at no lower than colonel, and possibly Lt. General or Major General. While Sergeev’s exact role in the operation was not known, taking into account his seniority and pattern of prior international operations, we assessed that he was in a senior position to Chepiga and Mishkin, and was likely in charge of coordinating the Salisbury operation.
In a series of follow-up investigations conducted in cooperation with international media organizations, we have attempted to uncover more details on Sergeev’s role in several international GRU operations.
This first installment is conducted in cooperation with BBC’s Newsnight.
Newly obtained telephone metadata logs from a telephone number registered in the name of the (cover) persona “Sergey Fedotov” has allowed us to analyze Denis Sergeev’s telephone usage – including calls and data connections – in the period of May 2017 – May 2019. The data – and especially the cell-ID metadata that we have been able to convert to geo-locations – allowed us to recreate Sergeev’s movements. These movements were both in Russia and abroad, as well as his pattern of communications during his overseas operations. Bellingcat obtained the telephone metadata records from a whistleblower working at a Russian mobile operator, who was convinced s/he was not breaching any data privacy laws due to the fact that the person to whom this phone number was registered (“Sergey Fedotov”) does not in fact exist.
- Based on the analysis of Sergeev’s telephone movements within Moscow, we have established that his daily routine involves trips from his place of residence to several locations housing GRU operations. These include the GRU headquarters at Khoroshevskoe Shosse 67B, and the GRU Academy at Narodnoe Opolchenie 50.
- Notably, Sergeev’s daily routine shows unchanged pattern of travel to these GRU locations from 2017 through the end of 2018, validating our hypotheses that he was in the employ of the GRU at the time of the Skripal poisoning.
- The telephone metadata produced further, unexpected evidence validating our identification of Denis Sergeev as the real person behind the “Sergey Fedotov” cover persona. This extra proof came in the form of a stray phone call from a telephone number registered in the name of Denis Sergeev’s wife, to the number registered in the name of “Sergey Fedotov” .
- Our reporting partner BBC has established via its own sourcing that Denis Sergeev has a rank of Major General. This, along with our prior assessment of his seniority to the Mishkin/Chepiga team and with the objective telephone records from his trip to London, presented below, validates our assumption that he was involved in the Skripal operation in a supervising, coordinating role; communicating back and forth to Moscow, while leaving the suspected Chepiga/Mishkin hit-team to work in an operational “Faraday cage”.
The Impulsive Traveler
On the morning of Thursday, March 1st 2018, Denis Sergeev was working from his new home, a 7-minute walk from the GRU Academy where he had worked – and lived in a dormitory-style apartment with his family – for almost 10 years. His new apartment was on a street named, somewhat imprudently, after a famous German spy who during World War II had passed on information about Hitler’s plans to the Soviet Union.
At 10:51 Sergeev, using a phone issued in the name of his cover identity, made a call to a number registered in the name of another non-existing person, a fictional Timur Agofonov. Whatever he had to say was short, as he hung up after 9 seconds. The rest of the day Sergeev stayed at home, browsing the internet and waiting.
Just after 6 pm, Denis Sergeev got the confirmation that he was expecting: he had to fly to London for the weekend. Not with his wife, and not under his real name, but as “Sergey Fedotov” – a department manager at a GRU front company offering courier services. Operational security protocol required that he himself book his ticket, lest traces to his employer – the GRU – remain in any of the booking systems.
Sergeev called a couple of travel agencies searching for a last-minute ticket to London for the next morning. For whatever reason – maybe the flight was sold out – it took them a while to confirm a booking. Only at 20:09 he got a call back from a travel agent situated about 2 kilometers from his home confirming that he had a ticket for the next morning.
Sergeev dialed *100# on his phone to check his prepaid credit. There was enough cash on the account, but he realized he needed to activate a roaming package plan for his trip, as he knew he would have to receive and send a lot of data files. But he left that chore for the morning – he had an early flight to catch.
The next morning Sergeev arrived at Sheremetyevo airport just before 6 am. His Aeroflot flight was scheduled to depart at 8:15 but he had to be at the airport early as he had luggage to check in. Disappointingly, at about 7:30 he got a text message from Aeroflot informing him that his flight would be delayed by an hour. An hour later, another text would extend the delay to two hours.
Sergeev used the waiting time to send a few messages and download some large files. In the two extra hours he was forced to wait, he exchanged several messages using Telegram, Viber, WhatsApp, and Facebook messenger, and downloaded 3 large files. At 9:15 he got a call from “Amir”, and they spoke for about 3 minutes. 45 minutes later, just before he finally boarded the Airbus A321, he called Amir again to tell him he was finally taking off. He would speak to Amir – and only to him, many times during the next three days.
An Uninterested Tourist
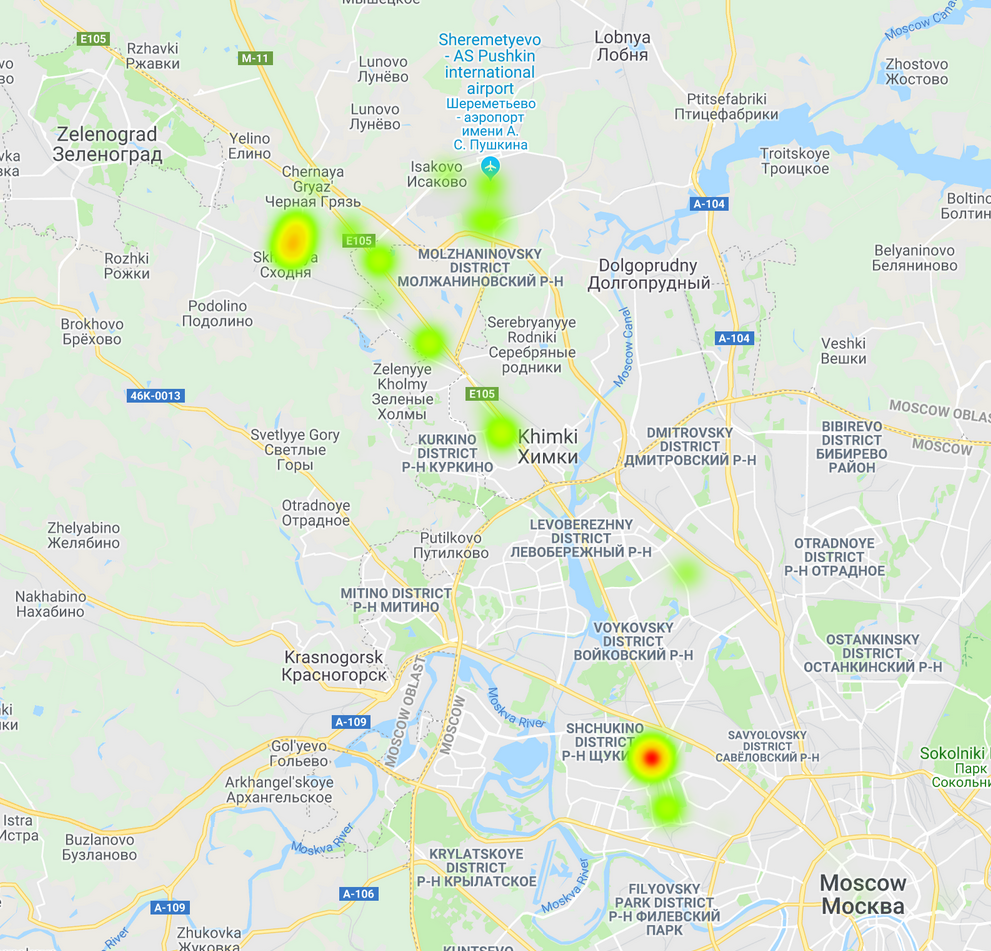
Both airline data and the telephone metadata confirm that Sergeev landed at Heathrow at 10:33 local time. It took him just over an hour to start moving from Heathrow’s Terminal 4 to downtown London. Telephone metadata pinpoints him at Heathrow latest at 11:50, following which it took him 37 minutes to get to the Kensington area another 15 minutes to get to his final destination, a hotel near Paddington Station.
Timeline of Sergeev’s movement on March 2, based on cell-tower connections. Number in circle signifies sequential connection, number next to circle shows number of connections.
His phone connected a number of times during his trip from the airport, suggesting he did not take the underground which typically has no phone coverage. The trajectory of the route taken, and the time it took him implies he most likely traveled by car. He checked in at his hotel at about 12:35 pm. Due to the coverage range of cell-towers, it is not possible to establish which exactly hotel he stayed at; however, it is practically certain that the hotel was within a few hundred feet from Paddington.
Over the following 2 days, and until his departure on Sunday morning, Sergeev barely left his hotel room, except for a short trip on Saturday morning.
The Great Communicator
While Sergeev did not show interest in seeing the sights of London, he spent a significant volume of time on the phone and online. Based on the data traffic of his phone, it appears that he did not trust local WiFi connections and instead used his 3G/4G telephone connection. The total data consumption for his 48-hour trip exceeded 1 GB.
Due to the specifics of data logging while in roaming, it is not possible to differentiate between different forms of data use – thus we do not know how much of Sergeev’s online time was spend on encrypted messengers vs downloading and uploading files and browsing. However, based on his observed use of messaging apps while in Moscow, we can assume that at least part of the time he was online he communicated via his preferred set of messengers – Telegram, Viber, Whatsapp and FB Messenger.
At least some of Sergeev’s data use can be plausibly identified as large file transfers, based on the size of the data transfer and the time it took to complete. The file size of some transfers matched the typical size of a high-resolution photograph, while other transfers were more commensurate with the expected size for video files.
Sergeev’s data usage persisted throughout his stay in London, suggesting his phone was with him the whole time and he did not take (long) trips that could not be matched via connections to cell-tower locations. For example, during the night of 2nd to the 3rd of March, we can see non-trivial data volumes at 3 am to 4 am, as well as large file transfers (or video/VOIP calls) between 4:30 and 6 am London time, which would match the start of the working day in Moscow, given the three-hour time difference in March.
“Amir from Moscow”
During his trip, Sergeev made and received regular phone calls from only one telephone number. This was the same number he called just before flying from Moscow, and he communicated with this contact a total of 11 times during the London trip.
We have established that as of press-time, this number is “unregistered”, i.e. belongs to a prepaid sim-card without a documented owner. However, given that Russian mobile operators are obliged to activate sim cards only linked to individuals (or companies), and as of June 2018 they must require passport identification of number owners – or else disconnect them – this number appears to be non-standard. In addition, metadata logs show that this telephone number does not produce the regular “footprint” left by regular numbers: i.e. there are no cell-tower IDs, or IMEI/IMSI logs matching this number. It is thus likely that this is a number from a special series used by Russian’s security services, and it is possibly not linked to a hardware telephone but – for instance – to a gateway device.
The number shows up in one telephone-sharing app popular in Russia under the name “Amir – Moscow”.
Screenshot from GetContact, a popular phone-number sharing app
Sergeev first called this number shortly after checking into his hotel near Paddington station on March 2. He had another short call with “Amir” an hour later, and then a longer 9-minute call 8:49 pm.
Saturday, 3 March
The next morning Sergeev received two phone calls from the same number shortly after 9 am, and two calls again after 15:45.
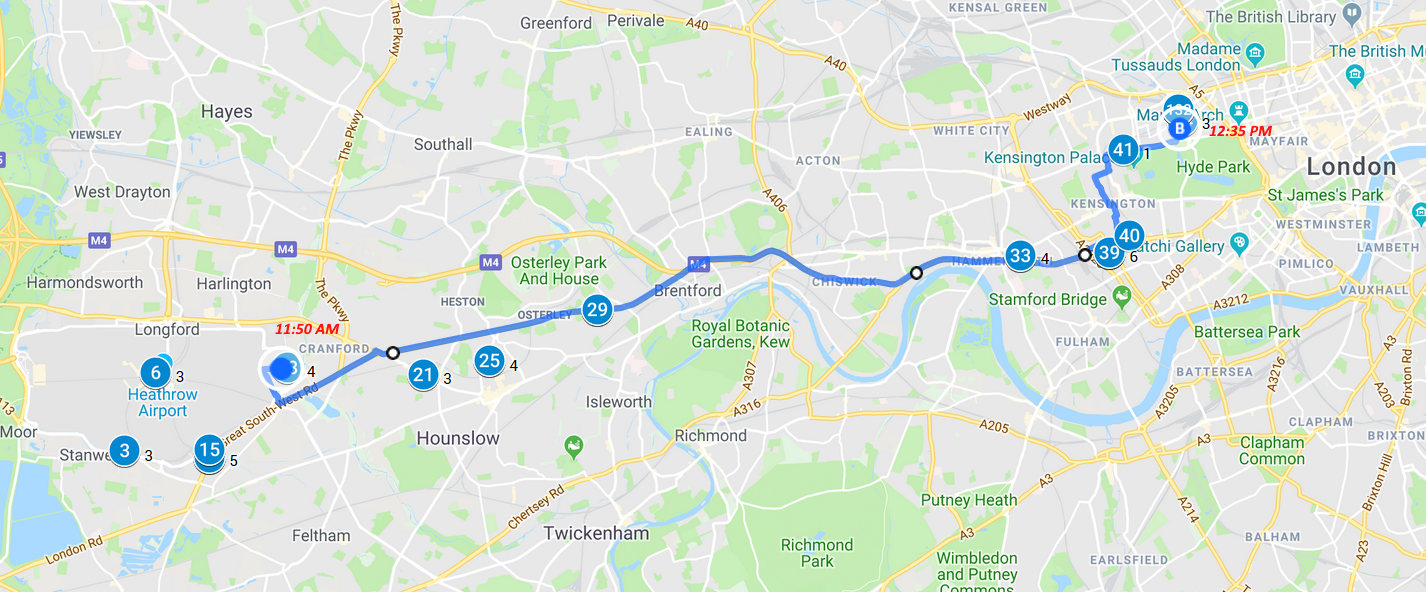
Between the two calls, Sergeev took at least one trip outside the hotel. Between 11:30 and noon, his phone registered at least once at a cell tower near Oxford Circus. Then, between noon to about 1:30 pm, his phone connected several times near the Embankment, on the Thames west bank.
Notably, according to the timeline of Chepiga and Mishkin’s movements, as presented by British police, they arrived from their hotel to Waterloo station at approximately 11:45 on that day. Their train to Salisbury, however, would have left at 12:50. Waterloo station is approximately 10 minutes walk from the Embankment. Thus, had a meeting in person been necessary between Sergeev and the Chepiga/ Mishkin team – whether to pass on final instructions or a physical object – the area between the Embankment and the Waterloo would have been a convenient place, and the one-hour time gap between their arrival to the station and their departure would have likely sufficed.
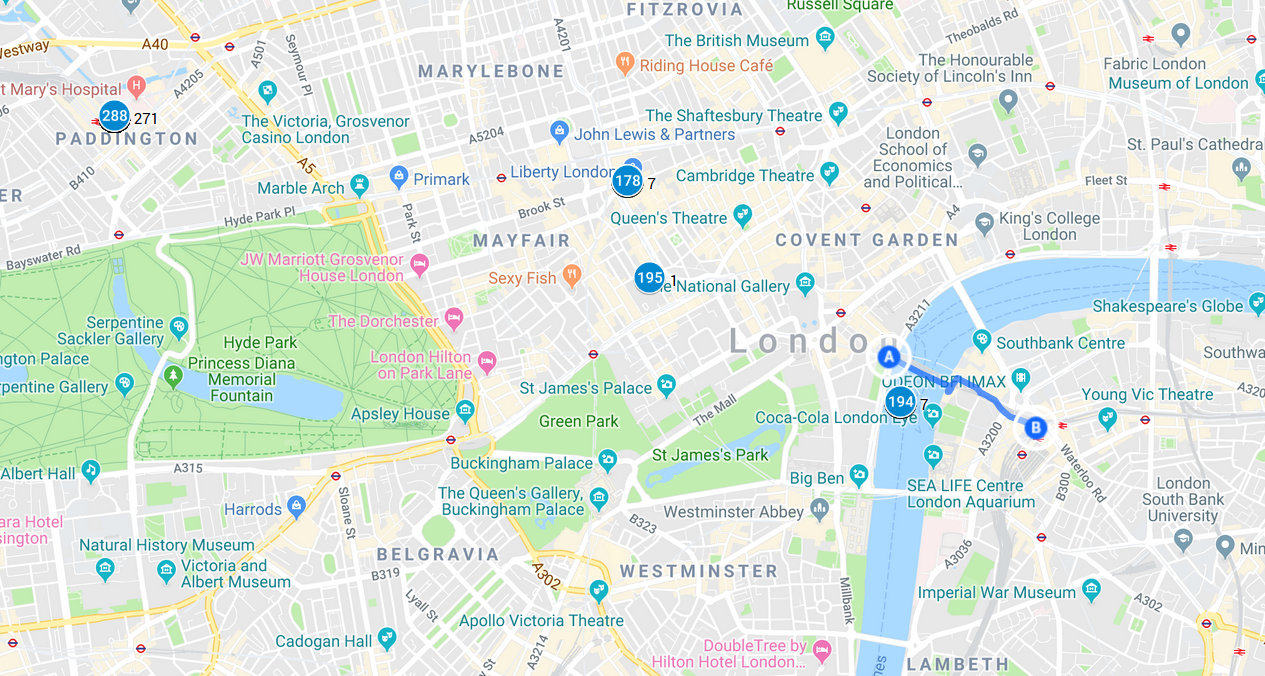
Sergeev’s movements on March 3. He spent most of the day at his hotel (271 connections), with a short trip to Oxford circus and a longer stay at the Thames. The blue line shows the walking distance between the Embankment and Waterloo
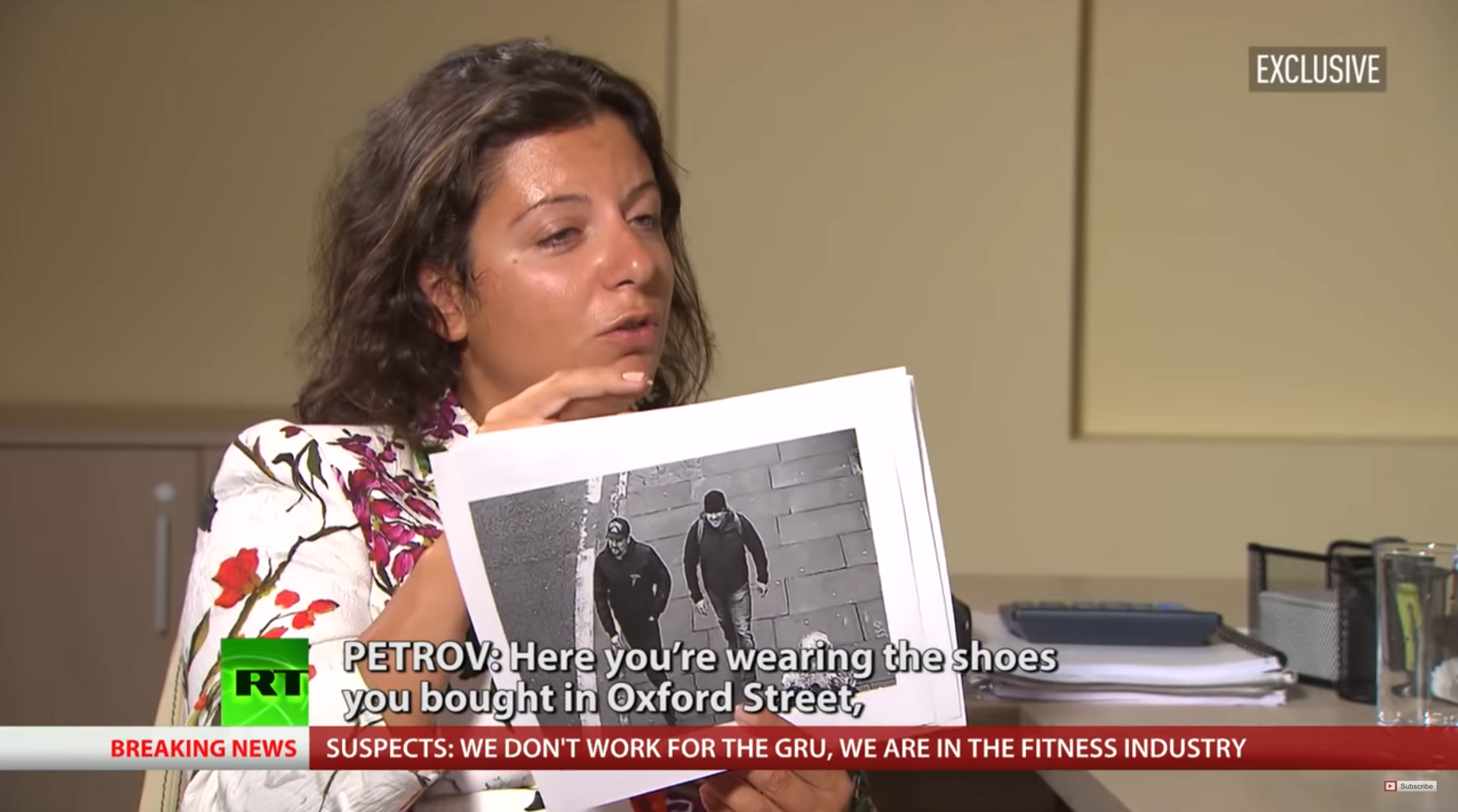
Sergeev’s detour to Oxford Circus may or may not be significant. In their infamous RT interview, Chepiga and Mishkin, masquarading as tourists Boshirov and Petrov, claimed that on March 3 they visited a shop at Oxford Street. However, they said they shopped for sneakers at Oxford street after their return from Salisbury, whereas Sergeev’s connection is from the morning before their trip. However, it is possible that Oxford Street was used as a point of brush-off meeting, or a fallback to another place of meeting.
Timeline of Mishkin/Chepiga movements, per UK police
| 2018-3-2 15:00 | Gatwick arrival | |
| 2018-3-2 17:40 | Victoria station | |
| 2018-3-2 18:00 | Waterloo | |
| 2018-3-2 19:00 | Waterloo | |
| 2018-3-2 19:00 | CityStay Hotel | |
| 2018-3-3 11:45 | Waterloo | *departing Waterloo 12:50 |
| 2018-3-3 14:25 | Salisbury Station | |
| 2018-3-3 16:10 | Salisbury Station | |
| 2018-3-3 20:05 | CityStay Hotel | |
| 2018-3-4 8:05 | Waterloo | *departing Waterloo 10:20 |
| 2018-3-4 11:48 | Salisbury Station | |
| 2018-3-4 11:58 | Skripal house | |
| 2018-3-4 13:05 | Salisbury Fisherman street | |
| 2018-3-4 13:50 | Salisbury Station | * left at 15:10 |
| 2018-3-4 16:45 | Waterloo | |
| 2018-3-4 18:30 | Underground to Heathrow | |
| 2018-3-4 19:28 | Passport control | |
Just after 6 pm, Sergeev received two more calls from “Amir”, totaling about 4 minutes. Based on the police timeline, suggesting Chepiga and Mishkin left Salisbiry just after 4 pm, by the time of the call the pair would have just returned from their first trip to Salisbury.
Sunday, 4 March. Day of the Poisoning.
On the morning of March 4, Fedotov made several data connections from his Paddington hotel. At 9:03 AM his phone rang, and he spoke with “Amir” for just about a minute. At 10:20 he sent or received a file of 8 MB, commensurat with a photo file. Notably, at that same moment, the Chepiga/Mishkin team left by train from Waterloo to Salisbury.
At 10:40 Sergeev called “Amir” one last time, and spoke with him for about 2 minutes. He continued using the internet until 11, when he checked out of the hotel. He had a scheduled flight out of Heathrow at 13:30, and he was already running late.
At 11:20 Sergeev went offline and reappeared near Southhall on the way to Heathrow airport 30 minutes later. This route and timing would be consistent with him taking the 11:25 AM Heathrow Express from Paddington. He arrived at Heathrow’s Terminal 4 just before 12 pm. Fortunately for him, Aeroflot’s flight – once again – was late. He made the flight, and the plane to Moscow took off at 14:15.
As Sergeev’s plane was about to land, “Amir” tried to call him at 8:51 PM, and when he could not reach him, sent him a text message. Sergeev landed at 21:00, checked his online messengers for messages, and left for his home by car. Once at his home, at 22:35 he made a brief 10-second call to “Amir”. He then stayed browsing the internet until 4 in the morning.
Relevance of new findings
The new findings confirm that Sergeev was an active GRU officer at the time of the Salisbury operation, as opposed to a retired officer employed for a private operation. They also shed light on the likely chain of command for this (and other) GRU overseas operations, with one coordinating senior officer communicating with headquarters in Moscow while the team on the ground receive limited to no new instructions. This set-up may be linked to operational security and the need to minimize the operative team’s exposure to traceable data communications. Evidence obtained by us on other international operations involving the same team suggests that this is a stable GRU oprerational model.
The new telephone metata data also provides an answer to a mystery unresolved in our prior investigation relating to Sergeev: his mysterioius check-in and later “de-boarding” entry from the passenger list. Given the late departure from his hotel and delayed arrival at Heathrow, it is plausible that by the time he went through security control, the airline had already excluded Sergeev from the passenger list. Assuming he had an electronic boarding pass on his phone, he would have been able to make his way to the gate and – given the delayed flight – “begged” his way back in to the checked-in passenger list. This would still leave open the question as to why, upon arriving to Moscow, he declared to border officials that he was landing from Rome, instead of London. The latter might have been out of caution given the sensitivity of his operation.
While we cannot validate from objective sources the finding by our reporting partner BBC Newsnight that Denis Sergeev has a rank of Major General, it is consistent with our own assessment, given his prior military achievements and seniority. The involvement of a GRU Major General would indicate the unusually high importance of the operation.