I write about cybersecurity for The Associated Press, but like other reporters I pitch in on other investigative tracks too. That includes occasional forays into covering the fallout from Russia’s 2016 election interference. On Monday, I published a story on Joseph Mifsud, the enigmatic Maltese academic who is alleged to have dropped publicly known hint of Russian interference in the 2016 vote. Mifsud has since gone to ground and, while I couldn’t locate him, I did speak to his lawyer, whose office supplied me with a photo of the man.
The picture shows Mifsud in what appears to be an office somewhere, wearing a white collared shirt and clasping a pen in his right hand, looking up at the camera with a serious, slightly quizzical look. On the table: a signed power of attorney document and the May 17 edition of Zurichsee-Zeitung, a Swiss-German newspaper. Also on the table, off to the side, is what appears to be a copy of the Democratic National Committee’s lawsuit against the Russian government, WikiLeaks, the Trump campaign, and many others (including Mifsud) resting under a pair of eyeglasses. It’s just barely visible, but Mifsud’s name appears to be highlighted in pink. On a chair to Mifsud’s right is a dark blazer and a stylish attache case.
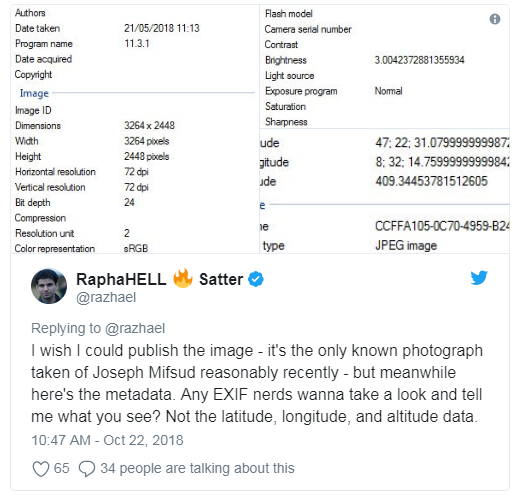
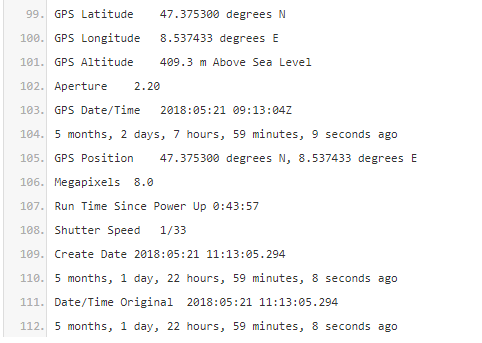
Stephan Roh, Mifsud’s lawyer, said he was providing me with the image for verification purposes and asked me not to publish it. His office suggested I look at the EXIF to verify that the photo was in fact taken in Zurich (and not, for example, in Moscow.) So I did. EXIF data (the acronym stands for Exchangeable File Image Format) is far from cast-iron; it can pretty easily edited. But it’s always worth examining. In this case, the photographer seems to have made things easy. GPS data embedded in the EXIF suggested the picture was taken with an iPhone at 47.375300 North, 8.537433 East and 409.3445378 meters above sea level. The website LatLong.net gives Zurich’s coordinates as 47.376888 North and 8.541694 East; “The Book of Cities”gives its altitude as 408 meters. I found the EXIF timestamp, around noon on May 21, 2018, consistent with the newspaper on the table (even if the paper was by then five days old.) Satisfied with a cursory verification, I included a brief reference to the metadata in my story.
But soon after publishing I learned that the EXIF data can be mined for much more — and the folks at Bellingcat have shown, once again, that crowdsourcing is a fantastic way of seeking help. Within minutes of the open source experts picking up my request for help, users were cross-referencing version histories, poring over the brightness levels and even counting the number of pixels to see what kind of an iPhone had shot the picture.
My appeal for help that was rebroadcast by Bellingcat (I misspelled “note”)
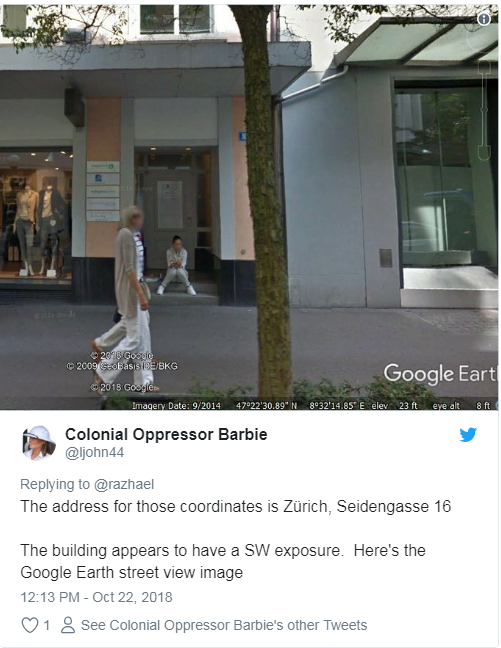
One user geolocated the photo to downtown Zurich; another provided an address that was only one door down from Roh’s law firm.
This was very close; the law firm’s address is Seidengasse 15
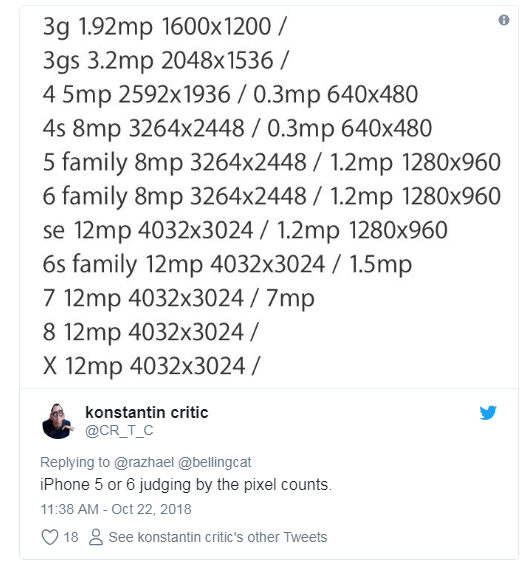
A third user picked up on the program name, 11.3.1, and said it was a reference to iOS 11.3.1, an update to the iPhone’s operating system that was released on April 24, 2018 — a month before the photo’s date. (iOS 12, the operating system’s next iteration, was released in September.) So far, so logical. But a verification trick that was new to me was using pixel counts to determine the iPhone model.
The size of some images can be used to reverse engineer smartphone model numbers
The EXIF data did in fact identify the camera as an iPhone 6, although I didn’t post that until a few minutes later.
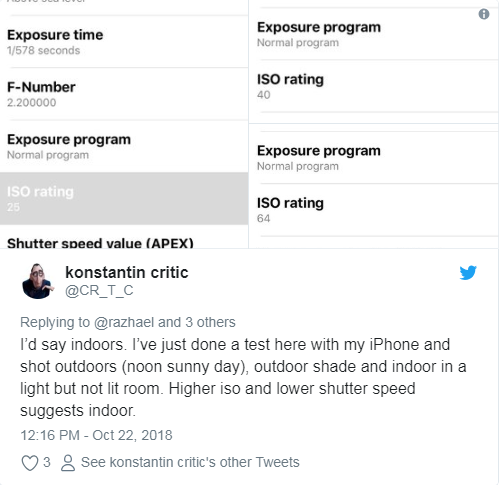
Pixel counting is clever, but this user really impressed me when we got to arguing about whether the brightness of the light recorded in the EXIF data made sense. A fifth user said the f-stop (2.2) shutter speed (1/33) and ISO (100) suggested that the photo was taken outdoors — which obviously isn’t consistent with the indoor (albeit well-lit) shot of Mifsud that I had. So the pixel-counter ran an experiment:
Nothing beats a field test
A sixth user referred us to a digital photography website to buttress the point. And, just to make sure, the user who’d matched the coordinates to the Seidengasse address checked the weather that day around noon. It was sunny.
A seventh user pointed me to a site I didn’t know existed: Jeffrey’s Image Metadata Viewer. The site is useful for extracting EXIF data from photos which I eventually did here (note that I painted over the entire image in black before uploading it, which explains the reference to Paint.net in the metadata.)
A selection of EXIF data extracted using Jeffrey’s Image Metadata Viewer:
I learned a lot from this brief crowdsourcing episode— and I hope this will be useful for other EXIF sleuths. Meanwhile, if you have other photos of Joseph Mifsud, please send them my way.
This article was first published to Medium and is being reprinted here with permission. The author has no affiliation with Bellingcat.